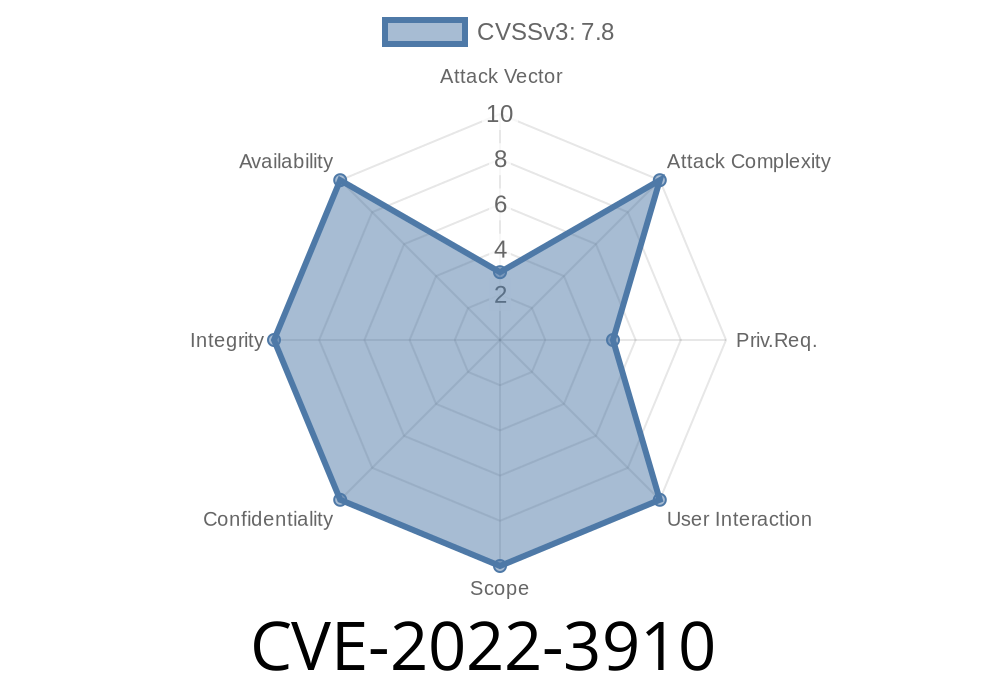
A recently discovered vulnerability within the Linux Kernel, identified as CVE-2022-3910, allows for privilege escalation through Use After Free (UAF) attacks. This security flaw has been found to stem from an improper update of the reference count in io_uring, causing a Use-After-Free vulnerability and ultimately leading to local privilege escalation.
Code Snippet
The vulnerability is caused by io_msg_ring invoking the fixed file with the function io_fput_file(). This call improperly decreases the reference count, which is integral to memory management, ultimately causing a Use-After-Free situation. The code snippet with the vulnerability:
...
struct file *file;
...
if (mask & REQ_F_FIXED_FILE) {
io_fput_file(file);
}
...
Fixed files are a part of the ring structure and should not be decreased separately.
Exploit Details
An attacker can exploit this vulnerability by leveraging the UAF scenario. They could manipulate data, execute arbitrary code, or take control of the kernel. Since the Linux kernel serves as the backbone to an immense range of software applications, the implications of a successful privilege escalation attack can be severe.
The security issue has been acknowledged and resolved in this commit
https://github.com/torvalds/linux/commit/fc7222c3a9f56271fba02aabbfbae999042f1679
By examining the changes introduced in the above commit, it is clear that the improper reference count decrease has been removed, effectively addressing the Use-After-Free vulnerability.
Mitigation and Recommendations
To mitigate the risks associated with CVE-2022-3910, users should promptly upgrade their Linux kernel to a version that includes the fix:
https://github.com/torvalds/linux/commit/fc7222c3a9f56271fba02aabbfbae999042f1679
By applying the necessary updates, users can prevent potential security threats and ensure a more robust kernel environment. Additionally, it is crucial to stay informed about any new security issues discovered within the Linux kernel, and to be proactive in applying patches as they become available.
Timeline
Published on: 11/22/2022 13:15:00 UTC
Last modified on: 02/14/2023 21:13:00 UTC