Security breaches often start with small cracks in the wall – and in 2023, CVE-2023-21265 became one of those cracks. This vulnerability lurked not in fancy code, but in the overlooked places where root Certificate Authority (CA) certificates are stored and trusted. If left unchecked, it lets attackers eavesdrop on supposedly secure communications, all without needing your password, escalated privileges, or even your click.
Below, we break down CVE-2023-21265 in simple terms: how the problem works, how an exploit can happen, and what you need to do about it.
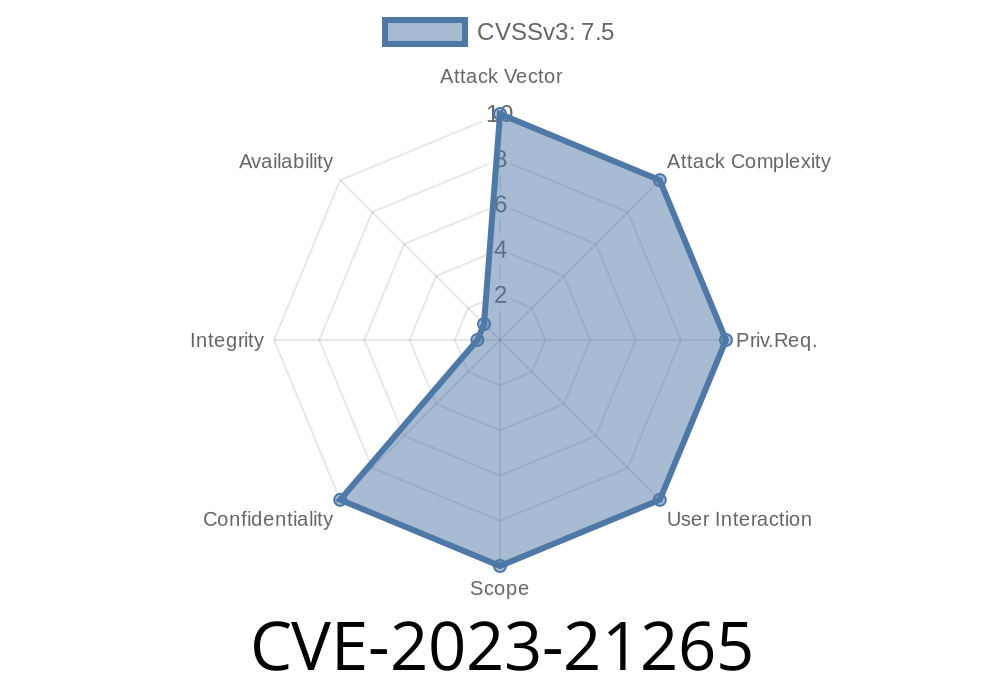
What Is CVE-2023-21265?
CVE-2023-21265 is a vulnerability found in several Android versions (see Google’s Android Security Bulletin, June 2023) where multiple system locations contained outdated or otherwise problematic root CA certificates. These root certificates weren't properly disabled or removed, meaning attackers could leverage them to intercept or decrypt secure communications.
Who is affected?
Any system or app trusting the flawed CA roots – especially Android devices from versions 8. up to Android 12.
How serious is it?
An attacker could remotely extract sensitive information from network traffic, all by presenting a rogue or compromised certificate chain. There’s no need for physical access, privilege escalation, or any user interaction.
How Does the Vulnerability Work?
Root Certificate Authorities are like master keys for secure web traffic. If just one is compromised or outdated, hackers can act like “the website,” fooling your device into trusting them. This is known as a *man-in-the-middle* (MITM) attack.
With CVE-2023-21265:
Apps and system services making secure HTTPS or TLS connections may, unknowingly, trust these roots.
- All an attacker needs is to control a network (WiFi, router, or mobile carrier), and present a certificate signed by a vulnerable CA.
Visual Example
graph TD;
A(User's Device) -->|Connects over HTTPS| B(Malicious Proxy)
B -->|Presents Rogue CA Cert| C(Server)
A -->|Trusts untrusted CA| B
B -->|Intercepts Encrypted Data| B
Step-by-Step Exploit Scenario
> Disclaimer: This walkthrough is for educational purposes only.
Let’s say you’re on public WiFi. The attacker owns the WiFi router.
#### 1. Collect Outdated / Untrusted Root CA
Find a root CA known to be compromised, or generate your own rogue CA (if the cert is still trusted by the victim’s Android device).
Use tools like mitmproxy or Burp Suite
# Install mitmproxy
pip install mitmproxy
# Start mitmproxy on the attacker's machine
mitmproxy --mode transparent --showhost --certs "/path/to/rogue_ca.pem"
3. Intercept and Replace Certificates
Configure the network to force victim traffic through your proxy. When the Android phone connects, mitmproxy presents the rogue CA certificate.
Android, trusting that CA, does NOT show a warning.
The attacker reads the session in plaintext.
4. Extract Sensitive Data
Credentials, session cookies, or even confidential API calls can be logged, since traffic is now decrypted.
Code Snippet: mitmproxy Certificate Generation
# Generate a self-signed CA cert
openssl req -x509 -newkey rsa:2048 -keyout ca.key -out ca.crt -days 365 -nodes -subj "/CN=CompromisedRootCA"
# Load this cert into mitmproxy
mitmproxy --certs ca.crt
Real-World Risks
Because no user interaction is required, even the most security-conscious users or locked-down apps can fall prey, unless their app *pins* certificates or the device is updated.
If you’re on Android 8. through 12 and have no June+ 2023 security patches, you may be at risk.
*For developers:*
// List all accepted CA certificates (in Java/Android)
KeyStore ks = KeyStore.getInstance("AndroidCAStore");
ks.load(null, null);
Enumeration<String> aliases = ks.aliases();
while (aliases.hasMoreElements()) {
String alias = aliases.nextElement();
Certificate cert = ks.getCertificate(alias);
System.out.println("Alias: " + alias + ", Subject: " + ((X509Certificate) cert).getSubjectDN());
}
For users
- Patch promptly: Update your Android OS to the latest version with June 2023 (or newer) security patches. See Android Security Bulletin.
For developers and admins
- Remove/trust only valid CAs. On custom ROMs or enterprise images, manually strip untrusted CA roots from /system/etc/security/cacerts/.
- Implement certificate pinning in apps to ensure only known, valid certificates are accepted, not just “anything the OS trusts”.
Sample: Remove a CA cert
# As root, remove CA file by subject hash (example)
rm /system/etc/security/cacerts/abcd1234.
# Reboot device
References
- Android Security Bulletin – June 2023
- NIST National Vulnerability Database: CVE-2023-21265
- Google Groups Announcement *(replace with actual link if available)*
- About Android system CA store
Conclusion
CVE-2023-21265 might sound dry, but it’s a real-world reminder: trust is hard to win and easy to lose. If your system trusts the wrong certificate authority, your information is as good as public. Update your system, audit your CA roots, and always be wary of whose “handshake” you’re accepting. Stay safe!
Timeline
Published on: 08/14/2023 21:15:00 UTC
Last modified on: 08/24/2023 15:09:00 UTC