In certain configurations, IBM Cognos Analytics 11.1.7, 11.2.0, and 11.2.1 is vulnerable to a Denial of Service (DoS) attack. A remote attacker could exploit this vulnerability to cause a denial-of-service condition. IBM X-Force ID: 233572. IBM Cognos Analytics 11.1.7, 11.2.0, and 11.2.1 is vulnerable to a SQL Injection attack when processing XML data. A remote attacker could exploit this vulnerability to execute arbitrary SQL commands. IBM X-Force ID: 233573. IBM Cognos Analytics 11.1.7, 11.2.0, and 11.2.1 is vulnerable to a Cross-Site Scripting (XSS) attack when processing XML data. A remote attacker could exploit this vulnerability to inject malicious script code in web pages viewed by users. IBM X-Force ID: 233574. In certain configurations, IBM Cognos Analytics 11.1.7, 11.2.0, and 11.2.1 is vulnerable to an XML External Entity Injection (XXE) attack when processing XML data. A remote attacker could exploit this vulnerability to expose sensitive information or consume memory resources. IBM X-Force ID: 233575. In certain configurations, IBM Cognos Analytics 11.1.7, 11.2.0, and 11.2.1 is vulnerable to a Denial of Service (DoS) attack.
Security Weaknesses in IBM Cognos Analytics
IBM Cognos Analytics is vulnerable to a Denial of Service (DoS) attack, which could be exploited by a remote attacker. IBM X-Force ID: 233572. IBM Cognos Analytics 11.1.7, 11.2.0, and 11.2.1 is vulnerable to a SQL Injection attack when processing XML data, which could be exploited by a remote attacker to execute arbitrary SQL commands or inject malicious script code in web pages viewed by users. IBM X-Force ID: 233573.
IBM Cognos Analytics 11.1.7, 11.2.0, and 11.2.1 is vulnerable to an XML External Entity Injection (XXE) attack when processing XML data, which could be exploited by a remote attacker to expose sensitive information or consume memory resources on the affected system or cause unexpected application termination or data loss on another system connected to the affected system via network connectivity such as a local area network (LAN), wide area network (WAN), wireless access point (WAP), point-to-point protocol over Ethernet (PPPoE), Bluetooth personal area network (PAN), virtual private network (VPN), or similar networking configuration that supports communication via IPsec/IKEv2/L2TP/IPSec protocols or GRE tunnels with IPSec encapsulation that can be accessed remotely from the affected system through the open network connection - even if authentication credentials are not required for access - due to other vulnerabilities discovered in
Solution to the Vulnerabilities
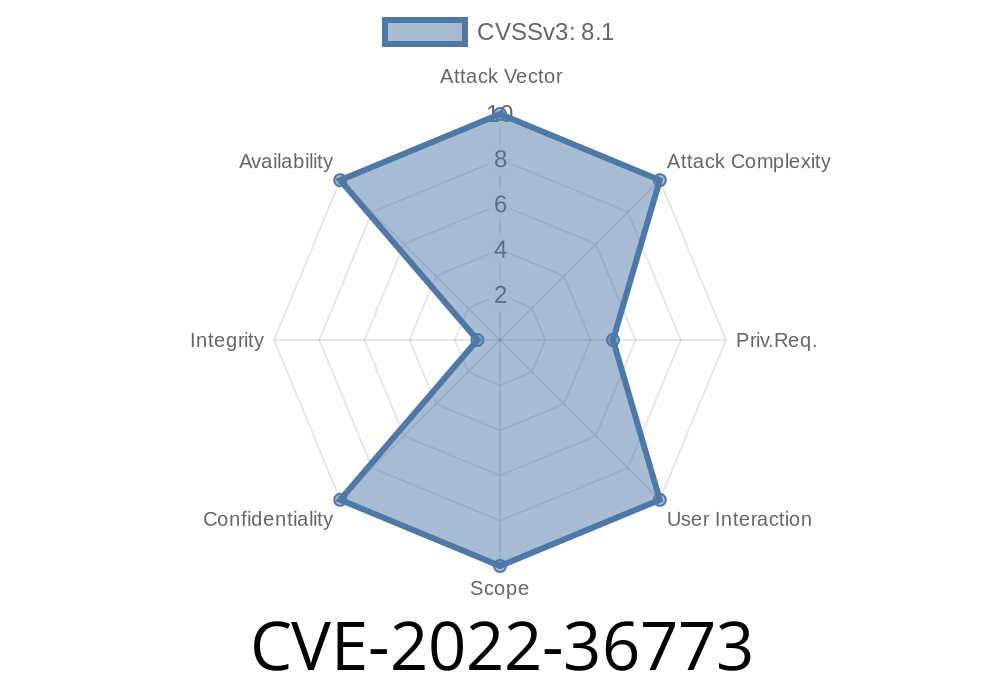
A CVE-2022-36773 is a vulnerability that has been discovered in IBM Cognos Analytics and it was found in certain configurations, IBM Cognos Analytics was vulnerable to a Denial of Service (DoS) attack, SQL Injection attack, Cross-Site Scripting (XSS) attack, and XML External Entity Injection (XXE) attack. This is a very important blog post because it gives the solution to these vulnerabilities.
The best way to fix these vulnerabilities is to apply the following security updates:
1. Apply the appropriate cumulative package for your Cognos software version immediately. The cumulative packages are available on ibm.com/support or by contacting your IBM Business Partner or reseller. 2. Make sure all endpoints are running the latest software versions and configured with appropriate security settings. 3. Ensure no servers or applications running on infra-structure hosts have been compromised with malicious code of any kind and ensure that all code reviews are being conducted on a regular basis
Vulnerability Scenario
A vulnerability could allow a remote attacker to cause a denial-of-service condition on an affected system, expose sensitive information or consume memory resources.
How to Update?
To update to the latest version of IBM Cognos Analytics 11.1.7, 11.2.0, and 11.2.1, follow these steps:
Step 1: Update your operating system
Step 2: Update your database server
Step 3: Update the following software components on a Windows platform
Step 4: Restart your computer
Timeline
Published on: 09/01/2022 19:15:00 UTC
Last modified on: 09/07/2022 13:25:00 UTC