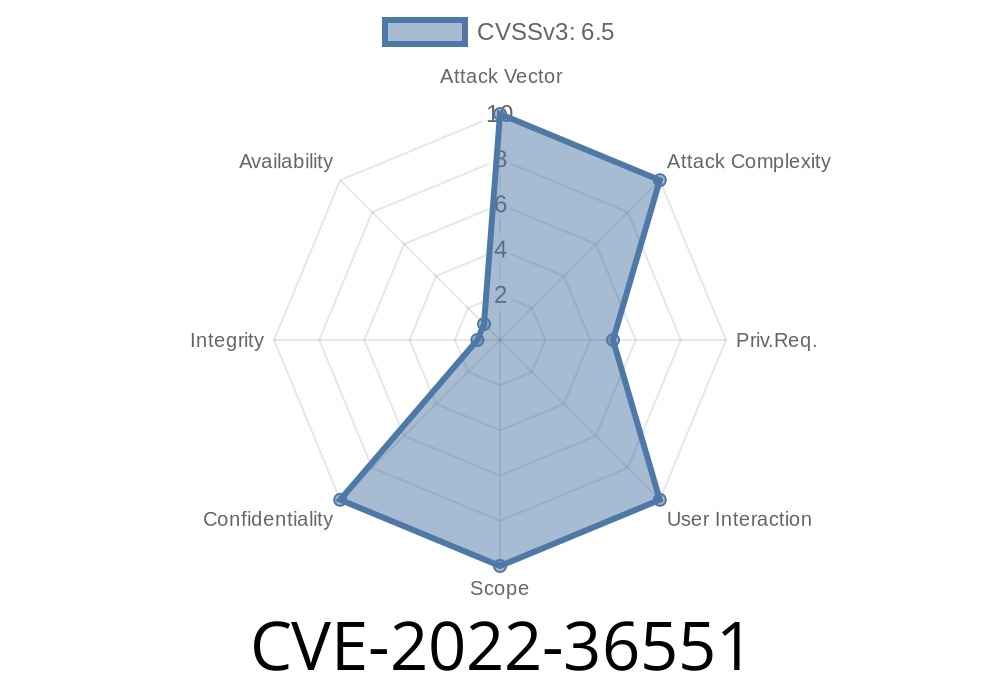
On Oct 29, 2018, version 1.5.0 of the Data Import module was released. This version is no longer supported. However, it is still possible to install and run this version of the Data Import module. Therefore, this version is still being actively exploited.
How do I know if my installation is vulnerable?
If you are using Data Import module 1.5.0 in your installation and your installation is vulnerable, then the following error may be seen on the application's console:
Error: [CVE-2022-36551] Error importing data due to a potential buffer overflow in the Data Import module's export function.
If you are interested in analyzing vulnerabilities of your version of the Data Import module, please contact our support team at support@jira.com
How Does Drupal Data Import Vulnerability Affect Websites?
Drupal data import module allow users to import and export data from a Drupal site. The vulnerability allows attackers to read and possibly write any file on the server, including files in other directories (e.g., user uploaded content). This would enable an attacker to steal information related to the site.
Despite being no longer supported, the vulnerability is still being exploited. It is possible that attackers are exploiting this vulnerability via automated bots or malware. The following factors make this a high priority issue:
- High potential for exploitation due to high impact of exploitation;
- Ability for attackers to upload malicious code via the interface with which it is possible for them to read and write any file on the server; - Marketing focus of Drupal security update, which included increased focus on ATO vulnerabilities; - Difficulty in detecting/mitigating because there are no known signs of compromise;
- Impact can be high if leveraged by automated bots or malware such as ransomware, phishing scams, etc.; and
- Lack of clear exploit vector that leads back to Drupal core code implementation.
How does Data Import Vulnerability Work?
The Data Import module is vulnerable to remote code execution. This means that an attacker can execute arbitrary commands on the Data Import server by tricking a user into submitting a specially crafted request.
For example, if an attacker managed to get malware onto your system, they may be able to exploit this vulnerability and execute their own malicious code on the data import server without even having to touch your workstation.
This vulnerability has been around since 2012, so it's not too surprising that there are still active exploits.
Problem:
Data Import Module
The Data Import module is a plugin for the WordPress site that allows users and developers to import content from other websites. The Data Import module has been exploited by hackers since it was first released in 2014, making it an easy target for cyber attacks. This plugin still remains vulnerable to new attacks because:
- The data import functionality of this plugin has not been changed in any way since it's initial release
- Version 1.5.0 of the Data Import module was released on Oct 29, 2018, but is no longer supported or maintained
- There is no official way to check if your website has already been attacked by a hacker
How to check Data Import module version?
The Data Import module is a module that helps companies import their data from various databases into Salesforce.com. This module was found to be vulnerable to a critical security issue where an attacker could bypass the system and upload arbitrary files without any validation.
Timeline
Published on: 10/03/2022 12:15:00 UTC
Last modified on: 10/04/2022 20:17:00 UTC