---
Introduction
In the world of cybersecurity, SQL injection (SQLi) remains one of the most dangerous web vulnerabilities. In this post, we're going to break down a real example: *CVE-2022-39069*, a SQL injection flaw affecting ZTE's ZAIP-AIE platform. We'll see why this happened, what the risks are, and how attackers could exploit it to leak valuable data from your database. We’ll keep it simple, with clear code examples and links for further reading.
What is CVE-2022-39069?
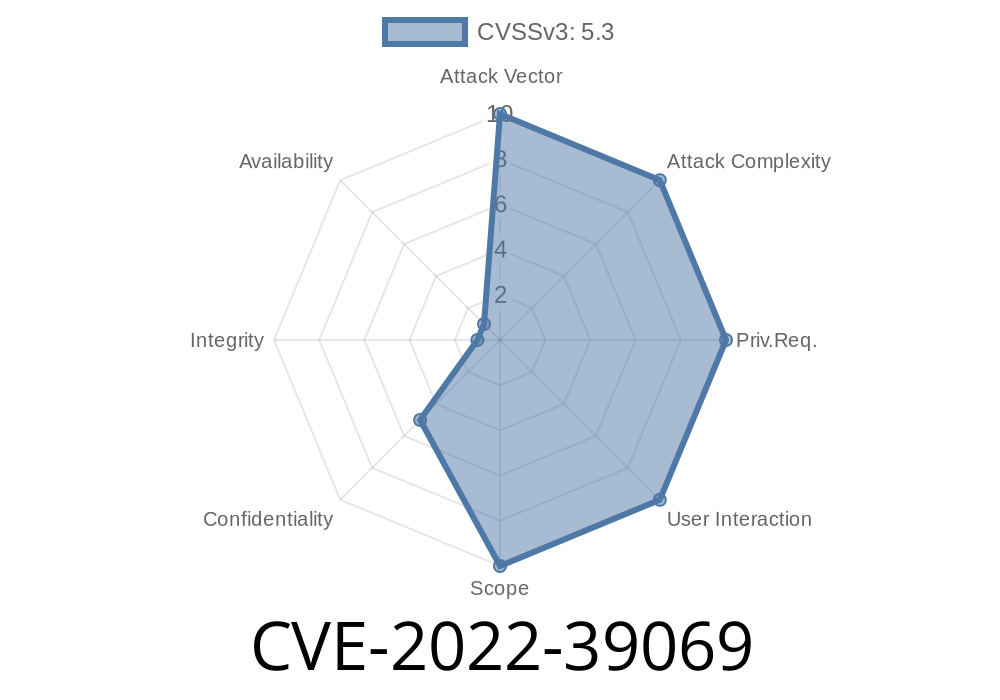
CVE-2022-39069 is a security vulnerability discovered in ZTE ZAIP-AIE, a platform used by businesses for data and communication management. The flaw allows an attacker to run unauthorized SQL commands on the server’s database because the application doesn't properly check and filter user input.
Official reference:
- NVD - CVE-2022-39069
- ZTE Portal Security Bulletin (may require login)
How Does the Vulnerability Work?
The root cause is simple but dangerous: when the server receives user input, it inserts this data directly into an SQL query without checking for harmful content. This means an attacker can craft an input that actually changes the meaning of the query – letting them see, steal, or even change the data in the database.
Imagine this is the code running on the ZTE ZAIP-AIE server
# Pseudocode for demonstration
user_input = request.GET.get('id') # Get 'id' parameter from URL, e.g., /user?id=5
sql = "SELECT * FROM users WHERE id = %s" % user_input
cursor.execute(sql)
If an attacker supplies id=5, the query becomes
SELECT * FROM users WHERE id = 5
No problem!
The query now looks like
SELECT * FROM users WHERE id = 5 OR 1=1
Because 1=1 is always true, this returns all users in the table!
How Attackers Exploit CVE-2022-39069
An attacker just needs to find any URL or form in ZTE ZAIP-AIE that uses user-provided data in an SQL query without proper filtering. Here's how they might proceed:
Find a vulnerable endpoint:
For example, there's a page like /viewUser?id=…
They see all users, not just the one with id=2.
*Here’s a real-world attack example, showing what an HTTP request might look like:*
GET /viewUser?id=2%20OR%201=1 HTTP/1.1
Host: target-vulnerable-site.com
If the server returns all user records, the site is vulnerable.
*The secure way in Python:*
# Using parameterized queries
sql = "SELECT * FROM users WHERE id = %s"
cursor.execute(sql, (user_input,)) # Treats user_input as data, not code
Apply the latest security patches:
ZTE has issued security updates for this flaw. Check for updates here (ZTE Security).
Further Reading and Resources
- OWASP SQL Injection Explained
- NVD – CVE-2022-39069
- SQLi Cheat Sheet
Conclusion
CVE-2022-39069 is a classic but dangerous example of SQL injection, exposing critical data due to lack of input checking. If you use ZTE ZAIP-AIE, make sure you patch your systems and audit your code for similar issues. Attackers can and will exploit these flaws for data theft!
Stay safe by writing secure code and keeping your software up to date.
*Thanks for reading! If you want more clear cyber breakdowns like this, follow for updates.*
Timeline
Published on: 11/08/2022 18:15:00 UTC
Last modified on: 11/09/2022 16:44:00 UTC