Adobe Acrobat Reader DC is one of the most widely used PDF readers globally. It’s found on millions of PCs, often used without much thought. Security of this software is critical — and in late 2022, a serious vulnerability was disclosed: CVE-2022-44514.
This post breaks down the vulnerability, shows how attackers can take control of a target computer, and provides you with everything you need to know to stay safe.
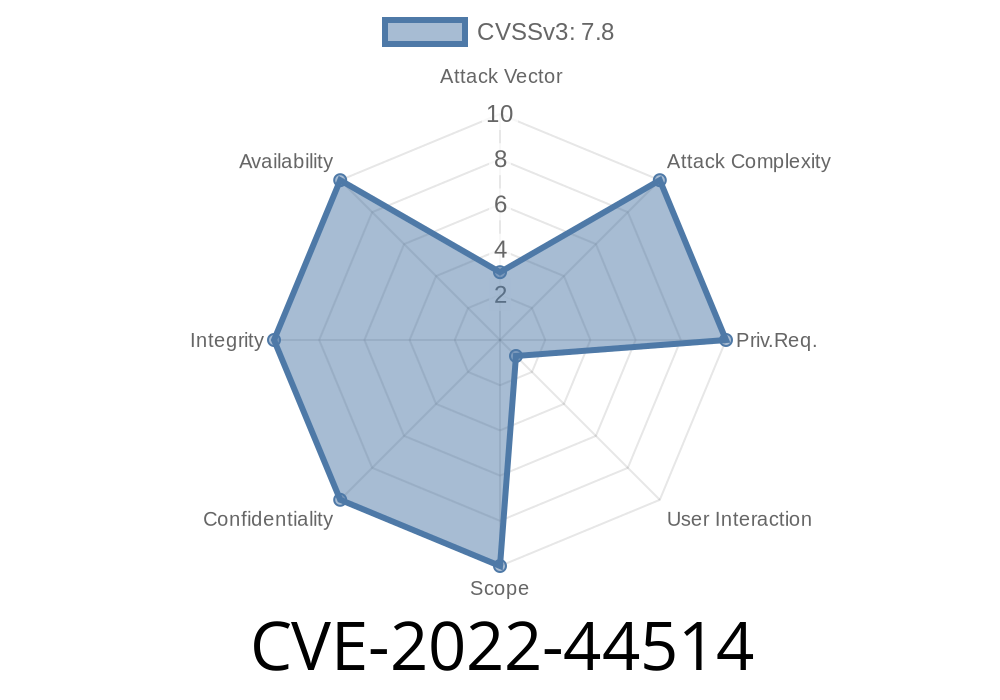
1. What is CVE-2022-44514?
CVE-2022-44514 is a use-after-free vulnerability found in multiple versions of Adobe Acrobat Reader DC:
17.012.30205 and earlier
A use-after-free bug happens when a program continues to use a piece of computer memory after it’s been "freed" — leading to unpredictable behavior. In many cases, attackers can trick the program into executing malicious code with all the rights of the logged-in user.
Original reference:
- Adobe Security Bulletin APSB22-55
- NVD Details: CVE-2022-44514
2. Impact and Risk
When exploited, this vulnerability allows arbitrary code execution. In plain English: attack code could fully control your PC with your permissions — read your files, install programs, or even spy on you.
Important: Exploitation _requires user interaction._ A victim must open a specially-crafted malicious PDF sent by an attacker, often through email or a download link.
Reusing freed memory space for attacker’s code.
Example Exploit Snippet (for educational purposes only!)
Attackers might create a PDF like the following (JavaScript inside PDF)
// Malicious JavaScript embedded in PDF
var tmpObj = this.getAnnots()[];
this.removeAnnot(tmpObj); // This frees the memory
// Use-after-free: tmpObj is now referencing freed space
app.alert(tmpObj.contents); // Accessing freed memory - triggers bug
An attacker might then fill that freed memory region with shellcode to get code execution, by filling the heap with a specially crafted byte pattern.
Adobe has patched this vulnerability!
- Download the latest Adobe Acrobat Reader DC
5. Dig Deeper: Resources and References
- Adobe Security Bulletin APSB22-55 (CVE-2022-44514)
- National Vulnerability Database: CVE-2022-44514
- Exploit DB Search for Acrobat Reader
- How to Disable JavaScript in Adobe Acrobat
6. Final Thoughts
CVE-2022-44514 is a dangerous bug, but only if you’re running an outdated version of Acrobat Reader DC and open a malicious file. Keep your software current, stay wary of unexpected attachments, and you’re much safer.
Vulnerabilities like these often go public in a few months, with exploit code following shortly after. Updating promptly is always your best defense!
Stay informed. Stay safe. If you have older coworkers or family members, let them know too!
*This analysis was created to help everyday users and IT staff understand and protect themselves against CVE-2022-44514. For defenders and technical enthusiasts, see the references above and follow security advisories for timely updates.*
Timeline
Published on: 12/19/2024 00:15:05 UTC