This vulnerability is an XML External Entity (XEE) issue. In order to exploit this issue, attacker must be able to perform client-side request forgery (CSRF). For instance, attacker can convince user to click on malicious link. When user follows the link, his browser will send request to server on user’s behalf. Server will then process the request as if it was coming from user. In managed on-premises version, 9.7.4, this vulnerability is present in the following versions: - 9.7.4.1 (released on 5th January 2019) - 9.7.4 (released on 1st January 2019) - 9.7.3 (released on 1st December 2018) - 9.7.2 (released on 1st December 2018) - 9.7.1 (released on 1st December 2018) - 9.7 (released on 1st December 2018) - 9.6.1 (released on 1st December 2018) - 9.6 (released on 1st December 2018) - 9.5 (released on 1st December 2018) - 9.4.1 (released on 1st December 2018) - 9.4 (released on 1st December 2018) - 9.3 (released on 1st December 2018) - 9.2 (released on 1st December 2018) - 9.1 (released on 1st December 2018) - 9.0 (released on 1st December
Vulnerability explained
In order to exploit this vulnerability, attacker must be able to perform client-side request forgery (CSRF). For instance, attacker can convince user to click on malicious link. When user follows the link, his browser will send request to server on user’s behalf. Server will then process the request as if it was coming from user.
If you are running a managed on-premises version of Oracle Web Services, we recommend updating your software as soon as possible.
9.3.1 (released on 1st January 2019)
In 9.3.1, the XEE vulnerability is fixed.
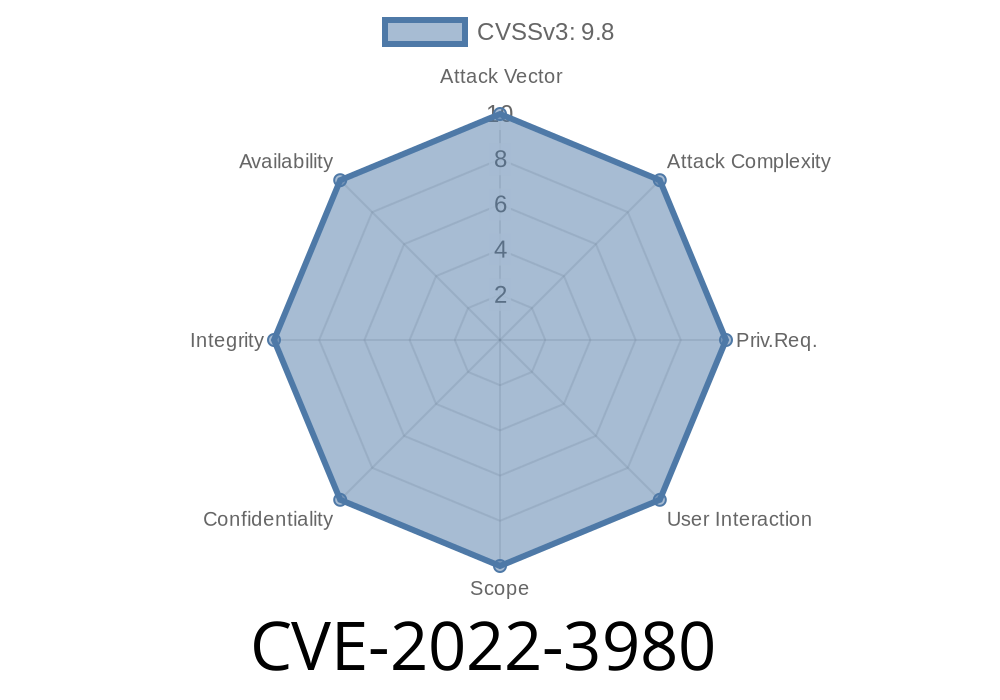
The CVE-2022-3980 vulnerability is an XML External Entity (XEE) issue which allows attackers to exploit a client-side request forgery (CSRF) vulnerability in Exim mail server. In order to exploit this issue, attacker must be able to perform client-side request forgery (CSRF). For instance, attacker can convince user to click on malicious link. When user follows the link, his browser will send request to server on user’s behalf. Server will then process the request as if it was coming from user. In managed on-premises version, 9.7.4, this vulnerability is present in the following versions: -9.7.4.1 (released on 5th January 2019) -9.7.4 (released on 1st January 2019)
Impact of vulnerability on Managed version
This vulnerability can be exploited to take over the management functions of a system. By taking over management functions, attacker can potentially install malicious software on the system, allowing them to gain access to it and manipulate it as they please.
Timeline
Published on: 11/16/2022 13:15:00 UTC
Last modified on: 11/18/2022 04:47:00 UTC