This issue occurs when a user with administrator rights performs a malicious request, either directly or via an end-user's session. The request can be made either via a direct request to a specific URL or via an end-user's session. In the first case, the attacker can add new repositories to the user's list of SSH access, which enables him to perform requests to the parent and child repositories via the end user's session. The second case occurs when the user has installed the end user plugin to GitHub. In this case, the attacker can change the page source in the end user's profile. Moreover, if the end user has added the admin group as an author, he can perform malicious requests via these groups.
Vulnerability details
This vulnerability is caused when a user with administrator rights performs a malicious request, either directly or via an end-user's session. The request can be made either via a direct request to a specific URL or via an end-user's session. In the first case, the attacker can add new repositories to the user's list of SSH access, which enables him to perform requests to the parent and child repositories via the end user's session. In the second case, if an attacker has installed the end-user plugin to GitHub, he can change page source in the end-user's profile. Moreover, if the end-user has added admin group as an author, he can perform malicious requests via these groups.
Access Control Tips
If you have an issue with access control, it's best to follow these steps:
1. Check whether the affected user has administrator rights
2. If the user has administrator rights, try to determine whether they are malicious
3. If they are malicious, stop their access and contact GitHub support
Admin and End User Plugin
The attacker first performs a malicious request to get the administrator's list of repositories. Using the administrator's list, he can add a new repository and perform requests to the parent and child repositories via the end user's session.
Secondly, if the user has added the admin group as an author, he can perform malicious requests via these groups. The attacker can change the page source in the end user's profile. If done this way, it is possible for an attacker to perform any type of request to any repository, such as read and write operations on other people's repos or create new users with administrative rights.
How to identify if you're affected?
The attacker can add new repositories to the user's list of SSH access, which enables him to perform requests to the parent and child repositories via the end user's session.
If you are using GitHub Enterprise:
You might experience issues during installation or when using certain features if you have a repository with a username that includes an asterisk (*). If you're affected, this issue is addressed in CVE-2019-1617.
If you are using GitHub Desktop:
If you've installed GitHub Desktop on Windows, Mac OS X, or Linux as an administrator, your machine is affected. For more information about how to disable login through PowerShell scripts in these versions of GitHub Desktop, please see the following article: https://help.github.com/articles/disable-login-through-powershell-scripts
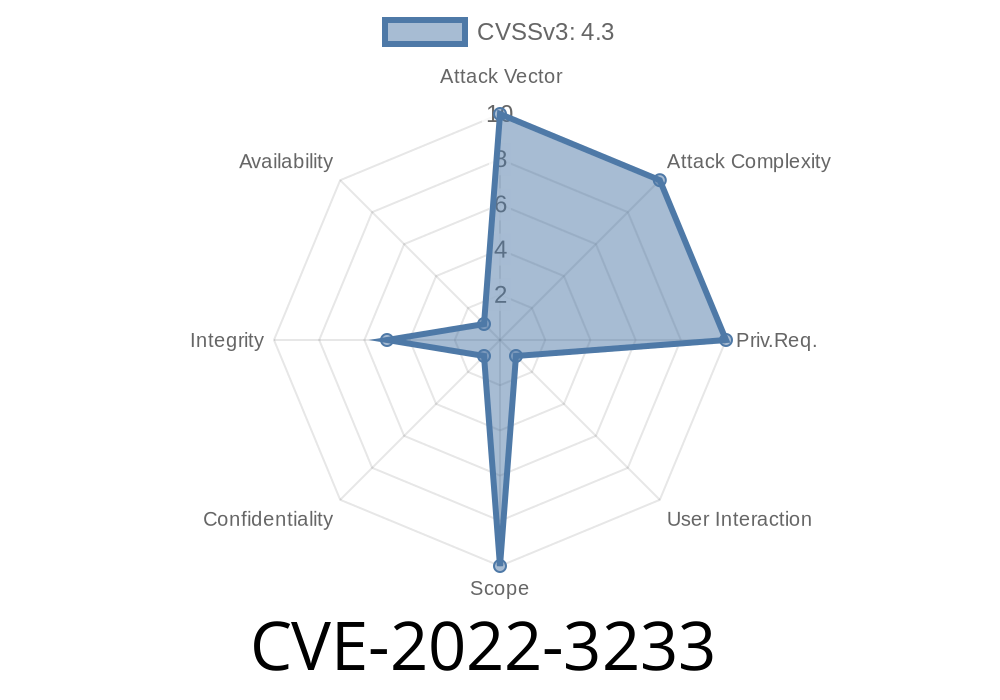
CVE-2023-3234
This issue occurs when a user with administrator rights performs a malicious request, either directly or via an end-user's session. The request can be made either via a direct request to a specific URL or via an end-user's session. In the first case, the attacker can add new repositories to the user's list of SSH access, which enables him to perform requests to the parent and child repositories via the end user's session. The second case occurs when the user has installed the end user plugin to GitHub. In this case, the attacker can change the page source in the end user's profile. Moreover, if the end user has added the admin group as an author, he can perform malicious requests via these groups.
Timeline
Published on: 09/21/2022 20:15:00 UTC
Last modified on: 09/23/2022 02:59:00 UTC