Adobe recommends users update to the latest version 23.5.1. The update is currently available through the Creative Cloud application. Adobe warned that although it has successfully tested the update on Windows, Mac OS X, and Linux, it is possible that some users may still be running an earlier version of Adobe Photoshop. Adobe recommends users update to the latest version 23.5.1. The update is currently available through the Creative Cloud application. Adobe warned that although it has successfully tested the update on Windows, Mac OS X, and Linux, it is possible that some users may still be running an earlier version of Adobe Photoshop. Adobe Photoshop versions 22.5.8 (and earlier) and 23.4.2 (and earlier) are affected by a Use After Free vulnerability that could lead to disclosure of sensitive memory. An attacker could leverage this vulnerability to bypass mitigations such as ASLR. Exploitation of this issue requires user interaction in that a victim must open a malicious file.
Adobe Photoshop versions 22.5.8 (and earlier) and 23.4.2
(and earlier) are affected by a Use After Free vulnerability that could lead to disclosure of sensitive memory. An attacker could leverage this vulnerability to bypass mitigations such as ASLR. Exploitation of this issue requires user interaction in that a victim must open a malicious file.
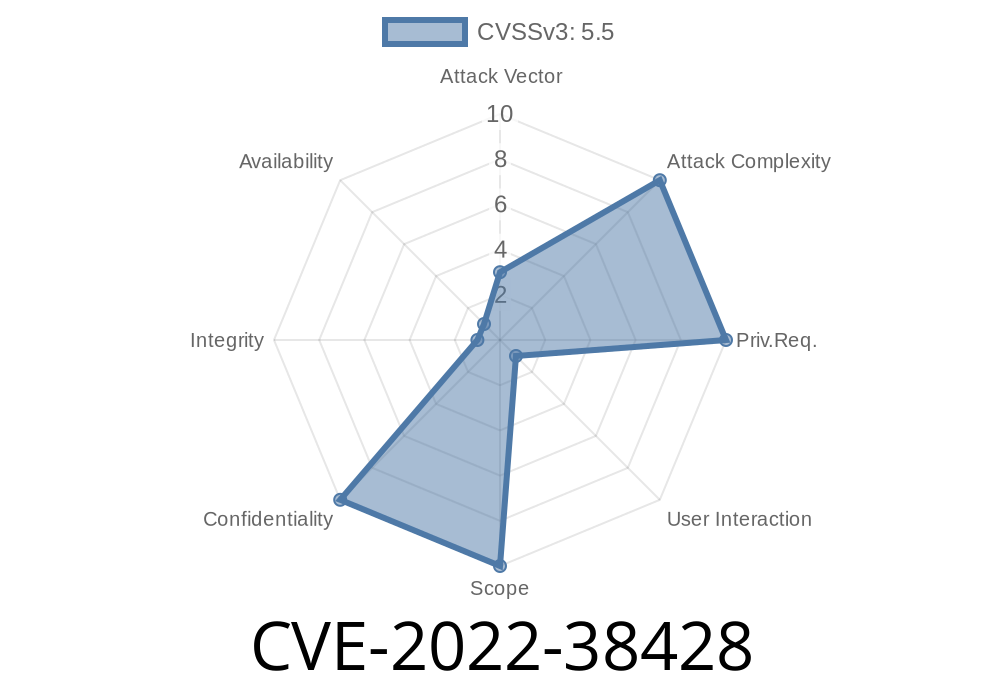
This CVE-2022-38428 is an information disclosure vulnerability for Adobe Photoshop versions 22.5.8 (and earlier) and 23.4.2 (and earlier). This information disclosure vulnerability is rated critical severity, which means it is exploitable remotely, allowing attackers to gain access to the full system of an affected computer with relative ease and without authentication methods being required.
Adobe Photoshop versions 22.5.8 (and earlier) and 23.4.2 (and earlier) are affected by a Use After F Update
Adobe's recommendation is to update your Photoshop version to the latest 23.5.1, which is currently available through the Creative Cloud application. Adobe warns that although it has successfully tested the update on Windows, Mac OS X, and Linux, it is possible that some users may still be running an earlier version of Photoshop. Adobe recommends users update to the latest version 23.5.1. The update is currently available through the Creative Cloud application. Adobe warns that although it has successfully tested the update on Windows, Mac OS X, and Linux, it is possible that some users may still be running an earlier version of Photoshop
Adobe Photoshop versions 22.5 and earlier are affected
Adobe is issuing an update to Adobe Photoshop versions 22.5 and earlier that addresses the vulnerability. The update is currently available through the Creative Cloud application. It will be available via Windows Update on October 31, 2018, and on Mac OS X and Linux in early 2019. All users of Adobe Photoshop should update to this latest version of Adobe Photoshop as soon as possible to ensure they are protected from exploitation by adversaries. Although this vulnerability does not have a zero-day exploit associated with it, it can only be triggered when a user interacts with a malicious file that exploits this issue. Generally speaking, if you’re running a system with up-to-date software, your systems are likely not vulnerable and you don’t need to take action at this time. If you do see a malicious file exploiting this issue, please contact your local authorities immediately.
Adobe Photoshop versions 22.5.7 (and earlier) are affected by a Use After Free vulnerability that co
**NOTE:** the option to "Disable Java" must be disabled for this exploit to be effective.
Adobe has released a security update for Adobe Photoshop versions 22.5.7 and earlier which addresses a Use After Free vulnerability that could lead to disclosure of sensitive memory. An attacker could leverage this vulnerability to bypass mitigations such as ASLR and execute arbitrary code on the target system. Exploitation of this issue requires user interaction in that a victim must open a malicious file, or if the "Enable Java" option is not disabled, open an applet.
Timeline
Published on: 09/16/2022 18:15:00 UTC
Last modified on: 09/20/2022 18:28:00 UTC