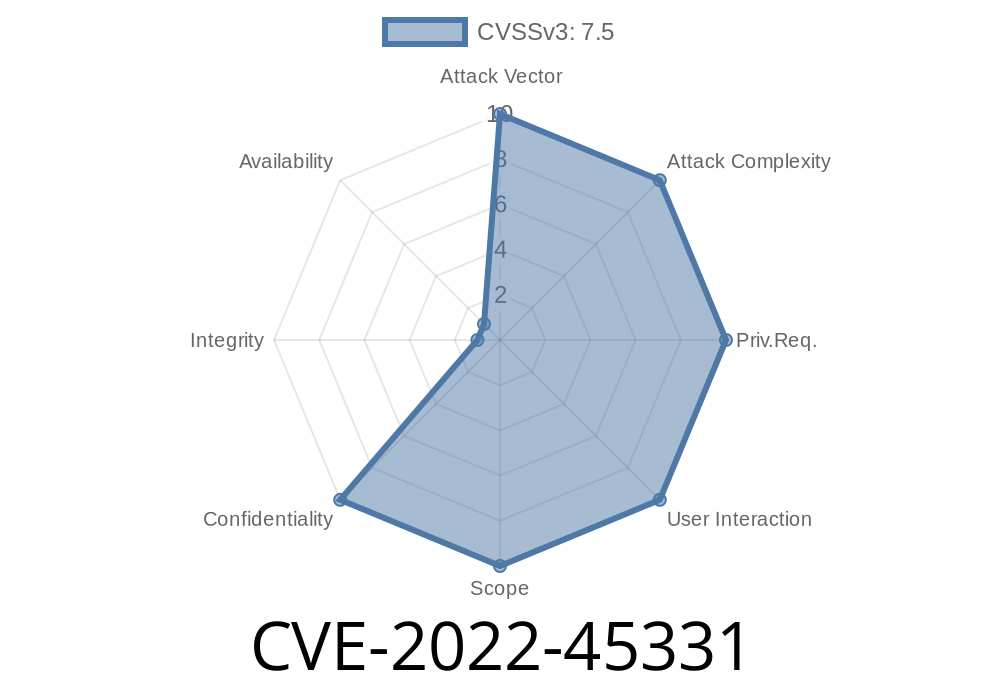
AeroCMS is a lightweight, open-source Content Management System (CMS) designed for simple websites and blogs. But in version ..1, a critical security hole was discovered: CVE-2022-45331. This issue could allow attackers to steal your database content or even take over your CMS.
Let’s dive deep into what was discovered, how the vulnerability works, what the code looks like, and ways you can protect your site.
What is CVE-2022-45331?
CVE-2022-45331 is a SQL Injection vulnerability found in AeroCMS v..1. The flaw lets attackers manipulate the p_id parameter in requests to /post.php, injecting unexpected SQL code. When your CMS’s backend processes the input, it’s tricked into executing malicious queries against your database.
References
- NVD Entry – CVE-2022-45331
- Exploit-DB: 51358
Suppose the /post.php page gets a URL parameter like this
http://example.com/post.php?p_id=1
Somewhere in post.php, you will find code similar to
// Insecure example
$p_id = $_GET['p_id'];
$query = "SELECT * FROM posts WHERE post_id = $p_id";
$result = mysqli_query($conn, $query);
The p_id comes straight from the user into the SQL command, without any sanitizing or escaping. This means an attacker can send anything as the p_id value, including their own SQL code!
Suppose an attacker visits
http://vulnerable-aerocms.com/post.php?p_id=1+OR+1=1
This turns the SQL into
SELECT * FROM posts WHERE post_id = 1 OR 1=1
Instead of just post #1, this shows *all* posts, because OR 1=1 is always true.
But it gets worse. Here’s a sample attack that reveals the current logged-in MySQL user
http://vulnerable-aerocms.com/post.php?p_id=1 UNION SELECT 1,user(),3,4,5,6,7--
A more advanced trick, revealing table names from the database
http://vulnerable-aerocms.com/post.php?p_id=1 UNION SELECT 1,table_name,3,4,5,6,7 FROM information_schema.tables--
Disclaimer: Never test on sites you don’t own.
How Can You Fix It?
Simple: Never trust user input in SQL. Use parameterized queries! Here’s the safe way, using prepared statements:
// SAFE VERSION with Prepared Statement
$p_id = $_GET['p_id'];
$stmt = $conn->prepare('SELECT * FROM posts WHERE post_id = ?');
$stmt->bind_param('i', $p_id); // 'i' means integer
$stmt->execute();
$result = $stmt->get_result();
This way, any weird input in p_id won’t affect your SQL command.
Summary Table
| | Insecure Example | Secure Example |
|-------------|---------------------------------------------------|------------------------------------------------|
| Vulnerable? | Yes | No |
| Query | SELECT * FROM posts WHERE post_id = $p_id | SELECT * FROM posts WHERE post_id = ? |
| Risk | SQL Injection: can reveal or dump table contents | None |
Final Thoughts
The discovery of CVE-2022-45331 is a wakeup call for every PHP developer: sanitize your inputs and use prepared statements! Even small projects like AeroCMS can be seriously compromised if good habits aren't followed from the start.
If you use AeroCMS v..1: update immediately or patch your PHP code manually.
Always monitor the National Vulnerability Database and Exploit-DB for news about the tools you use.
References
- CVE-2022-45331 @ NVD
- Exploit-DB: 51358
- OWASP SQL Injection
Stay safe! If you found this post helpful, share with your fellow developers.
Timeline
Published on: 11/22/2022 21:15:00 UTC
Last modified on: 11/23/2022 16:04:00 UTC