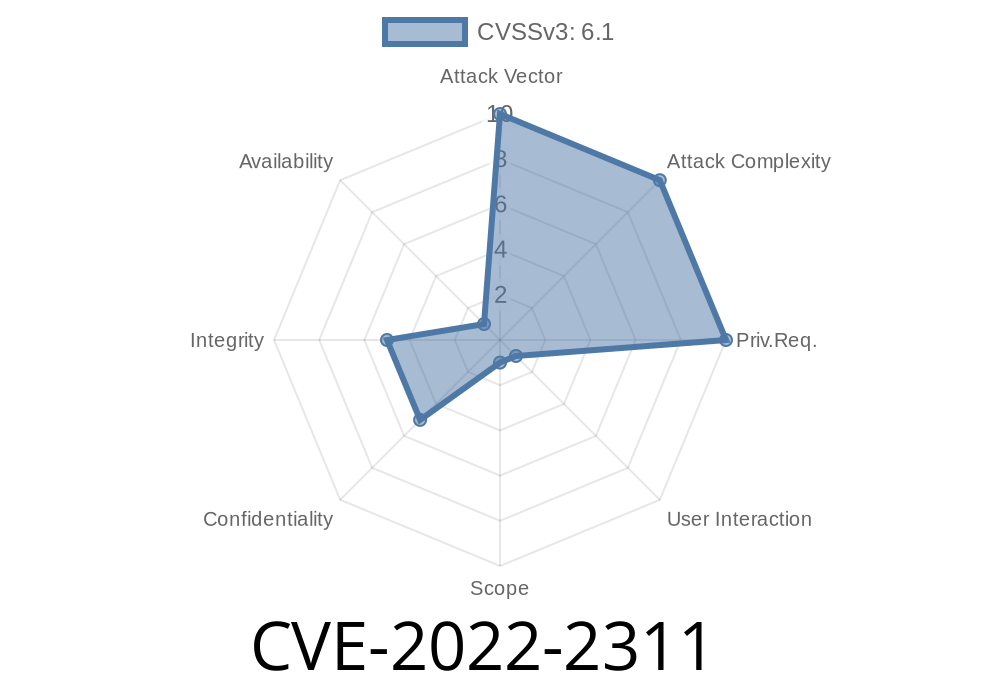
In July 2022, a security vulnerability was discovered and documented under the identifier CVE-2022-2311. This issue affects the popular Find and Replace All WordPress plugin in all versions prior to 1.3. Due to improper sanitization and escaping of some parameters on its settings page, the plugin became vulnerable to a Reflected Cross-Site Scripting (XSS) attack. This long-read explores the underlying cause, exploit scenario, and preventive strategies for CVE-2022-2311, using real code snippets and references.
What Is Reflected Cross-Site Scripting?
Reflected XSS happens when user-supplied data is immediately included in the application's response without proper sanitization or escaping. Attackers can exploit this to inject malicious JavaScript, which executes in the context of the victim’s browser. The critical point about this type of XSS is that the malicious input needs to be delivered by the attacker—usually via a link.
About the Find and Replace All Plugin
Find and Replace All is a plugin made to let admin users search and replace text across the entire WordPress website, including posts, pages, and comments.
Technical Details
In versions prior to 1.3, the Find and Replace All plugin takes parameters from user input on its settings page and outputs them directly without proper sanitization or escaping. If an attacker can trick a legitimate user (especially an admin) into clicking on a specially crafted URL, they can execute arbitrary JavaScript code in the user’s browser.
Let’s look at some hypothetical (but realistic) PHP code, simplified for clarity
<?php
// Example: plugins/find-and-replace-all/admin.php
if (isset($_GET['notice'])) {
// The plugin directly echoes the 'notice' parameter.
echo '<div class="notice">'.$_GET['notice'].'</div>';
}
?>
There is no htmlspecialchars() or any other escaping applied to $_GET['notice'].
Assume a victim is logged into their WordPress admin panel and visits the following crafted URL
https://example.com/wp-admin/options-general.php?page=find-and-replace-all¬ice=<script>alert('XSS')</script>;
The plugin reads the notice parameter from the URL.
- It outputs <script>alert('XSS')</script> inside the page.
Try visiting
https://yoursite.com/wp-admin/options-general.php?page=find-and-replace-all¬ice=%3Cscript%3Ealert('XSS')%3C%2Fscript%3E
If you are using a vulnerable version, you will see a popup. Malicious actors can replace the alert with code that steals your admin cookies or performs actions on your behalf.
Impact
Since this page is only accessible to authenticated users (like site admins), attackers need to trick privileged users. Still, successful exploitation can lead to:
# Fix
Version 1.3 and above of the plugin properly escape user input using WordPress’s escaping functions. Always sanitize and escape outputs with functions like esc_html(), esc_attr(), or native PHP’s htmlspecialchars().
Secure Code Example
<?php
if (isset($_GET['notice'])) {
echo '<div class="notice">'.esc_html($_GET['notice']).'</div>';
}
?>
Now, if the input contains any HTML or JavaScript, it will be displayed as plain text.
References
- Original CVE Record - CVE-2022-2311
- Plugin Details on WP.org
- Patchstack Writeup
- OWASP XSS Overview
Conclusion
CVE-2022-2311 highlights a common pitfall in plugin development: unsanitized input in admin pages. While reflected XSS on such pages may seem less dangerous, the stakes are much higher due to admin privileges. If you use Find and Replace All, upgrade immediately. As a general rule, always validate and escape user data—especially when building for WordPress.
Timeline
Published on: 11/28/2022 14:15:00 UTC
Last modified on: 11/30/2022 03:40:00 UTC