On April 18, 2023, Oracle released its quarterly Critical Patch Update, which included the disclosure of CVE-2023-21937, a security flaw impacting both Oracle Java SE and Oracle GraalVM Enterprise Edition. This networking component vulnerability, while classified as "difficult to exploit," deserves closer scrutiny for organizations and developers who depend on Java in environments where untrusted code may run—especially in scenarios like Java Web Start or applets.
In this exclusive deep dive, we'll break down what this CVE means, the risks involved, code-level details, how it might be exploited, and what steps you should take to mitigate your risk.
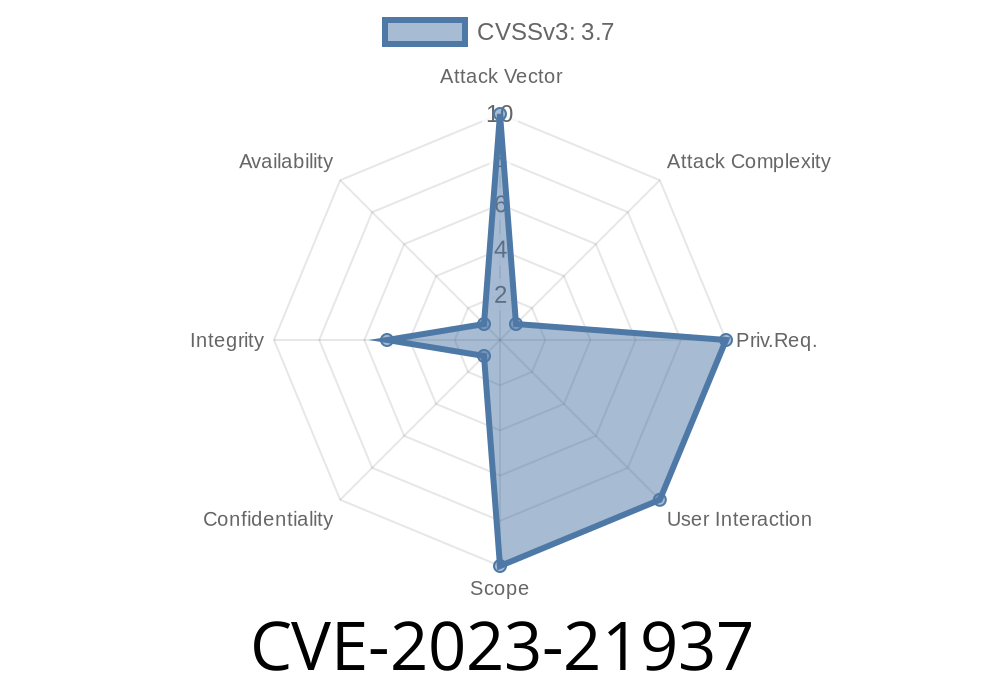
CVE: CVE-2023-21937
- Impacts: Oracle Java SE (8u361, 8u361-perf, 11..18, 17..6, 20), GraalVM EE (20.3.9, 21.3.5, 22.3.1)
Impact: Unauthorized update, insert, or delete of some data
- Who’s at risk: Java applications running untrusted code (e.g., through Web Start, applets, exposed APIs)
What is CVE-2023-21937?
This flaw resides in the networking component of affected Java SE and GraalVM EE versions. Specifically, code that loads and runs untrusted scripts coming from unverified sources, such as the internet, is at risk if it assumes the Java sandbox offers sufficient protection.
In most modern usage, browser-based Java applets are rare, but systems using Java Web Start, internal applications allowing users to run 3rd party code, or APIs that accept data (and might pass it through to vulnerable networking components) can be affected.
Quote from Oracle Original Advisory
> “Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Java SE, Oracle GraalVM Enterprise Edition accessible data.”
Scope: Unchanged (attacker stays in the same context)
- Impact: Integrity low (modification of data possible); no confidentiality or availability impact
> Real-World Risk: While the exploit is tricky, if someone can send the right data to a vulnerable Java runtime—such as via running a crafted Java Web Start applet, or via a Java API that processes arbitrary data—they could cause unauthorized changes to accessible data in the Java process.
You are running the listed Java SE or GraalVM EE versions.
- You allow untrusted code execution (for example, via applets, Java Web Start, or through APIs that pass external data into Java’s networking classes).
Potential Exploitation – What Would Attack Look Like?
Imagine you have a Java Web Start application that connects to your secure backend and, via untrusted code, parses network data using Java's networking APIs. An attacker might craft a malicious script or network message, causing the application to insert, update or delete sensitive application data it should not have access to.
Let’s say a public web service parses input with a Java networking library
import java.net.Socket;
public class DataHandler {
public void processInput(String host, int port, byte[] payload) throws IOException {
try (Socket s = new Socket(host, port)) {
s.getOutputStream().write(payload);
// Vulnerable code processing response here...
}
}
}
*If an attacker influences host, port, and payload, and the Java environment is outdated and vulnerable, the attacker could leverage CVE-2023-21937 to alter backend data.*
What Did Oracle Patch?
As Oracle keeps specifics close in the interest of security, public details are scarce. However, based on the description and components, the problem relates to how Java’s networking stack validates and enforces access or data manipulation—especially with data coming from untrusted sources.
Untrusted input is passed to a networking API.
- Due to the flaw, code running in a Java “sandbox” might be able to bypass intended controls, leading to data modification.
Lack of isolation between trusted and untrusted input.
- Insufficient validation—allowing privileged operations when sandboxing was supposed to prevent them.
Proof-of-Concept: What Could a Basic Attack Look Like?
NOTE: As an integrity-only bug with high complexity, a full working exploit isn’t public. However, for educational purposes, here’s a skeleton for how one might attempt exploitation _if_ more technical details were available.
Pseudocode
public class ExploitCVE21937 extends Applet {
public void start() {
try {
// Attempt to exploit the networking bug
Socket malicious = new Socket("targetserver.com", 9999);
OutputStream os = malicious.getOutputStream();
// Crafted payload exploiting malformed protocol interaction
byte[] exploitPayload = {/* malicious bytes */};
os.write(exploitPayload);
os.flush();
// Observe for unauthorized data changes
} catch (Exception e) {
e.printStackTrace();
}
}
}
> Disclaimer: This is not a working exploit, but a reference for how such attacks may be delivered: through untrusted applets or apps sending malicious networking payloads.
Upgrade to the fixed Java versions (the April 2023 CPU or later).
- Oracle JDK Downloads
- GraalVM Downloads
Avoid Deprecated Technologies:
Consider moving off Java applets and Web Start, which are both deprecated and increasingly a security risk.
References
- Oracle Critical Patch Update Advisory - April 2023
- National Vulnerability Database Entry: CVE-2023-21937
- Oracle Java SE Risk Matrix
- GraalVM Enterprise Edition Risk Matrix
Conclusion
CVE-2023-21937 may have a "low" integrity rating and is tough to exploit, but it serves as a reminder that even mature, maintained technologies like Java can harbor hidden dangers—especially when running code from less trustworthy sources. Apply patches early, audit where you ingest user input, and stay away from running untrusted Java where possible.
Stay safe, and patch your systems!
Author:
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC