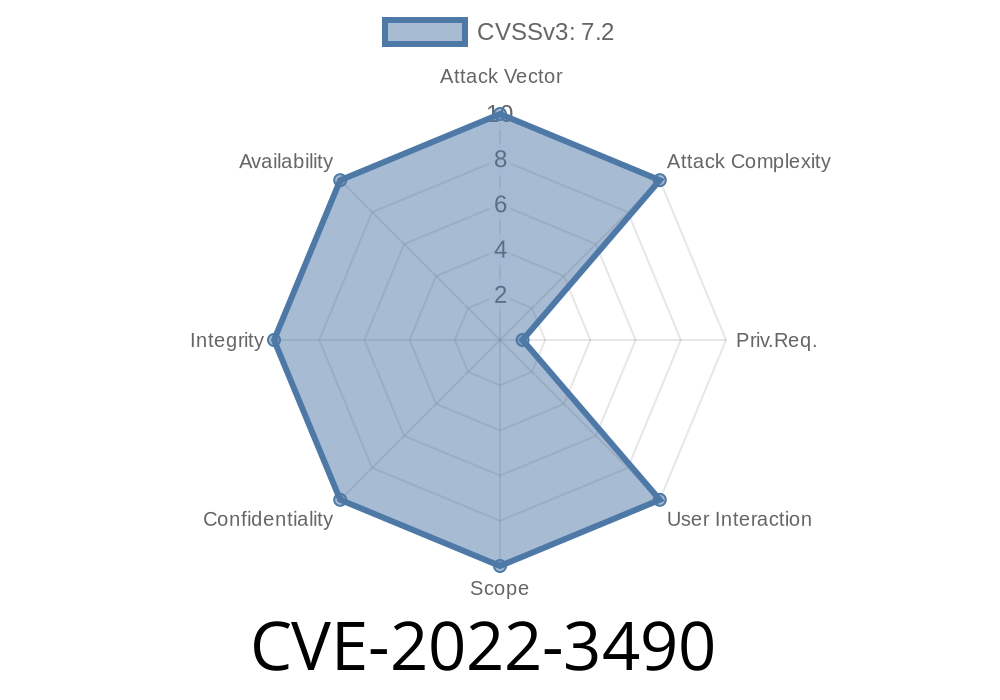
CVE-2022-3490 is a security vulnerability classified in the "PHP Object Injection" category. This vulnerability is specifically found in the Checkout Field Editor (Checkout Manager) for WooCommerce WordPress plugin before version 1.8.. An attacker (such as an admin or another high-privilege user) could exploit this security flaw to conduct various malicious operations, such as escalating privileges, stealing sensitive data, or even compromising the entire system. Let's explore this vulnerability in depth, understanding its functioning, and how to mitigate such risks.
Background
The Checkout Field Editor (Checkout Manager) for WooCommerce is a popular plugin used to customize checkout fields in WooCommerce stores (Source: https://wordpress.org/plugins/woocommerce-checkout-manager/). Developers and store owners use the plugin to add, edit, or remove various fields on the checkout page as per their needs. The plugin has more than 80,000+ installations, making it one of the most popular WooCommerce plugins.
The Issue - PHP Object Injection
The vulnerability (CVE-2022-3490) lies in the manner the plugin handles serialized data in its settings. User input is unserialized without proper validation or sanitization, thereby allowing an attacker to potentially trigger PHP Object Injection attacks when a suitable gadget is present in the system.
The code snippet below demonstrates the improper unserialization of user input in the plugin
// PHP Code Snippet from an older version of the plugin
$stored_data = get_option( 'wccs_settings' );
$unserialized_data = maybe_unserialize( $stored_data );
// Perform plugin operations using $unserialized_data
PHP Object Injection occurs when user-supplied data is processed using the unserialize() function or maybe_unserialize() function in this case. By doing so, an attacker can manipulate serialized objects to execute various malicious functions (gadget chains) when the object is unserialized.
Craft a malicious payload that includes a serialized object that triggers PHP Object Injection.
3. Inject the payload into the plugin's settings through the plugin interface or through a POST request.
References
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-3490
- https://wordpress.org/plugins/woocommerce-checkout-manager/
To mitigate the CVE-2022-3490 vulnerability, follow these steps
1. Update the Checkout Field Editor (Checkout Manager) for WooCommerce plugin to version 1.8. or later. This version contains a patch addressing the PHP Object Injection vulnerability.
2. As a general security practice, limit the number of high-privilege user accounts and monitor their activities. Unnecessary privileges should be revoked as needed.
Conclusion
Awareness about potential vulnerabilities such as CVE-2022-3490, and understanding the consequences of PHP Object Injection attacks, is crucial for website administrators and store owners. Proper validation and sanitization of user input, limiting privileged user accounts, and keeping plugins updated can significantly reduce security risks associated with software vulnerabilities.
Timeline
Published on: 11/28/2022 14:15:00 UTC
Last modified on: 11/30/2022 15:16:00 UTC