*Published: June 2024
By: Security Insights Team*
What is CVE-2022-32896?
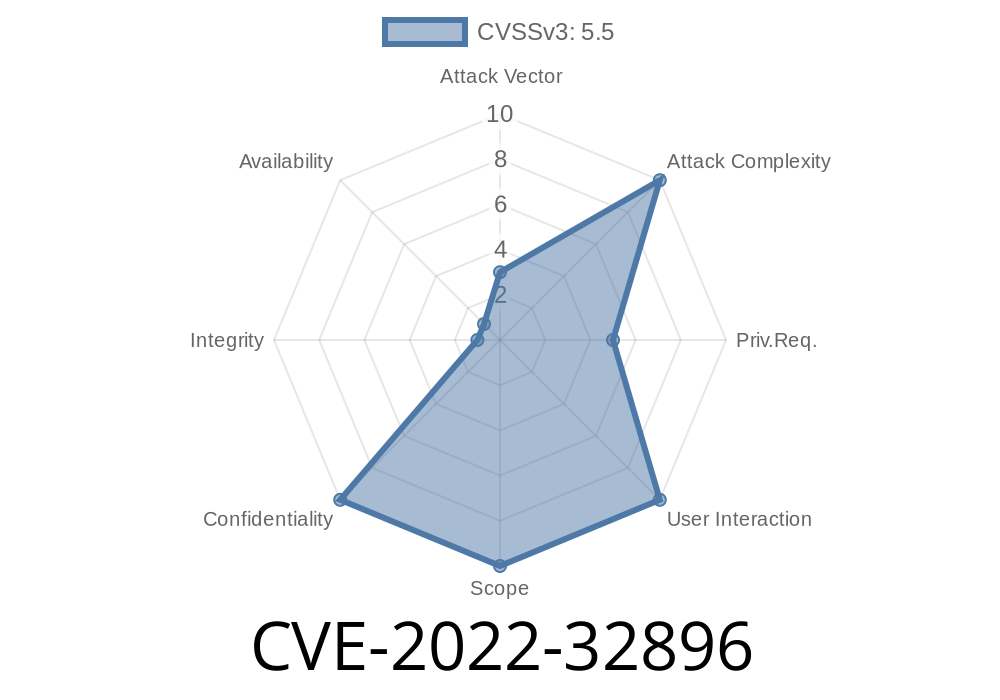
CVE-2022-32896 is a high-impact security vulnerability discovered in Apple’s macOS operating system, specifically in versions before macOS Monterey 12.6 and Big Sur 11.7. This bug allowed a malicious user or program to gain access to sensitive user data, bypassing some important operating system protections.
How Serious is the Threat?
While Apple hasn't published all technical details, the main risk was that someone could access private information from your computer, like documents or browser data, using a specially crafted application or tool.
macOS Big Sur before 11.7
Apple addressed this issue by enabling *hardened runtime* in affected system components, which made it much harder for attackers to use this loophole.
Understanding Hardened Runtime
Hardened runtime is a set of protections in macOS for running apps. When enabled, it limits what code can do by default:
Enforces code signing for all loaded code
Basically, Apple’s fix made sure that key parts of the system would always run with these extra checks on, even if a developer had not enabled them in their own app.
How the Exploit Worked
Before the patch, a malicious or compromised app without hardened runtime could trick the operating system into sharing private user data it shouldn't have. This was possible because the required security checks weren't enforced everywhere.
Example Attack Snippet (Before the Patch)
Below is a simulated, simplified pseudo-code example like what a rogue script might have looked like on unpatched systems:
import os
# Trying to read sensitive Safari data
sensitive_path = "/Users/<username>/Library/Safari/History.db"
try:
with open(sensitive_path, "rb") as f:
data = f.read()
print("[!] Sensitive data found:", data[:128]) # Print first 128 bytes
except Exception as e:
print("Access denied or file not found:", e)
On patched systems, or with hardened runtime enforced, this won't work for unprivileged apps—it will throw an error or return nothing.
How Apple Fixed the Problem
Apple resolved CVE-2022-32896 by simply enforcing hardened runtime by default for system components starting in:
- macOS Monterey 12.6 (release notes)
- macOS Big Sur 11.7 (release notes)
With this, even if a third-party app didn't bother enabling all protections, the system itself would refuse to hand over sensitive data unless all security rules were followed.
Original References
- Apple Security Update for Monterey 12.6
- Apple Security Update for Big Sur 11.7
- CVE-2022-32896 Entry at NIST
- Apple Platform Security: Hardened Runtime
> In short:
> CVE-2022-32896 is a macOS vulnerability fixed by enabling stricter system-wide security checks, making it much harder for apps to spy on your personal data. If you haven't updated yet—now's the time!
Timeline
Published on: 02/27/2023 20:15:00 UTC
Last modified on: 03/08/2023 14:03:00 UTC