---
Summary:
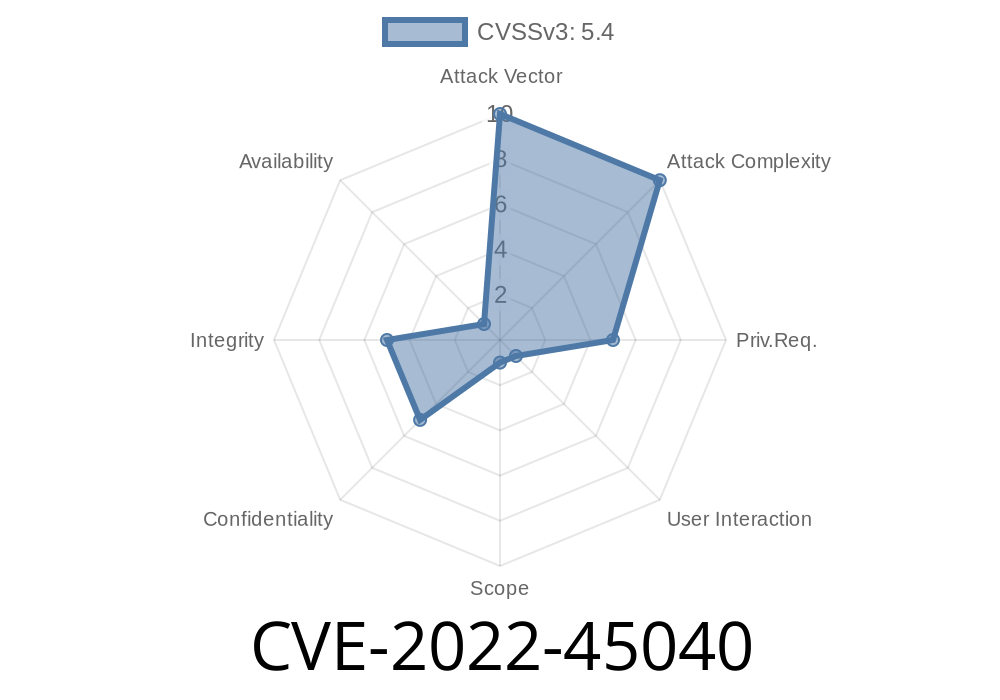
CVE-2022-45040 is a Cross-site Scripting (XSS) vulnerability discovered in WBCE CMS version 1.5.4. This flaw happens in the /admin/pages/sections_save.php file, letting attackers inject and execute malicious JavaScript or HTML by manipulating the "Name Section" input field.
What is WBCE CMS?
WBCE CMS is a simple, open-source content management system based on PHP and MySQL. It's popular for small to medium web projects, appreciated for its ease of use.
Where the Bug Lives
The critical vulnerability appears in the sections_save.php script, specifically when handling user-supplied input for the name of a section.
No proper sanitization or escaping is done before storing or displaying this field, opening the door for XSS payloads.
How Attackers Exploit It
An attacker simply needs to craft a special value for the “Name Section” field when editing or creating a new section. When an admin or user visits the affected page in the admin panel, the injected code executes in their browser.
In the “Name Section” input field, insert the following payload
"><script>alert('XSS - CVE-2022-45040')</script>
4. Submit the form.
Whenever the section is listed or edited again, any user (often an admin) viewing the page will trigger a popup alert. In a real attack, the injected script could steal cookies or perform actions with the victim’s session.
Here’s a simulated HTTP POST request exploiting the flaw
POST /admin/pages/sections_save.php HTTP/1.1
Host: target.com
Content-Type: application/x-www-form-urlencoded
Cookie: your_session_cookie
section_id=1337§ion_name=%22%3E%3Cscript%3Ealert('XSS'%3C%2Fscript%3E)&other_fields=...
Or, just use your browser’s developer tools to modify the value in the input box and submit it normally.
Malicious Actions: Perform actions as logged-in users without their consent.
Anyone with access to the “Name Section” field can plant an XSS. Even more dangerous if low-privileged users can add or edit sections.
## Fix / Solution
Patch:
Developers should escape or sanitize all input before displaying it. Use PHP’s htmlspecialchars() for outputting untrusted data.
Here’s how a fixed code snippet may look
// BAD: Direct output (vulnerable)
echo "<h1>" . $_POST['section_name'] . "</h1>";
// GOOD: Proper escaping (safe)
echo "<h1>" . htmlspecialchars($_POST['section_name'], ENT_QUOTES, 'UTF-8') . "</h1>";
Check with the latest WBCE CMS version for a patch:
https://forum.wbce.org/viewtopic.php?id=5697
References and More Reading
- WBCE CMS Official website
- VulDB Entry on CVE-2022-45040
- NVD CVE-2022-45040
Takeaway
CVE-2022-45040 was a straightforward yet dangerous XSS bug in WBCE CMS v1.5.4. It’s another reminder to always sanitize user input before sending it to browsers, especially in admin interfaces that control content.
If you’re running WBCE CMS, update immediately and check for other unescaped user input throughout your site!
Timeline
Published on: 11/25/2022 16:15:00 UTC
Last modified on: 11/28/2022 21:05:00 UTC