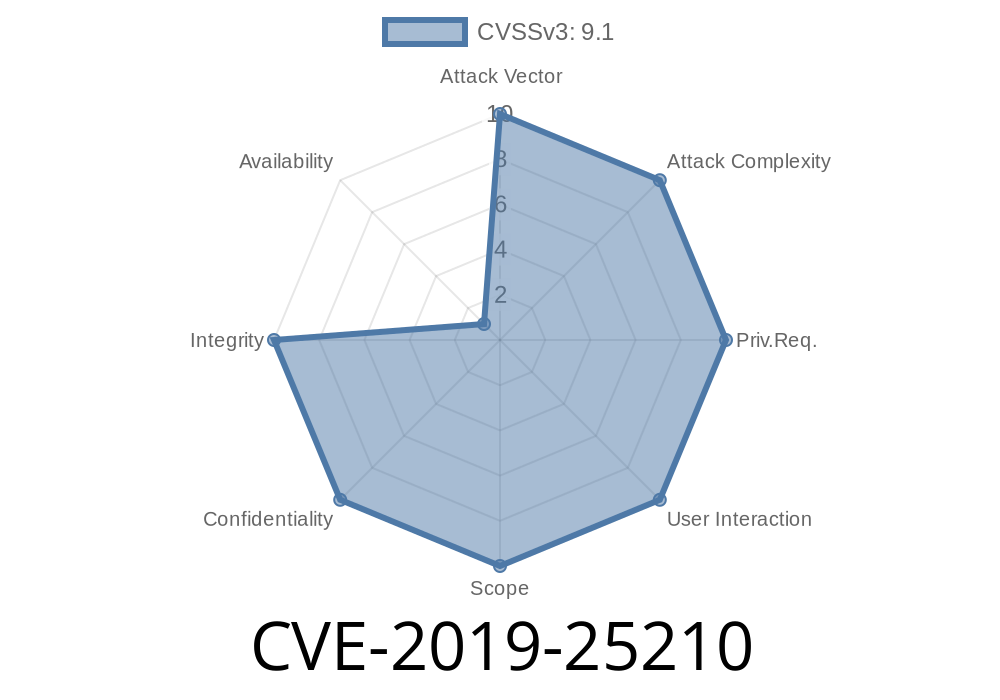
In February 2021, a security issue surfaced in Helm, the de facto package manager for Kubernetes, tracked as CVE-2019-25210. The vulnerability affected all versions of Helm up to 3.13.3 and involved an unexpected leak of secrets when using the --dry-run flag—a feature commonly used in automation and CI/CD pipelines. This post breaks down what happened, how it can impact your deployments, and what you should do to keep your secrets… well, secret.
What Is CVE-2019-25210?
CVE-2019-25210 is a security concern discovered in the Cloud Native Computing Foundation (CNCF) Helm project. When deploying manifests with Helm, you may use the --dry-run flag to simulate what will happen—without actually making changes in your cluster. The bug? If your values.yaml (or similar input files) contains secrets, Helm displays them in its output, even though nothing is deployed.
Consider this
- You use Helm's --dry-run flag in a CI/CD tool.
The tool echoes output to a log, accessible to developers, testers, and maybe even the public.
- Secrets, passwords, access tokens, or similar sensitive values might be printed in clear text to the log.
When running
helm install my-app ./my-chart --dry-run
Helm merges values from values.yaml and user input. If a value like apiKey is present, for example:
values.yaml
apiKey: "super-secret-key-123"
The dry run output (either as text or YAML, depending on your flags), includes
# Source: my-chart/templates/secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: my-app-secret
type: Opaque
data:
apiKey: c3VwZXItc2VjcmVLWtleSxMjM= # base64 encoded "super-secret-key-123"
Any script, person, or automated system with access to this output can recover your secrets.
Here’s a simple Python script that could “scrape” secrets from dry-run outputs in log files
import re
import base64
with open("dryrun-output.log") as f:
content = f.read()
matches = re.findall(r"apiKey:\s([a-zA-Z-9+/=]+)", content)
for b64_secret in matches:
try:
print("Decoded secret:", base64.b64decode(b64_secret).decode())
except Exception as e:
pass # Not a base64 string or decoding failed
Why Is This a Security Issue?
Using --dry-run is a *testing tool*. You expect it to be safe, but when secrets go out in the open, several bad things can happen:
- Accidental Leaks: Teams might copy/paste outputs or store logs insecurely.
- CI/CD Exposure: Automated pipelines might expose logs to too many eyes.
Vendor's Position
The Helm maintainers have stated:
> “This is intentional and unavoidable without breaking backwards compatibility. Helm as a tool will output everything the rendered templates contain, and it's up to users to ensure that this output isn’t sent somewhere unsafe. Many users rely on this output for template debugging, including for secrets.”
Helm will not fix this issue—removing secrets from dry-run output would break other workflows.
- Responsibility is on the user: If you choose to run Helm dry-runs in an insecure context, you accept the risk.
References
- Original Github Advisory
- CVE detail CVE-2019-25210
- Helm Docs - Security
Don’t store or output dry-run logs publicly.
- Avoid running --dry-run for secret-heavy charts in CI/CD systems unless outputs are tightly controlled.
`sh
helm install my-app ./my-chart --dry-run | egrep -v 'apiKey|password|accessToken'
`
- Use Kubernetes External Secrets or providers like Sealed Secrets to avoid putting raw secrets in your manifests at all.
Helm will not change this. As a user, it’s on you to protect sensitive output.
- Review your CI/CD and manual practices: Where is your dry-run output going?
- Treat --dry-run output as sensitive if secrets are present—clean up logs, add access controls, or avoid using it with secrets.
Additional Resources
- CNCF Helm Security Docs
- Helm Github Issue on secrets
- Kubernetes Secrets Best Practices
Stay safe, and always double-check what gets printed—your secrets could be just a --dry-run away from exposure!
Timeline
Published on: 03/03/2024 21:15:49 UTC
Last modified on: 09/04/2024 18:35:00 UTC