When Apple releases security updates, it’s often easy to gloss over the technical details. But behind those little updates can be some pretty big bugs. In this exclusive deep dive, we'll break down CVE-2022-42789, a security flaw in macOS’s code signature validation. We’ll explain how it worked, why it was dangerous, show code snippets, point to useful references, and show what it means for your Mac’s security.
What Was CVE-2022-42789 All About?
Apple uses a system called code signing to make sure the apps running on your Mac really come from who they claim, and haven’t been secretly modified. This system is a big part of what makes macOS trustworthy.
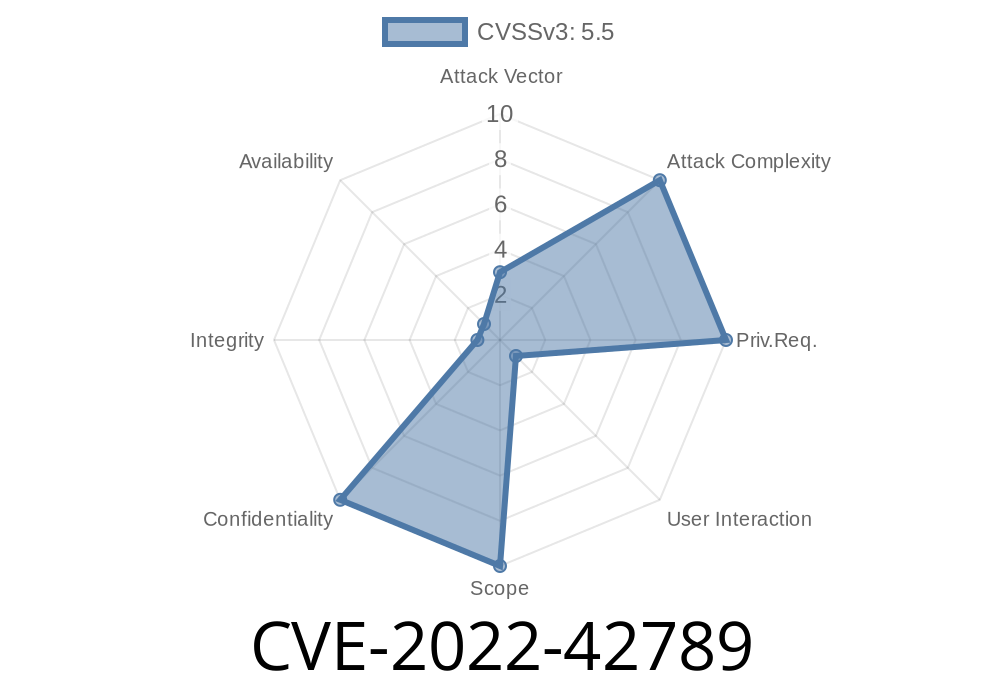
CVE-2022-42789 was a flaw in the way macOS checked these signatures. Because of a problem with how it verified code signatures, it was possible for a malicious app to sneak past some of these checks and, under the right conditions, access data it shouldn’t be able to.
If exploited, it could let a rival or rogue app poke around user-sensitive data, which is exactly what Apple wants to avoid.
macOS 11.7, 12.6, 13.
See Apple's advisory here:
https://support.apple.com/en-us/HT213445
Why Is Code Signature Validation So Important?
Let’s break it down simply:
When you download and run an app on your Mac, Apple’s Gatekeeper and system security checks look for a digital signature. This signature says, “the code in here hasn’t been tampered with since the developer shipped it.” If malware slips through, it usually means the code signing process got tricked or bypassed.
Where Was the Bug?
While Apple’s detailed code isn’t public, security researchers pieced together that this bug occurred in a function responsible for parsing and validating app signatures.
The bug allowed a malicious app to present a specially crafted file, or package, in a way that made the code appear correctly signed—even if it had been tampered with.
Example Exploit Scenario
Suppose an attacker crafts an *evil* app bundle that includes a valid signature for one part, but tucks malicious binaries somewhere deeper or in a confusing spot.
On vulnerable versions, the system might only check the signature of the “main app,” but not thoroughly check nested or linked files—allowing the malicious files to do their dirty work.
A simplified pseudo-snippet (not Apple's real code) might look like
bool validateSignature(const char* appPath) {
// Validate primary app binary signature
if (!checkCodeSignature(appPath)) {
return false;
}
// Problem: Doesn't recursively check all nested binaries/scripts!
return true;
}
A fixed version would recursively check every binary or script embedded in the bundle.
Hide extra components, like scripts or helper programs, inside the app bundle.
3. Trick macOS into launching these unsigned or tampered components, since the system check could be skipped or tricked.
Once running, these shady components could access files, keys, or sensitive user data that only “genuine” signed apps are supposed to reach.
Suppose an app bundle is structured to look like this
MyApp.app/
├── Contents/
│ ├── Info.plist
│ ├── MacOS/
│ │ ├── MyApp (signed)
│ │ └── sneakyHelper (modified, unsigned)
On a vulnerable system, opening MyApp.app could cause both MyApp and sneakyHelper to run—despite sneakyHelper being unsigned or tampered with.
You might see exploit code similar to this
codesign -s "Valid Dev ID" MyApp.app/Contents/MacOS/MyApp
# Don't sign sneakyHelper!
# Now, package the app
open MyApp.app
# sneakyHelper gets executed via a post-install script or helper
How Did Apple Fix It?
Apple improved checks so now, every component inside an app bundle must validate fully and recursively. Any tampered or unsigned binary, helper or script anywhere inside means the whole app gets rejected.
More References and Reading
- Apple Security Updates - CVE-2022-42789
- Understanding macOS Code Signing
- Amit Serper: "Breaking macOS code signing" *(not about this CVE but a good primer)*
Final Thoughts
CVE-2022-42789 is a stark reminder that the devil is in the details—especially when it comes to system security. Updating is your best defense, but understanding why helps you stay safer in the future. If you're running an older macOS version, patch up today!
*Feel free to share this breakdown or ask questions below!*
Timeline
Published on: 11/01/2022 20:15:00 UTC
Last modified on: 11/02/2022 19:12:00 UTC