In June 2022, a subtle but serious flaw was found in Linux’s kernel debugging tools, KGDB and KDB. At first glance, it may seem unlikely that a local hardware port could threaten a system’s confidentiality, integrity, and availability—even with lockdown in place. However, CVE-2022-21499 highlights exactly how this can happen, giving attackers a bridge straight into kernel memory.
The Tools: KGDB and KDB
KGDB (Kernel GNU Debugger) and KDB (Kernel Debugger) are critical for Linux kernel development, allowing devs to step through code, set breakpoints, and inspect memory directly inside the running kernel.
KDB is a lighter in-console debugger for quick troubleshooting.
Lockdown Mode is supposed to prevent even root from changing protected kernel code and memory, making system compromise much harder. But…
The Vulnerability
Sometimes, kernel lockdown can be bypassed. CVE-2022-21499 reveals that if an attacker can access a machine’s serial console, they might be able to trigger KGDB/KDB and get unrestricted access to kernel memory, even in lockdown mode.
> Key Issues:
> - KGDB/KDB did not check lockdown state before handling access or critical commands.
> - Attackers with serial port access can trigger debugger mode and dump/modify memory.
What does this mean? Regardless of how secure or restricted your software is, if attackers can plug in to a serial port (physical or virtual), they may get read/write kernel access. That’s game over for confidentiality, integrity, *and* availability.
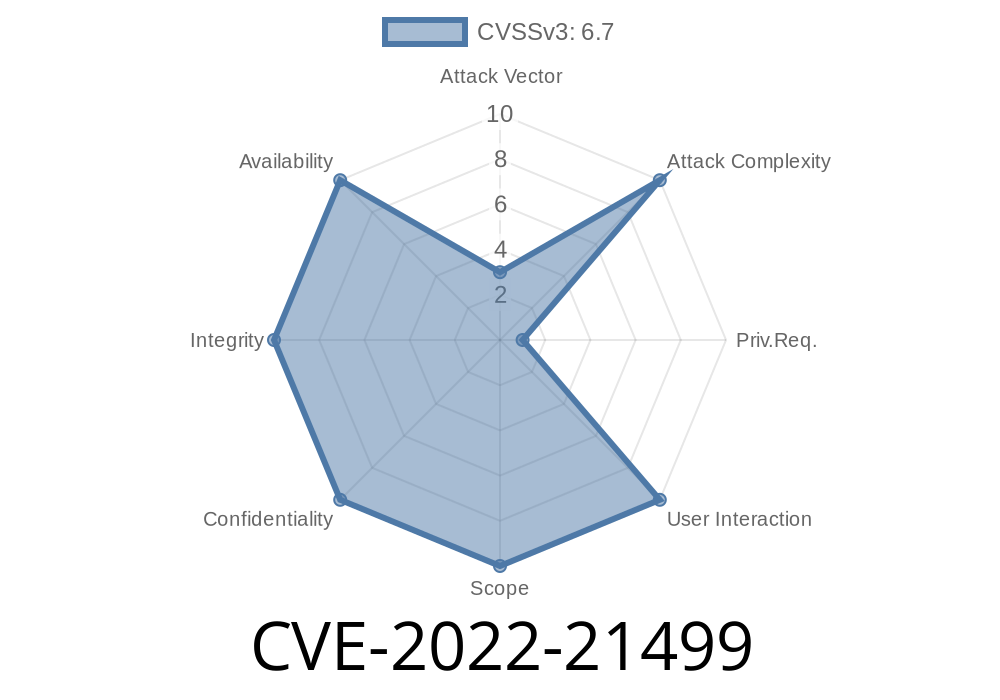
Impact
The CVSS 3.1 score is 6.5, meaning this is a high-severity local flaw. Here’s the vector:
Exploit Details
Let’s see what a typical exploit looks like. This isn’t a remote hack: You need access to the console—but don't underestimate how many virtual servers (especially cloud/dev boards) accidentally expose their “console” to admin panels, VNC, or accessible UART pins!
Trigger KDB — often, this is via a key sequence (like sending a "break" signal)
3. Issue memory commands: Tell KGDB/KDB to dump memory, change kernel code/data, or otherwise bypass kernel lockdown.
> #### Example KGDB Session Over Serial Port (Code Snippet)
# Attacker connects to serial console as root (lockdown enabled)
# Send <Ctrl+C>, or special break sequence to enter KDB/KGDB.
Sending: <Magic SysRq> g
# Now inside KDB prompt:
kdb> md xffff880b780000 # Dump memory at kernel address
kdb> mm xffff880b780000 xBADCDE # Modify kernel memory
# Can now patch kernel, dump data, or force a panic/reboot
Note: Normally, these commands would be locked *out* by lockdown, but here, the debugger happily accepts them.
Is this a Real-World Risk?
- Are your servers colocated, or do others have rack/board access?
Are dev boards or IoT systems in risky environments?
If so, this is your risk. Many cloud providers or server admins leave serial ports or virtual consoles less protected, thinking only “remote network” attacks matter.
Remediation and References
Fixes are available. As of late June 2022, kernel patches have landed to block KGDB/KDB if kernel lockdown is active. Always update to the latest stable kernel.
Some links for in-depth details
- CVE Record at NVD
- Kernel patch on LKML
- Oracle Security Advisory for CVE-2022-21499
- Red Hat Security Advisory
Update your kernel: Anything newer than mid-2022 should be good.
- Audit lockdown: Make sure nothing can trigger KGDB/KDB if lockdown is on.
Conclusion
CVE-2022-21499 reminds us that *hardware access is just as dangerous as network vulnerabilities*—and that lockdown must apply everywhere, even deep inside the debug tools. Never trust the serial port, and keep your kernel up to date.
> If you’re running Linux in production, especially on virtual or physical servers with exposed consoles, check your kernel version and lockdown settings. A single port can be your weakest link.
Timeline
Published on: 06/09/2022 21:15:00 UTC
Last modified on: 06/17/2022 14:55:00 UTC