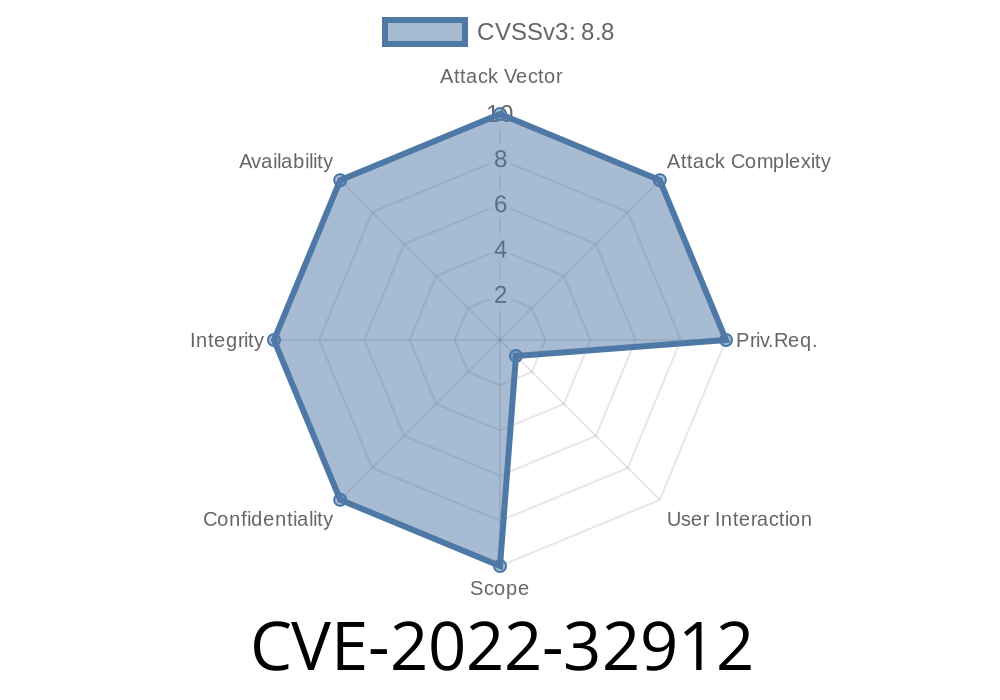
This issue is addressed with improved memory handling. WebAssembly may be enabled in some JavaScript projects, but there is a risk that the imported code is not evaluated in a trusted environment. This issue is fixed in Safari 16, iOS 16, and macOS High Sierra.
To be clear, these are not user-level security issues. Unfortunately, there’s no way to prevent these vulnerabilities from being exploited in the browser without breaking user functionality, especially with sites that users have chosen to trust. To mitigate the risk of these issues being exploited, developers should consider a variety of options.
JavaScript Sandboxing
One option is to use JavaScript sandboxing. This allows developers to compartmentalize code execution by restricting the number of potential values that a given piece of code can evaluate. It also allows developers to limit the set of allowed functions and properties that are available in a given piece of code. Developers can also specify the trusted environment where their code will execute, which will limit the types of operations that can be performed on untrusted data.
While this approach provides some protection against these vulnerabilities and other browser-based attacks, it’s not foolproof. If an attacker manages to circumvent any secure restrictions, they could still run arbitrary code on your system. Additionally, sandboxing has performance implications for many projects as well as a more complex developer workflow.
How do I check if WebAssembly is enabled?
You can check if WebAssembly is enabled in your browser using the following code snippet:
if (window.WebAssembly) {
// WebAssembly is Enabled!
} else {
// WebAssembly is Disabled!
}
Upgrade to a newer version of WebAssembly-enabled JavaScript
There's no reason for developers to stick with older versions of WebAssembly-enabled JavaScript when a newer version is available. In the case of this vulnerability, Safari 16 (and iOS 16 and macOS High Sierra) are the most recent releases and they have addressed this issue. If you're using an older version, consider updating to a newer one.
Upgrade to the latest supported version of WebAssembly
Users can mitigate the risk of these vulnerabilities being exploited by using the latest version of WebAssembly. As with any software, upgrading to the latest version is a highly recommended step for users.
Upgrade to a newer version of browser
If you are the developer of a site that’s using these vulnerabilities, you have a few options. You can upgrade to a newer version of WebAssembly in Safari, iOS and macOS. This will also update your code to fix the vulnerabilities. In addition, if you're using one of these libraries or any other library that might be vulnerable, you should consider upgrading it to use a newer version of WebAssembly as well.
Another option is to disable WebAssembly by setting the X-WebAssembly: 0 header on your pages. This will prevent any scripts from being imported into the page in question. If you do choose this option, make sure it's only applied to pages where you need it -- otherwise, this may impact your entire site's functionality.
Finally, if you don't want to upgrade either your browser or libraries at all, try adding additional security mechanisms like Content Security Policy (CSP) or HTTP Strict Transport Security (HSTS). These mechanisms force requests coming into your site to be HTTPS-only which would prevent any script from being executed without validating it first against an unknown origin.
Timeline
Published on: 09/20/2022 21:15:00 UTC
Last modified on: 09/22/2022 18:27:00 UTC