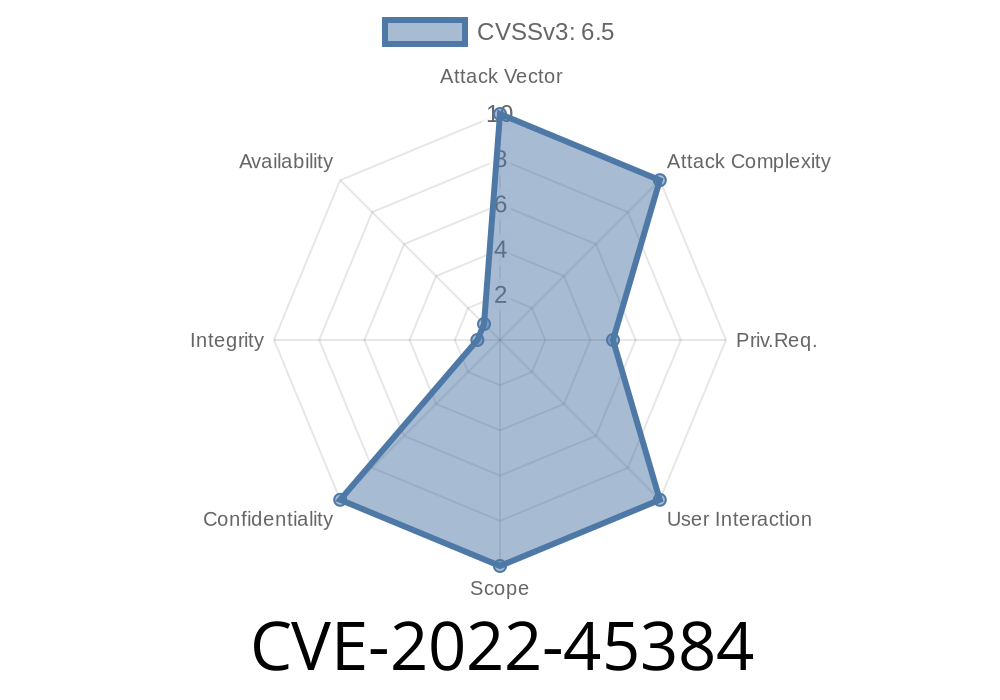
The world of software development thrives on automation. Jenkins, a popular automation server, is the backbone for many continuous integration and deployment pipelines. But what happens when the tools we trust open new doors for attackers? Today, we’re going to talk about a real vulnerability that puts sensitive credentials at risk: CVE-2022-45384.
What is CVE-2022-45384?
This vulnerability affects the Reverse Proxy Auth Plugin for Jenkins, specifically versions 1.7.3 and earlier. If you use this plugin alongside LDAP authentication for your Jenkins instance, your LDAP manager’s password could be stored _in clear text_ inside your Jenkins controller’s file system.
If an attacker or a rogue admin gets filesystem access, they can easily steal this password, jeopardizing not just Jenkins but your whole corporate directory.
Where’s the Problem?
The risky behavior happens in the Jenkins config file, config.xml. When you configure LDAP in the Reverse Proxy Auth plugin, it saves the manager’s password unencrypted in the global settings file. Even though Jenkins encrypts many credentials internally, in this scenario, the plugin didn’t use Jenkins’ credentials store or any encryption for the LDAP manager password.
Path to the vulnerable file
/var/lib/jenkins/config.xml
If anyone (malicious or by accident) can open this file, they’ll see the password in plain text.
Real-World Impact
Suppose you have a Jenkins server used by multiple projects, teams, or clients, and someone can get shell access to the Jenkins controller (for backup, maintenance, or debugging purposes). With just a quick search, they could get your directory admin password and use it for:
Show Me the Code
Here’s a snippet of what the sensitive part of config.xml might look like (with the password in PLAIN TEXT):
<jenkins.model.Jenkins>
...
<reverseProxyAuth>
<ldapManagerDN>cn=admin,dc=example,dc=com</ldapManagerDN>
<ldapManagerPassword>supersecretpassword</ldapManagerPassword>
...
</reverseProxyAuth>
...
</jenkins.model.Jenkins>
Even if you don’t use the plugin now, if this remains in config.xml, the password is still exposed.
Gain filesystem access (SSH, SFTP, a local terminal, or any method).
2. Locate your Jenkins home directory (commonly /var/lib/jenkins/ on Linux).
`bash
cat /var/lib/jenkins/config.xml | grep ldapManagerPassword
Imagine an attacker with compromised shell access on your Jenkins controller
cat /var/lib/jenkins/config.xml | grep ldapManagerPassword
# Output:
# <ldapManagerPassword>supersecretpassword</ldapManagerPassword>
With this value, they could run LDAP queries anywhere on your network
ldapsearch -x -D "cn=admin,dc=example,dc=com" -w supersecretpassword -b "dc=example,dc=com"
And instantly see or change directory contents.
1. Update the Plugin
The Reverse Proxy Auth Plugin maintainers fixed this problem in version 1.8. Upgrading is the single most effective fix.
- Upgrade instructions (official Jenkins plugin page)
- Changelog for v1.8
2. Use Encrypted Credentials
After upgrading, switch to using Jenkins’ built-in credentials store for LDAP manager passwords. This will encrypt sensitive information at rest.
3. Audit Your Configs
After upgrading, remove any leftover plain text passwords from config.xml. You may need to search for <ldapManagerPassword> tags.
4. Secure Jenkins Controller File System
Always restrict shell or file access on your Jenkins controller. Use strict permissions and monitor for unauthorized access.
Additional References
- Jenkins Security Advisory for CVE-2022-45384
- Reverse Proxy Auth Plugin on Jenkins Plugins Site
- Upgrading Jenkins plugins
Final Thoughts
CVE-2022-45384 is a classic example of “plaintext password” risk. Even if your network is tight and your Jenkins is secure, just one unsafe plugin can create a gap in your armor.
Lock down access to the Jenkins file system
If you have more questions about Jenkins security or need help locking down your pipeline, get in touch—or keep reading trusted sources like Jenkins’ own security advisories.
Timeline
Published on: 11/15/2022 20:15:00 UTC
Last modified on: 11/18/2022 17:04:00 UTC