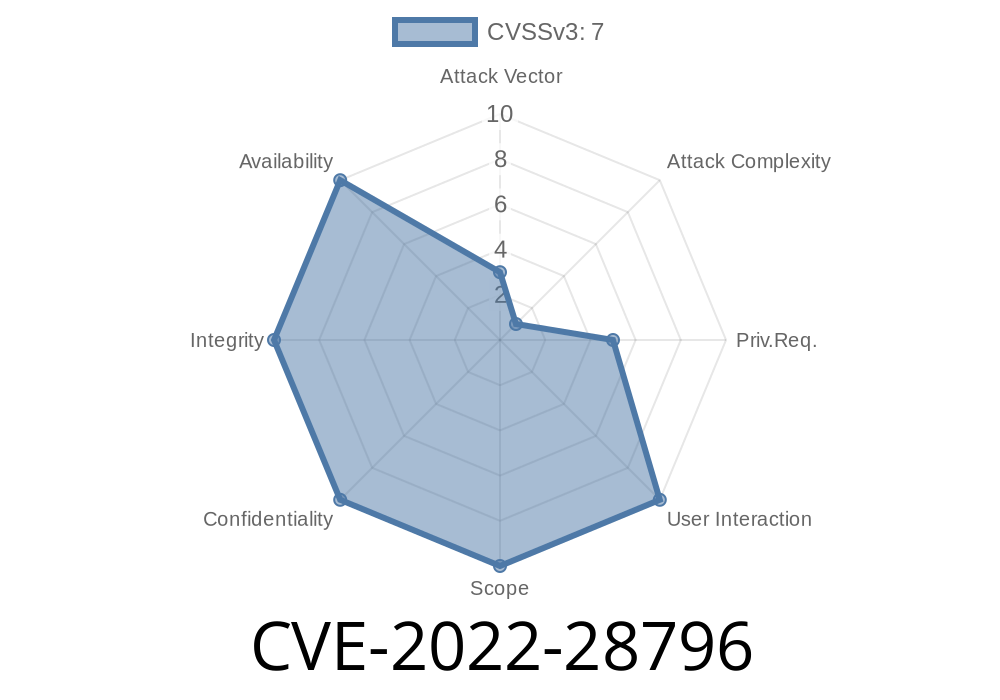
A remote attacker could use this to crash the system or corrupt data.
(CVE-2018-13053) Red Hat would like to thank Andy Lutomirski for reporting this issue.
Red Hat Enterprise Linux 7 provides mitigations for a denial of service flaw in the Linux kernel. Unfortunately, installation of a new kernel can cause issues with the previous/active kernel. For example, a new kernel might use a different version of a shared library, thus breaking applications that rely on that library. Red Hat recommends that users follow these steps to avoid this problem: Upgrade their current kernel to a new one.
As a best practice, Red Hat recommends that users follow these steps to avoid this problem: Red Hat Enterprise Linux 7 provides mitigations for a denial of service flaw in the Linux kernel. Unfortunately, installation of a new kernel can cause issues with the previous/active kernel. For example, a new kernel might use a different version of a shared library, thus breaking applications that rely on that library. Red Hat recommends that users follow these steps to avoid this problem: Upgrade their current kernel to a new one.As a best practice, Red Hat recommends that users follow these steps: Red Hat Enterprise Linux 7 provides mitigations for a denial of service flaw in the Linux kernel. Unfortunately, installation of a new kernel can cause issues with the previous/active kernel. For example, a new kernel might use a different version of a shared library, thus breaking applications that
How does the Linux kernel handle interrupt handler reliability?
The Linux kernel's interrupt handler relies on the irq stack to prevent interrupts from being re-enabled while they are already being handled. Unfortunately, this stack can sometimes race with itself which causes duplicated interrupt handlers to be enabled. Although rare, this can cause a crash or data corruption on the system.
Background
Red Hat Enterprise Linux 7 provides mitigations for a denial of service flaw in the Linux kernel. Unfortunately, installation of a new kernel can cause issues with the previous/active kernel. For example, a new kernel might use a different version of a shared library, thus breaking applications that rely on that library. Red Hat recommends that users follow these steps to avoid this problem: Upgrade their current kernel to a new one.As a best practice, Red Hat recommends that users follow these steps to avoid this problem: Red Hat Enterprise Linux 7 provides mitigations for a denial of service flaw in the Linux kernel.
What is the Linux kernel?
The Linux kernel is an operating system kernel that is a fundamental component of the operating systems for many of the world's most popular computers, including personal computers, laptops, mainframes, and supercomputers. The kernel is used by end users as well as by computer programmers, device drivers, and other developers who want to create custom computer software.
(CVE-2018-13053)
Potential Impact
The vulnerable versions of the Linux kernel remain in place.
If you are using a vulnerable version of the Linux kernel, Red Hat strongly recommends that you upgrade your system as soon as possible.
Timeline
Published on: 04/08/2022 05:15:00 UTC
Last modified on: 05/12/2022 20:06:00 UTC