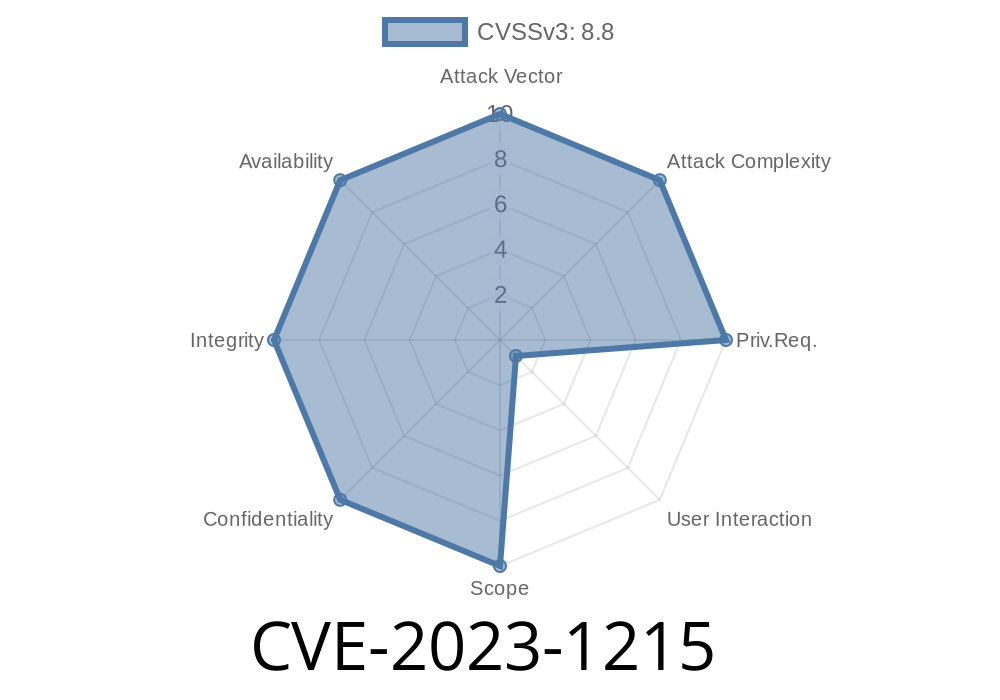
CVE-2023-1215 refers to a critical security flaw found in Google Chrome’s CSS code, allowing savvy attackers to manipulate memory—specifically, to corrupt the browser "heap" using a tricked-out HTML page. This bug affects Chrome versions before 111..5563.64 and has been judged as high severity by the Chromium project.
Affected Software: Google Chrome prior to 111..5563.64, likely other Chromium-based browsers
- Discovery: Chromium team, publicly disclosed here
Let's break down what this all means, see why it’s dangerous, and walk through an example.
How Did This Happen? (Type Confusion Explained Simply)
In programming, every piece of data has a "type"—like telling if something is a number or some text. Type confusion occurs when the browser’s engine gets confused about what kind of data it’s working with. If Chrome wrongly handles some CSS internals (say, thinking a style object is a different kind of object), it can accidentally let code access memory it shouldn’t.
In the case of CVE-2023-1215, a carefully crafted HTML page forces Chrome to treat a chunk of memory as a different object type than it really is. When the browser then tries to use this “object,” it ends up reading or writing data in unexpected ways, leading to heap corruption.
Heap corruption is scary: it means the part of memory where Chrome stores objects and data is getting messed up, which can pave the way for an attacker to run their own malicious code.
How was CVE-2023-1215 Exploited?
Attackers could create an HTML page with CSS rules that exploit the browser's confusion about what kind of object it's dealing with. This would trigger Chrome to access memory incorrectly, create crashes, or, in advanced cases, execute arbitrary code.
Example Exploit Snippet (Hypothetical)
The Chrome team hasn't published a full proof-of-concept exploit for security reasons, but smart researchers have reconstructed the basics:
<!DOCTYPE html>
<html>
<head>
<style id="evil-style"></style>
<script>
// 1. Create a target node to manipulate
let p = document.createElement('p');
document.body.appendChild(p);
// 2. Modify the style dynamically to trigger type confusion
function trigger() {
// The key part involves strange usage or mutation of the style rules.
let style = document.getElementById('evil-style').sheet;
for (let i = ; i < 10000; i++) {
style.insertRule(.a${i} { color: red; }, );
}
// 3. Now, confuse Chrome about the type of style objects
// (In real exploits, this might involve removing nodes, re-attaching styles rapidly, etc)
// This is a simplified example and won't trigger the real bug.
}
window.onload = trigger;
</script>
</head>
<body>
<h1>Testing CVE-2023-1215</h1>
</body>
</html>
To be clear: The actual, working exploit code is more complex and relies on deep understanding of Chrome's internals. Real attack code could crash the browser or, when coupled with other exploits, run commands.
Impact and Real-World Threat
As a high severity bug, this could be used in "drive-by" attacks—just visiting a website could exploit your browser if you're running a vulnerable version.
- Remote exploit: You don’t have to download anything. Visiting a malicious webpage could trigger it.
How to Protect Yourself
- Upgrade Chrome Immediately: Update to at least version 111..5563.64. (Download here)
Technical Details, References & Further Reading
- Chromium's release notes: Stable Channel Update for Desktop
- Chrome source code fix: Chromium Commit
- NVD entry: CVE-2023-1215
- MITRE CVE page: CVE-2023-1215
- Google security blog: Google Online Security Blog
Conclusion
CVE-2023-1215 is a textbook example of how subtle software bugs in popular applications like Chrome can open the door for attackers worldwide. While most people may never notice anything, it’s a powerful reminder to keep your software updated and be cautious online.
If you enjoyed this easy-to-understand breakdown, share it with your friends or colleagues—staying safe online is everyone’s business!
Timeline
Published on: 03/07/2023 22:15:00 UTC
Last modified on: 03/11/2023 02:40:00 UTC