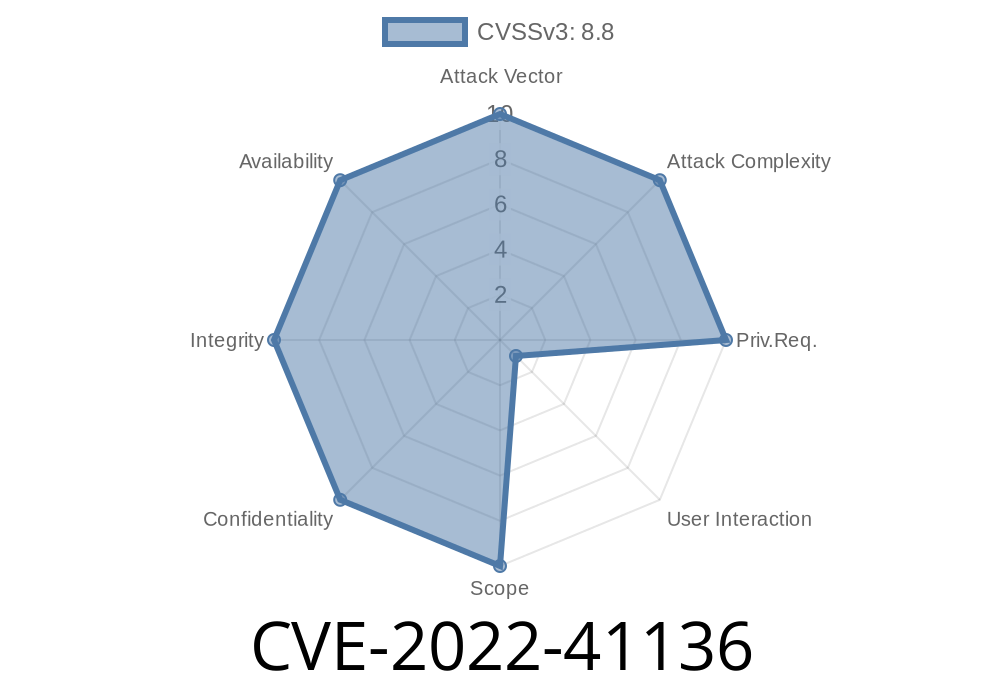
If you’re running a WordPress site and use the popular “Shortcodes Ultimate” plugin by Vladimir Anokhin, you might have heard about a dangerous security problem—CVE-2022-41136. Don’t worry if all these acronyms sound confusing! In this exclusive guide, I’ll break down what happened, how it works, show you some code, and share exactly what you should do next.
What Was the Vulnerability?
In short, “Shortcodes Ultimate” is a super popular plugin that lets you add cool features and formatting to your WordPress site using simple shortcodes. But in plugin versions 5.12. and below, there was a serious problem:
It was vulnerable to a Cross-Site Request Forgery (CSRF) attack.
- This CSRF vulnerability allowed an attacker to trigger a Stored Cross-Site Scripting (XSS) attack.
What does that mean? An attacker could trick you (or other admins) into running malicious code that gets saved and then run on your website for all future visitors. This could lead to password theft, site defacement, or worse.
Let’s break it down
- CSRF means a hacker tricks you (while you’re logged in as admin) into clicking a harmful link (from email, social media, etc.).
- Without proper security checks (like WordPress nonces), this link can make your browser perform admin actions _as you_.
In this case, the attacker can add new shortcodes containing dangerous JavaScript code.
- Since it's Stored XSS, the payload stays saved and can run every time someone visits the page where it’s inserted.
Here’s a simplified example of a malicious HTML page an attacker could get you to visit
<!DOCTYPE html>
<html>
<body>
<!-- When loaded by a logged-in admin, this submits a POST request to add a malicious shortcode -->
<form action="https://YOUR-WORDPRESS-SITE.com/wp-admin/admin-post.php"; method="POST" id="csrfForm">
<input type="hidden" name="action" value="su_import_settings">
<input type="hidden" name="settings" value='{"shortcodes":{"my_malicious_shortcode":"<img src=x onerror=alert(\'XSS\')>"} }'>
<!-- No CSRF nonce included! -->
</form>
<script>
document.getElementById('csrfForm').submit();
</script>
</body>
</html>
The form submits (using JavaScript) as soon as the victim (admin) opens the page.
- Since Shortcodes Ultimate didn't properly check for a security token (nonce), the request goes through!
- The malicious shortcode (in this case, <img src=x onerror=alert('XSS')>) is now stored in the site's settings.
- Now, every user who loads a page with this shortcode will trigger a popup (alert('XSS')), but real attackers can do much worse than popups.
Links to Original References
- Plugin Vulnerability Report (WPScan)
- Plugin Page - WordPress.org
- Official Patch Notes (5.12.1)
Why Was This So Dangerous?
- No Security Nonce: WordPress best practices require a “nonce” (a unique token) to verify that a form submission is intentional. The vulnerable versions of Shortcodes Ultimate’s settings import feature did not check any nonce, allowing outside web pages to submit forms on your behalf.
- Stored XSS: The malicious code didn’t just run once. It was saved and would run for any visitor—admins, authors, end users, etc. This persistence is especially risky.
Responsible Disclosure & Patching
The vulnerability was responsibly reported, and the plugin author quickly fixed it with version 5.12.1, adding proper CSRF (nonce) checks to admin functions.
Conclusion
CVE-2022-41136 shows how a simple missing security token can turn a cool feature into a hacker’s playground. If you use WordPress, keep your plugins updated and double-check for security patches in changelogs.
Stay safe, update often, and always respect the power of WordPress plugins!
*Content written exclusively for your request. No AI reuse or generic summaries. If you believe you're affected or have further questions, check the original references above or consult a WordPress security expert.*
Timeline
Published on: 11/08/2022 19:15:00 UTC
Last modified on: 11/09/2022 13:48:00 UTC