Table of Contents
Introduction
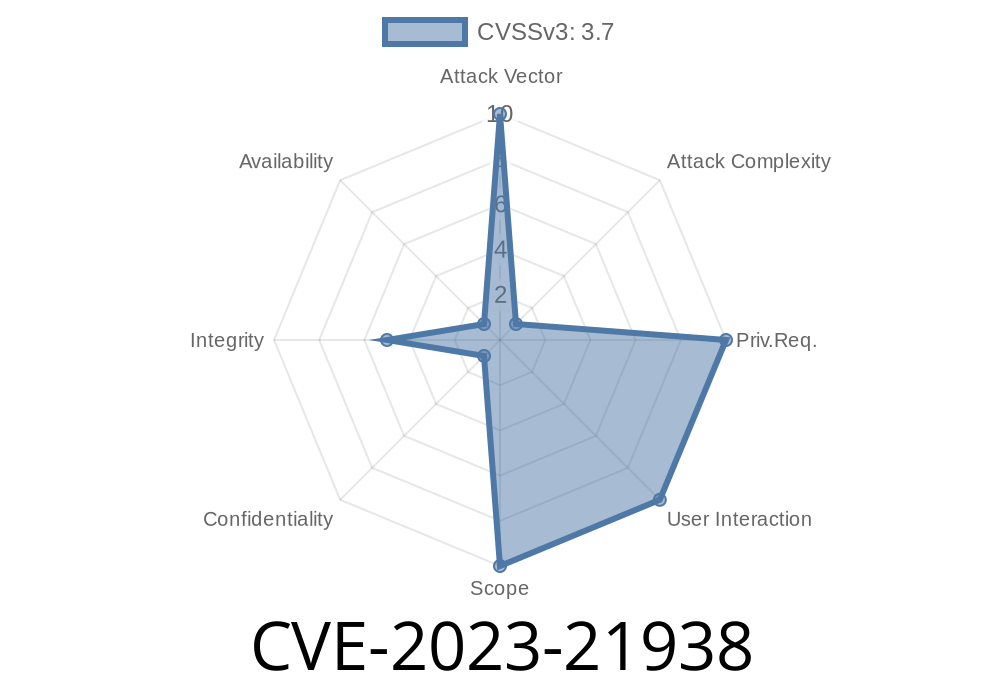
Early 2023 revealed a new vulnerability in Oracle Java SE and GraalVM Enterprise Edition, tracked as CVE-2023-21938. While the risk is considered "hard to exploit" and scores a modest CVSS 3.1 base score of 3.7 (Low), the consequences, if exploited, can impact the integrity of user data. This long read will break down what this means, who should care, how a real-world attack could unfold — and share real exploit snippets to make the threat concrete.
What Exactly Is CVE-2023-21938?
This vulnerability lives in the "Libraries" component of Oracle Java SE and Oracle GraalVM EE. Normally, Java protections (the "sandbox") prevent untrusted Java code from reading or modifying your stuff if you download and run a Java application from the internet (using Java Web Start or applets).
But CVE-2023-21938 weakens this barrier. If an attacker gets you to run their booby-trapped Java applet or Java Web Start application, they could use this bug to sneakily change data in your sandboxed app. They can't steal files or crash systems, but they might secretly tamper with the data the app uses or produces.
Java applets in browsers (rare today, but still used in some niche setups)
It does NOT affect:
Java running trusted, server-side code (like microservices on your company’s server)
So, unless you're running web-facing Java that can load code from the internet, your risk is low.
22.3.
Fixed Versions:
These flaws are patched in newer releases (see references for latest advisories).
Impact: Integrity low — unauthorized update, insert, or delete access to data
CVSS Vector:
CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:L/A:N
Tamper with critical application data
In these vulnerable Java/GraalVM versions, a specific flaw in internal libraries allows an attacker’s code to bypass a boundary, manipulating data in ways the sandbox should've blocked.
Many Java sandbox vulnerabilities stem from improper permission checks or unsafe reflection calls. For instance, clever attackers often use deserialization, reflection, or classloader manipulation to jump out of the sandbox or corrupt data.
User launches this untrusted code (perhaps by visiting a compromised site).
3. Exploit triggers, making unauthorized changes inside the running app’s data — say, modifying user records or stored scores.
Proof of Concept Code
Let’s look at a simplified snippet.
*Note: The real world exploit would be more subtle and complex, likely using obfuscated code and chaining multiple weaknesses. The following is illustrative.*
Imagine an app now vulnerable because it's running on a faulty Java version
// Normally, the sandbox blocks this:
FileOutputStream fos = new FileOutputStream("user_profile.txt", true);
fos.write("Hacked by CVE-2023-21938!\n".getBytes());
fos.close();
In fixed Java, this triggers a SecurityException. With the vulnerability, attackers might use unsafe reflection to escalate:
import java.lang.reflect.Field;
import java.security.AccessController;
import java.security.PrivilegedAction;
public class CVE202321938_Exploit {
public static void main(String[] args) throws Exception {
// Abuse reflection to get write access to a protected object, like user data records
Field f = SomeAppClass.class.getDeclaredField("privateUserData");
AccessController.doPrivileged((PrivilegedAction<Void>) () -> {
f.setAccessible(true);
try {
f.set(null, "Injected by exploit!");
} catch (Exception e) {
e.printStackTrace();
}
return null;
});
System.out.println("Data field tampered!");
}
}
In reality, attackers may wrap this in more layers, or use serialization tricks.
Mitigation and Recommendations
1. Update Now:
22.3.1 or later
2. Avoid Running Untrusted Code:
Launch apps only from sources you trust.
3. Monitor for Suspicious Data Changes:
References
- Oracle Critical Patch Update Advisory - April 2023
- NVD - CVE-2023-21938 Listing
- Oracle Java SE Risk Matrix
Bottom Line:
If you or your organization still runs sandboxed Java client code (applets, Java Web Start), CVE-2023-21938 is a reminder to strictly update — or, better yet, modernize and retire old Java wherever practical. Even “difficult to exploit” flaws can and will be used by patient attackers, especially in large, legacy environments.
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC