All Adobe Experience Manager versions prior to 6.5.13.0 are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. All AEM installations on Windows are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. All AEM installations on Mac are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. In order to exploit this issue, an attacker must be able to persuade a victim to visit a maliciously crafted URL. All AEM versions prior to 6.5.13.0 are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. All AEM installations on Windows are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. All AEM installations on Mac are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. In order to exploit this issue, an attacker must be able to persuade a victim to visit a maliciously crafted URL. An attacker may leverage this vulnerability to steal cookie-based authentication credentials, view personal information, conduct phishing campaigns, or manipulate data. An attacker may leverage this vulnerability
CVSS Scores
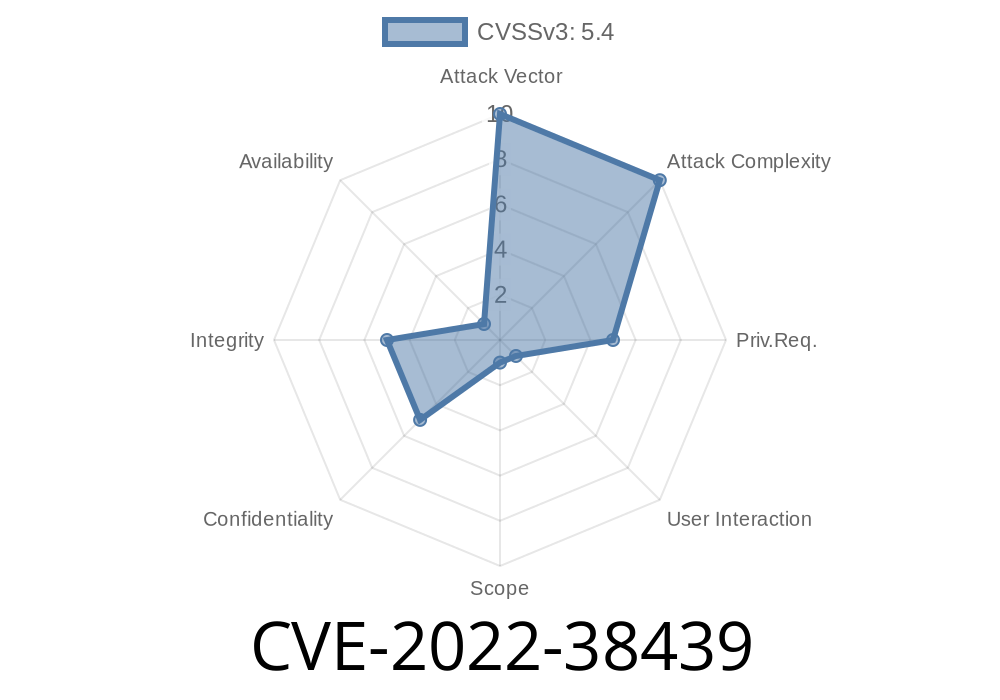
CVSS v3: 5.2
CVSS base score: 7.5
CVSS impact score: 3.8
CVSS exploitability score: 8
All Adobe Experience Manager versions prior to 6.5.13.0 are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. All AEM installations on Windows are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. All AEM installations on Mac are affected by a XSS flaw due to failed XSS filter validation. This issue exists in the default instance of the AEM application. In order to exploit this issue, an attacker must be able to persuade a victim to visit a maliciously crafted URL. An attacker may leverage this vulnerability to steal cookie-based authentication credentials, view personal information, conduct phishing campaigns, or manipulate data
Timeline
Published on: 09/23/2022 19:15:00 UTC
Last modified on: 09/26/2022 22:13:00 UTC