---
Introduction
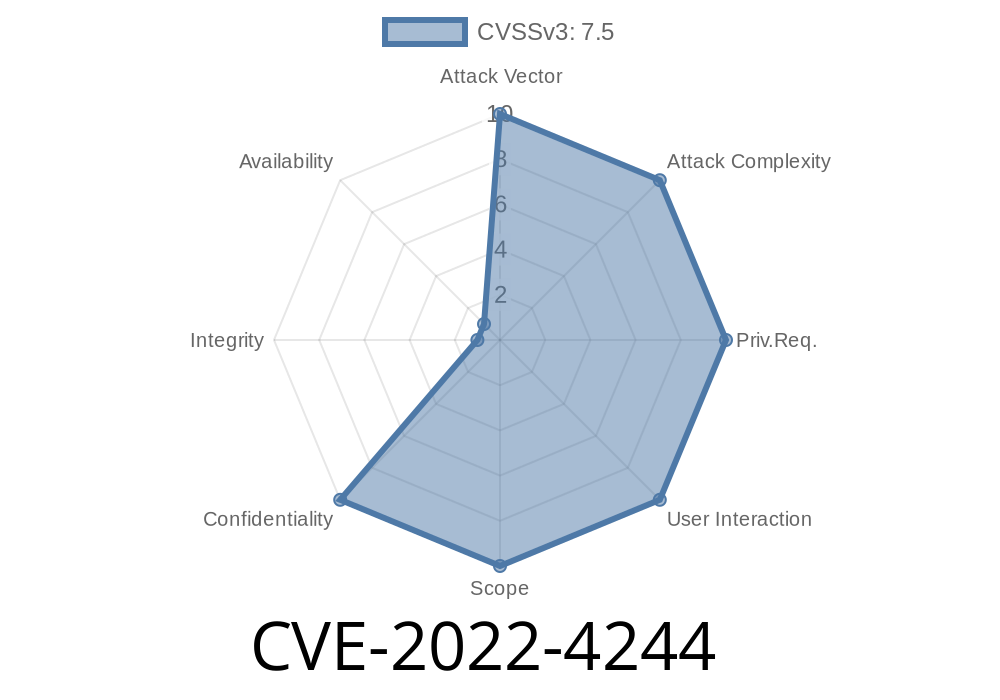
In 2022, a serious security flaw—CVE-2022-4244—was uncovered in the codeplex-codehaus project, a collection of open-source tools popular for software development and deployment. This flaw enables a *Directory Traversal* (a.k.a *Path Traversal*) attack, allowing hackers to access sensitive files on your system simply by tweaking a URL or a filename in a request.
In this post, we’ll break down how this vulnerability works, provide a simple code example highlighting the issue, share exploit details in plain language, and link you to original references for further reading.
What is Directory Traversal?
Directory Traversal is an attack vector that lets an attacker access files and directories that are intended to remain outside the web root folder. By inserting special character sequences like ../ (dot-dot-slash) in requests, attackers can "traverse" up and down the folder tree, potentially reaching configuration files, application source code, credentials, and even system files.
How CVE-2022-4244 Was Found in codeplex-codehaus
Researchers discovered that codeplex-codehaus did not properly sanitize file paths received from user input. If your application uses this package (or a vulnerable part of your own code), users might access unintended files. Here’s what the broken logic might look like in code:
Vulnerable Code Example (Java)
// BAD: Directly joins user input to file path!
String baseDir = "/srv/web/files/";
String requestedFile = request.getParameter("file"); // e.g., "../../etc/passwd"
File file = new File(baseDir + requestedFile);
// Reads the file and writes contents to response...
An attacker could send a request like
GET /download?file=../../../../etc/passwd
Instead of only being able to access files in /srv/web/files/, this input would resolve to /etc/passwd, leaking sensitive information.
Exploit Details (Step-by-step)
1. Find a Vulnerable Endpoint: Identify a download, file-view, or export feature in a web app using codeplex-codehaus or similar logic.
2. Supply Path Traversal Input: Modify the file parameter to include ../ sequences.
- For example: /download?file=../config/server.properties
3. Access Arbitrary Files: Keep adjusting the depth of the traversal until application allows you to access files outside the intended folder (you may reach /etc/passwd, application .env files, etc.).
4. Automate the Attack: Use tools like DirBuster, Burp Suite Intruder, or even simple curl/wget scripts to automate directory crawling.
Patch / How to Fix
Always sanitize user input. Instead of joining strings directly, use whitelists or built-in path resolution libraries:
Java Secure Example
String baseDir = "/srv/web/files/";
String requestedFile = request.getParameter("file");
// Canonicalize path and restrict access
File file = new File(baseDir, requestedFile).getCanonicalFile();
if (!file.getPath().startsWith(new File(baseDir).getCanonicalPath())) {
throw new SecurityException("Invalid file request");
}
Original References
- NVD: CVE-2022-4244
- OWASP Directory Traversal Cheat Sheet
- Mitre: CVE-2022-4244
Conclusion
CVE-2022-4244 is a critical bug in codeplex-codehaus that makes systems open to directory traversal attacks. If you use this package—or any user-supplied file path—check your code for potential path traversal. Fix it by properly sanitizing and validating all file paths against unauthorized access. For more info, follow the reference links above.
Timeline
Published on: 09/25/2023 20:15:00 UTC
Last modified on: 10/02/2023 19:28:00 UTC