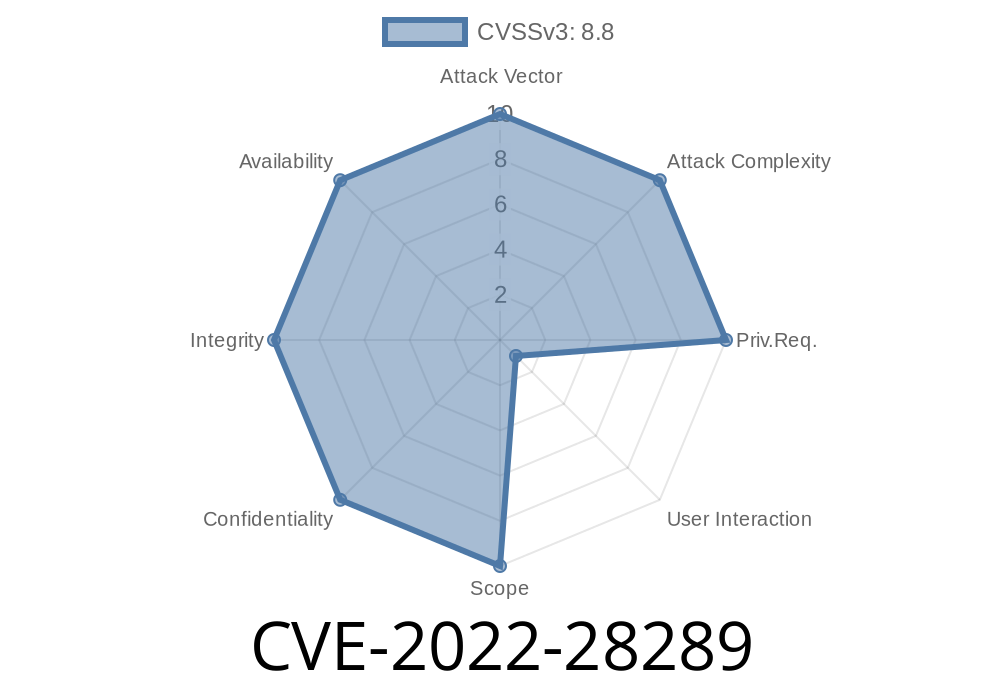
In March 2022, a notable vulnerability titled CVE-2022-28289 was reported in Mozilla’s popular software: Firefox, Firefox ESR, and Thunderbird. It wasn’t just a minor bug—this issue raised concerns about possible arbitrary code execution. Let's break down what happened, how it works, and what you can do about it.
What Is CVE-2022-28289?
Developers and fuzzing (automated testing) experts at Mozilla, including Nika Layzell, Andrew McCreight, Gabriele Svelto, and the Mozilla Fuzzing Team, discovered several memory safety bugs in Thunderbird version 91.7. After investigation, they realized these bugs affected not only Thunderbird but also Firefox < 99 and Firefox ESR < 91.8.
Some of these bugs showed *evidence* of memory corruption. While Mozilla’s team didn’t confirm a working exploit, they believed that, with enough effort, attackers could trigger these bugs to run arbitrary code—meaning malware, spyware, or other unwanted programs.
Why Is Memory Safety Important?
Memory safety is about making sure a program doesn’t read or write outside the bounds of memory it’s supposed to use. If this safety is broken, attackers can trick the program to run malicious code, steal information, or even take over your computer.
A Technical Dive: How Could the Exploit Work?
Here’s a simple example: Imagine a C++ function in the browser's rendering engine that allocates an array for processing network data. Due to a bug, the software allocates less memory than needed.
char data[10];
memcpy(data, user_input, 100); // Unsafe: user_input may be longer than 10 bytes!
In this case, if an attacker sends a specially crafted message (say, a giant email to Thunderbird or a weird web page to Firefox) that’s longer than 10 bytes, it can overwrite the memory beyond data. That area could include crucial program data or pointers to executable code.
With precise crafting, the attacker could make the browser execute their code. That’s how a memory corruption bug like CVE-2022-28289 can turn dangerous.
Mozilla Firefox ESR (Extended Support Release) versions earlier than 91.8
If you’re using any of these, you’re at risk. Attackers could target you by emailing you a malicious message (for Thunderbird) or luring you to open a toxic web page (for Firefox).
How Was the Bug Found?
Mozilla’s Fuzzing Team: They use “fuzzers”—tools that send random, unusual, or purposely broken data to software on a loop—to uncover unpredictable side effects. When the software crashes or starts acting weird, that’s a clue.
They noticed that special crafted inputs in the code path could make the program misbehave, hinting at memory problems.
References and Further Details
- Mozilla Security Advisory: 2022-12
- CVE Entry at MITRE
- NVD - CVE-2022-28289
Real-World Exploitation (Proof of Concept)
No public working exploit was shared by Mozilla, but here's a generic approach an attacker might take:
1. Craft a large, weirdly-formatted email (for Thunderbird) or a web page (for Firefox) with unusual data fields.
Trigger the processing code that mishandles memory.
3. Overwrite nearby memory to hijack the execution path—possibly running their own malicious shellcode.
Here’s a simplified *pseudo-exploit*
// For Firefox: a web page with massive, oddly named form fields
let hugePayload = "A".repeat(10000); // Create a giant string
form.appendChild(new Input('text', hugePayload)); // Might cause buffer overrun
document.body.appendChild(form);
Important: Actual exploitation would require deep browser internals knowledge and is much more complex.
Firefox ESR 91.8
Make sure you’re running at least these versions.
Conclusion
Memory safety bugs are among the most dangerous because they open the door to all sorts of attacks. CVE-2022-28289 in Firefox and Thunderbird is a textbook example: subtle, hard to spot, but potentially devastating.
Stay safe—always keep your browsers and email clients updated. And thank Mozilla’s security folks for finding and fixing these before the bad guys do!
More Reading
- Mozilla Release Notes for Firefox 99
- Thunderbird 91.8 Release Notes
*Stay updated—and tell your friends to update, too!*
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/30/2022 20:42:00 UTC