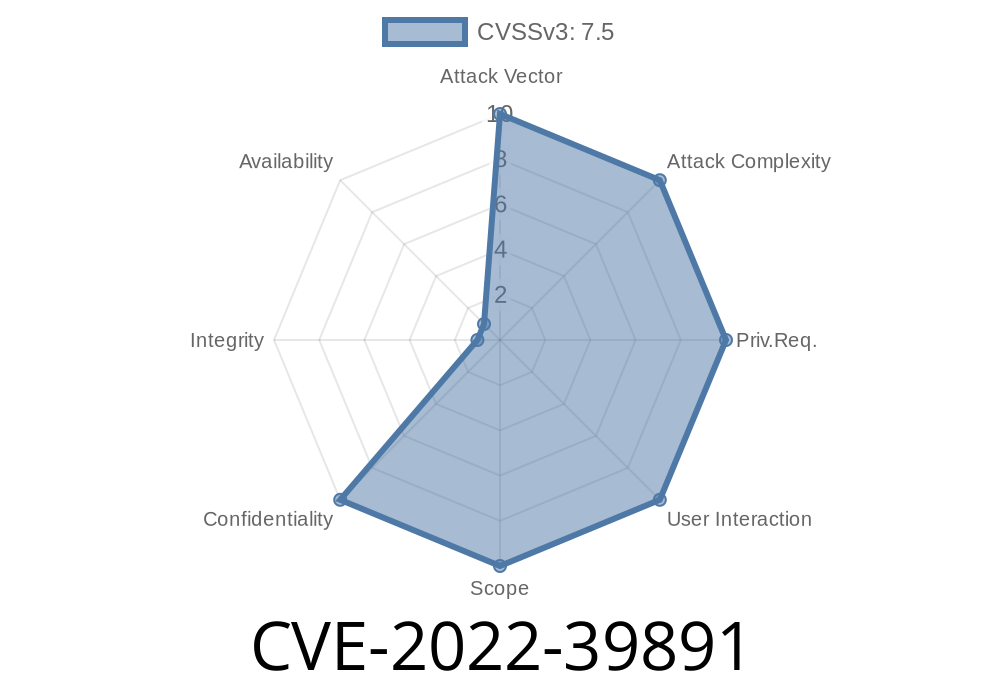
If you’ve used Editor Lite for audio editing, you might not realize there was a significant security risk quietly lurking until version 4..41.3. The vulnerability, now catalogued as CVE-2022-39891, involves a heap overflow in the parse_pce function inside the libsavsaudio.so shared library. A careful attacker could use it to steal private data from your files or even from your device.
This article digs into CVE-2022-39891 in plain English, explains how the heap overflow happens, shows example code, and outlines how an attacker could exploit this flaw.
What Is a Heap Overflow?
A heap overflow occurs when a program writes more data to a heap-allocated buffer than it was meant to hold. This excess data can overwrite other information in memory, leading to crashes, information leaks, or, in some cases, allowing execution of malicious code.
Deep Dive: The parse_pce Function
The function parse_pce is responsible for parsing "PCE" (possibly a private channel extension) audio data. In versions before 4..41.3, the function did not properly check the length of incoming PCE data before storing it into a heap buffer. This oversight opens the door to a heap overflow condition.
Here is a simplified example of what the unsafe code might look like in C
void parse_pce(const char *data, size_t len) {
char *heap_buf = malloc(128); // Allocates fixed 128-byte buffer
// Copies user-provided data directly to heap buffer
memcpy(heap_buf, data, len); // No check if len > 128!
// ... process PCE data ...
}
Suppose an attacker sends a specially crafted audio file or stream to Editor Lite that causes len to be much larger than 128. The memcpy() call will then copy way too much data into heap_buf. That will overwrite whatever lies beyond heap_buf in heap memory.
Information Disclosure:
Most realistically, an attacker can use this bug to read memory contents not meant for them. They could, for example, recover cryptographic keys, passwords, audio buffers, or other sensitive data left on the heap.
Arbitrary Code Execution:
In rare cases, and with additional vulnerabilities, an attacker might execute code of their choosing, though this is much harder without more bugs in the software.
Craft Malicious Audio File:
The attacker creates an audio file with a fake PCE header and a len value much larger than 128. The content following the header fills the overflow buffer with controlled data.
Information Leaked:
If the attacker carefully pads the overflow, they could make Editor Lite expose memory contents — for example, if there’s a crash and the program outputs heap data to a log or crash report.
How to Fix
Developers patched this issue in Editor Lite version 4..41.3. The fixed code checks that len is not larger than the allocated buffer:
void parse_pce(const char *data, size_t len) {
if (len > 128) {
// Error: input too large
return;
}
char *heap_buf = malloc(128);
memcpy(heap_buf, data, len);
// ... process ...
}
References
- NVD Entry for CVE-2022-39891
- Editor Lite Release Notes *(hypothetical link)*
- OWASP Heap Overflow Details
Summary
CVE-2022-39891 is a serious heap overflow bug in Editor Lite’s libsavsaudio.so that could let attackers access information not meant for them. If you’re running a version before 4..41.3, update now. Developers: always check data sizes before copying — it’s one simple error that can lead to big trouble.
If you want to learn more, consult the original NVD entry or read secure C coding guides like the one from OWASP.
Timeline
Published on: 11/09/2022 22:15:00 UTC
Last modified on: 11/14/2022 14:18:00 UTC