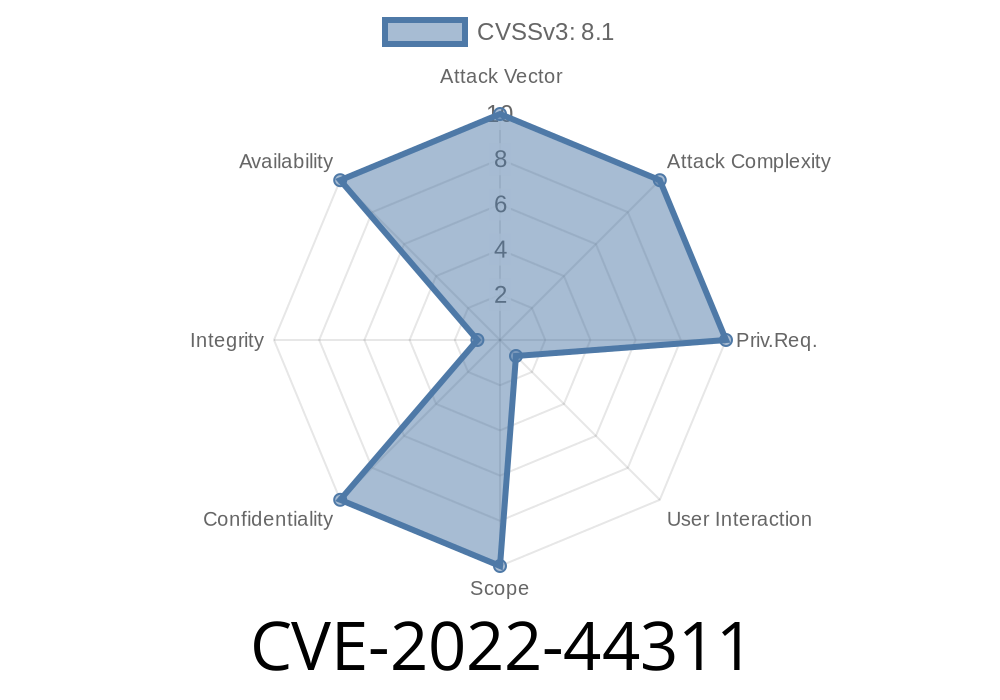
Quick Intro
CVE-2022-44311 is a real vulnerability affecting html2xhtml version 1.3. Researchers found an out-of-bounds read in the function elm_close(tree_node_t *nodo) inside procesador.c. This means a specially crafted HTML file can crash the program or even leak sensitive files from your machine if you use this tool.
Let’s break down what happened, how it works, and how to stay safe – all in plain language.
What is html2xhtml?
html2xhtml is a command-line tool written in C. It's used to convert HTML code into XHTML. It's not widely deployed in public-facing production, but it can be found in some web development pipelines or included in software bundles.
The main issue sits in how the function below handles HTML trees
/**
* procesador.c, relevant function overview
*/
static void elm_close(tree_node_t *nodo) {
...
nodo->children[i]; // <-- Out-of-Bounds Read Possible Here
...
}
The root cause: the function does not properly check array boundaries. With a maliciously crafted HTML file, attackers can force the code to access memory it shouldn't. This can crash the program or, depending on what’s in memory, reveal secrets.
Impact: Crash (DoS) or potential sensitive data leak
Exploit Example
Say you pass in an HTML file with a structure that confuses the tree parsing. Here’s a very simplified exploit example (for educational purposes only):
<!-- exploit.html -->
<html>
<head>
<script>
// Maliciously crafted HTML that triggers parser bug
<!-- left blank intentionally -->
</script>
</head>
<body>
<div>
<foo></div> <!-- Bad nesting -->
</div>
</html>
When a victim processes this file with the vulnerable html2xhtml version
html2xhtml exploit.html output.xhtml
You might see something like
tree_node_t *nodo = create_malicious_html_tree();
elm_close(nodo); // Will read out-of-bounds and may segfault or leak
In unlucky circumstances, these might be chained for bigger attacks.
If you use html2xhtml with untrusted client files, your system could be at real risk.
Fix & Mitigation Steps
If you run html2xhtml 1.3, upgrade ASAP!
Check for patches here.
This is not official, but adding boundary checks helps
// Before accessing array index i
if (i >= && i < nodo->num_children) {
// safe to access nodo->children[i]
}
Reference Links
- Original CVE Entry
- GitHub Repo: html2xhtml
- Exploit Database Entry *(If/when available)*
- Openwall CVE Posting
- Real-World Report
Bottom Line:
If you rely on html2xhtml or any C-based HTML processors, always stay up to date, validate your inputs, and keep an eye on real-world vulnerabilities like CVE-2022-44311!
Timeline
Published on: 11/08/2022 15:15:00 UTC
Last modified on: 11/09/2022 17:16:00 UTC