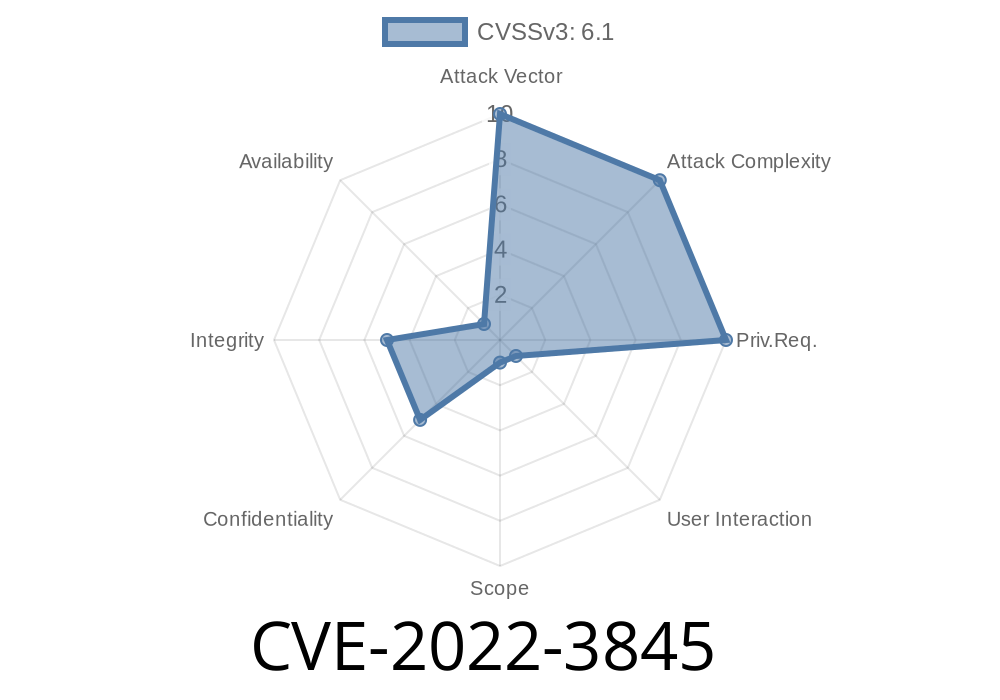
In late 2022, security researchers discovered a cross-site scripting (XSS) vulnerability in phpIPAM, a web-based IP address management application widely used by network administrators. This issue, now tracked as CVE-2022-3845 and VDB-212863, allows remote attackers to execute arbitrary scripts in the context of the victim's browser, posing a risk to sensitive network data and user accounts.
This article walks through what makes CVE-2022-3845 dangerous, how it can be exploited, and how to fix it. We'll wrap up with references for further reading, so you can stay secure.
The vulnerability affects an unknown functionality in the file
app/admin/import-export/import-load-data.php
Specifically, when handling imports via “Import Preview Handler,” insufficient input validation allows attackers to inject malicious JavaScript into the application. When an administrator previews or imports a file, the malicious script runs in their browser.
Exploit Scenario: How an Attack Works
Suppose your organization’s phpIPAM is running a vulnerable version (before 1.5.). An attacker could:
Trigger XSS in Preview
When the admin previews the import, the javascript runs—potentially stealing session cookies, redirecting to phishing pages, or defacing the UI.
Vulnerable Code (Explained)
In affected versions, the script which displays import previews does not sanitize user input. Here’s what that code might look like (simplified for this example):
<?php
// load data from csv
foreach ($csvData as $row) {
echo "<tr>";
echo "<td>".$row['Hostname']."</td>"; // Vulnerable: not escaped!
echo "<td>".$row['Description']."</td>"; // Vulnerable: not escaped!
echo "</tr>";
}
?>
Problem: Data goes straight from the CSV to the browser, with no escaping or sanitization.
The Patch
The vulnerability was patched with commit 22c797c3583001211fe7d31bccd3f1d4aeeb3bbc in phpIPAM 1.5..
The fix adds HTML escaping to output functions
<?php
foreach ($csvData as $row) {
echo "<tr>";
echo "<td>".htmlspecialchars($row['Hostname'])."</td>";
echo "<td>".htmlspecialchars($row['Description'])."</td>";
echo "</tr>";
}
?>
Now, special characters like < and > are rendered as harmless text, not executable code.
Upgrade to phpIPAM 1.5. or Later
Download the latest release from the phpIPAM GitHub releases page.
Verify Patch
Make sure your import-load-data.php reflects the patched code.
References
- NVD: CVE-2022-3845
- phpIPAM Patch Commit
- VulDB: VDB-212863
- phpIPAM Official Site
Stay updated: Keeping your network tools up to date is the best way to keep your infrastructure secure. If you use phpIPAM, this upgrade is a must!
Timeline
Published on: 11/02/2022 20:15:00 UTC
Last modified on: 11/04/2022 01:32:00 UTC