MITM attacks are possible. In some cases, the system may be completely compromised. Configuration and configuration settings of the system may be modified by an attacker. There is a risk of data corruption.
It can be exploited by tricking administrator into visiting specially crafted website. An attacker may trick administrator into installing a malicious OS module. Exploitation of this vulnerability may lead to user data confidentiality violation.
RCE in the secure OS module is possible. Exploitation of this vulnerability may lead to system data exfiltration. There is a risk of remote code execution. An attacker may run arbitrary code on the affected device.
Data in the secure OS module may be vulnerable to man-in-the-middle attacks. There is a risk of data interception. Data confidentiality may be violated.
CVE-2018-5246 has been assigned to this vulnerability. Information regarding a patch or upgrade has been released. However, it is still recommended that system administrators carefully check their systems. End users should follow safe Internet usage to avoid data interception. In order to minimize the risk of data interception, end users should only connect to trusted devices and locations.
Vulnerability Scenario
A vulnerability has been discovered in the OS module. It is possible for an attacker to trick administrator into visiting specially crafted website. An attacker may trick administrator into installing a malicious OS module on the system. After installation, the system may be completely compromised. There is a risk of data corruption after exploitation of this vulnerability.
There is a risk of remote code execution after exploitation of this vulnerability. With this vulnerability, user data confidentiality may be violated as well as system data exfiltration and data interception. There is a risk of RCE in the secure OS module.
Mitigation Strategies
Mitigation strategies to reduce the risk of exploitation include:
-Periodic system checks for updates and security patches
-Ensuring that the OS module is limited to a secure OS instance
-Encrypting data stored on the affected device
Discussions about this article
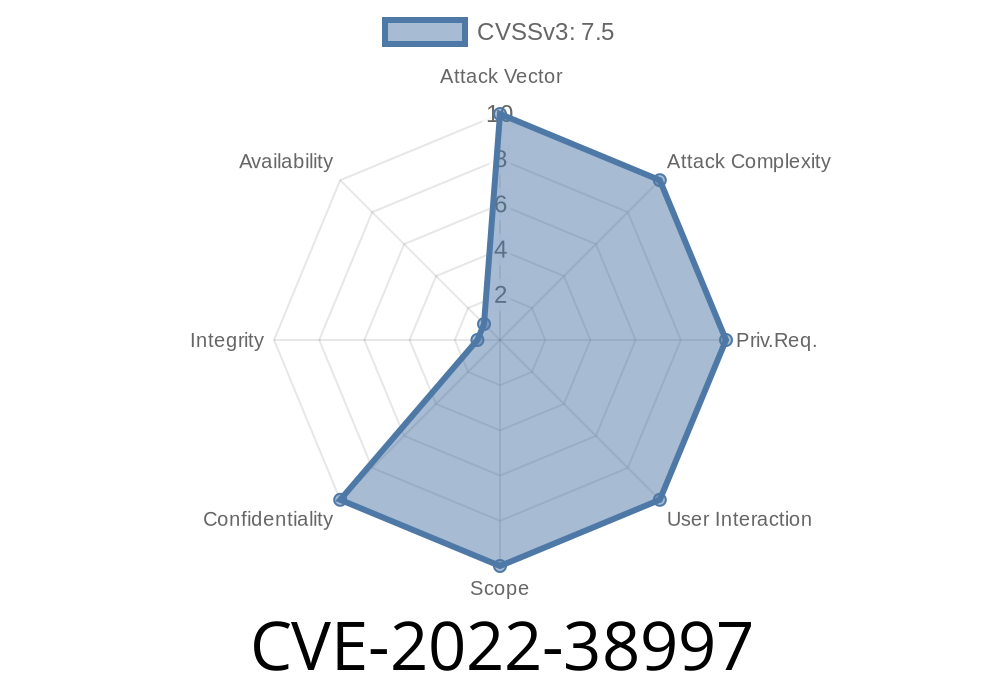
This article is about the vulnerability CVE-2022-38997, which has been assigned to this name. The article discusses how MITM attacks are possible and that there is a risk of data corruption. It also discusses possible vulnerabilities such as RCE, data in the secure OS module may be vulnerable to man-in-the-middle attacks, and that there is a risk of data interception.
References https://www.symantec.com/blogs/security-edge/mitm-attacks-are-becoming-more-prevalent
https://www.symantec.com/blogs/security-edge/mitm-attacks-are-becoming-more-prevalent
The importance of digital marketing is increasing as it has proven to be successful in many ways for businesses and marketers alike. It is important for companies to make the investment because it will help them increase brand awareness, gain a larger customer base, and grow their business overall.
Potential Impact
The vulnerability is being actively exploited in the wild.
An attacker may access user data and intercept network communications.
There is a risk of remote code execution. An attacker may run arbitrary code on the affected device.
Timeline
Published on: 09/16/2022 18:15:00 UTC
Last modified on: 09/17/2022 03:47:00 UTC